MPLS QoS - Lyle School of Engineering
... inside a Label Switched Path – Induced MPLS Graph • Analogous to a virtual topology in an overlay model • Logically mapped onto the physical network • Set of LSRs as nodes of the graph • Set of LSPs providing logical point to point connectivity between LSRs as edges SMU ...
... inside a Label Switched Path – Induced MPLS Graph • Analogous to a virtual topology in an overlay model • Logically mapped onto the physical network • Set of LSRs as nodes of the graph • Set of LSPs providing logical point to point connectivity between LSRs as edges SMU ...
"Resilient Overlay Networks"
... which allows the Internet to scale to millions of networks. This wide-area routing scalability comes at the cost of reduced fault-tolerance of end-to-end communication between Internet hosts. This cost arises because BGP hides many topological details in the interests of scalability and policy enfor ...
... which allows the Internet to scale to millions of networks. This wide-area routing scalability comes at the cost of reduced fault-tolerance of end-to-end communication between Internet hosts. This cost arises because BGP hides many topological details in the interests of scalability and policy enfor ...
L_06_ch_13_DLL_LAN_Ethernet
... The 10-Mbps capacity in each segment is now shared between 6 stations (actually 7 because the bridge acts as a station in each segment), not 12 stations. In a network with a heavy load, each station theoretically is offered 10/6 Mbps instead of 10/12 Mbps, assuming that the traffic is not going thro ...
... The 10-Mbps capacity in each segment is now shared between 6 stations (actually 7 because the bridge acts as a station in each segment), not 12 stations. In a network with a heavy load, each station theoretically is offered 10/6 Mbps instead of 10/12 Mbps, assuming that the traffic is not going thro ...
29414-d10
... This Technical Specification has been produced by the 3rd Generation Partnership Project (3GPP). The contents of the present document are subject to continuing work within the TSG and may change following formal TSG approval. Should the TSG modify the contents of the present document, it will be re- ...
... This Technical Specification has been produced by the 3rd Generation Partnership Project (3GPP). The contents of the present document are subject to continuing work within the TSG and may change following formal TSG approval. Should the TSG modify the contents of the present document, it will be re- ...
Link Layer
... encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! ...
... encapsulate datagram into frame, adding header, trailer channel access if shared medium “MAC” addresses used in frame headers to identify source, dest • different from IP address! ...
Chapter 6: The Transport Layer
... Minimize context switches Minimize copying You can buy more bandwidth but not lower delay Avoiding congestion is better than recovering from it – Avoid timeouts ...
... Minimize context switches Minimize copying You can buy more bandwidth but not lower delay Avoiding congestion is better than recovering from it – Avoid timeouts ...
TCP Fairness Issues
... – ECN must be supported by both TCP senders and receivers. – ECN-compliant TCP senders initiate their congestion avoidance algorithm after receiving marked ACK packets from the TCP receiver – A RED extension that marks packets to signal congestion ...
... – ECN must be supported by both TCP senders and receivers. – ECN-compliant TCP senders initiate their congestion avoidance algorithm after receiving marked ACK packets from the TCP receiver – A RED extension that marks packets to signal congestion ...
the document - Support
... The encryption algorithms DES/3DES/SKIPJACK/RC2/RSA (RSA-1024 or lower)/MD2/MD4/MD5 (in digital signature scenarios and password encryption)/SHA1 (in digital signature scenarios) have a low security, which may bring security risks. If protocols allowed, using more secure encryption algorithms, such ...
... The encryption algorithms DES/3DES/SKIPJACK/RC2/RSA (RSA-1024 or lower)/MD2/MD4/MD5 (in digital signature scenarios and password encryption)/SHA1 (in digital signature scenarios) have a low security, which may bring security risks. If protocols allowed, using more secure encryption algorithms, such ...
IP address.
... request to TCP layer asking for setting up a TCP connection, and the TCP connection between the PC and the server has been established . The http client then passes http request message (such as GET /….) to TCP layer. ...
... request to TCP layer asking for setting up a TCP connection, and the TCP connection between the PC and the server has been established . The http client then passes http request message (such as GET /….) to TCP layer. ...
Resilient Overlay Networks Abstract MIT Laboratory for Computer Science
... which allows the Internet to scale to millions of networks. This wide-area routing scalability comes at the cost of reduced fault-tolerance of end-to-end communication between Internet hosts. This cost arises because BGP hides many topological details in the interests of scalability and policy enfor ...
... which allows the Internet to scale to millions of networks. This wide-area routing scalability comes at the cost of reduced fault-tolerance of end-to-end communication between Internet hosts. This cost arises because BGP hides many topological details in the interests of scalability and policy enfor ...
Multicast Routing
... • Senders unicast their packets toward the core. • When the unicast packet reaches a member of the delivery tree, the packet is multicast to all outgoing interfaces that are part of the tree. Ahmed Helmy - UF ...
... • Senders unicast their packets toward the core. • When the unicast packet reaches a member of the delivery tree, the packet is multicast to all outgoing interfaces that are part of the tree. Ahmed Helmy - UF ...
Network Performance Definitions & Analysis
... Occur due to the fact that buffers are not infinite in size ...
... Occur due to the fact that buffers are not infinite in size ...
third edition
... and to see the big picture of networking. It is our experience that both students and professionals learning about networks for the first time often have the impression that network protocols are some sort of edict handed down from on high, and that their job is to learn as many TLAs (three-letter a ...
... and to see the big picture of networking. It is our experience that both students and professionals learning about networks for the first time often have the impression that network protocols are some sort of edict handed down from on high, and that their job is to learn as many TLAs (three-letter a ...
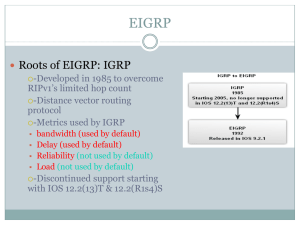
EIGRP
... a route becomes unavailable, DUAL will search its topology table for a valid backup path. • If one exists, that route is immediately entered into the routing table. • If one does not exist, DUAL performs a network discovery process to see if there happens to be a backup path that did not meet the re ...
... a route becomes unavailable, DUAL will search its topology table for a valid backup path. • If one exists, that route is immediately entered into the routing table. • If one does not exist, DUAL performs a network discovery process to see if there happens to be a backup path that did not meet the re ...
Computer Networking : Principles, Protocols and Practice Release
... • the Physical layer service may deliver more bits to the receiver than the bits sent by the sender • the Physical layer service may deliver fewer bits to the receiver than the bits sent by the sender Many other types of encodings have been defined to transmit information over an electrical cable. A ...
... • the Physical layer service may deliver more bits to the receiver than the bits sent by the sender • the Physical layer service may deliver fewer bits to the receiver than the bits sent by the sender Many other types of encodings have been defined to transmit information over an electrical cable. A ...
module10b
... • Router ID: Each OSPF router needs to have an unique ID which is the highest IP • address on any active interface. More about this later. • Hello / Dead Interval: Every X seconds we are going to send a hello packet, if we don’t hear any hello packets from our network for X seconds we declare you “d ...
... • Router ID: Each OSPF router needs to have an unique ID which is the highest IP • address on any active interface. More about this later. • Hello / Dead Interval: Every X seconds we are going to send a hello packet, if we don’t hear any hello packets from our network for X seconds we declare you “d ...
chapter5
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
Finish old component
... Partial ordering of high-level reconfiguration phases Preliminary partial ordering of NeCoMan’s reconfiguration actions Partial ordering of NeCoMan’s reconfiguration actions ...
... Partial ordering of high-level reconfiguration phases Preliminary partial ordering of NeCoMan’s reconfiguration actions Partial ordering of NeCoMan’s reconfiguration actions ...
HULA: Scalable Load Balancing Using Programmable Data Planes Naga Katta , Mukesh Hira
... have been designed to reduce the number of entries using compression techniques that exploit symmetry in the network. However, since these techniques rely on the control plane to update and compress the forwarding entries, they are slow to react to failures and topology asymmetry, which are common i ...
... have been designed to reduce the number of entries using compression techniques that exploit symmetry in the network. However, since these techniques rely on the control plane to update and compress the forwarding entries, they are slow to react to failures and topology asymmetry, which are common i ...