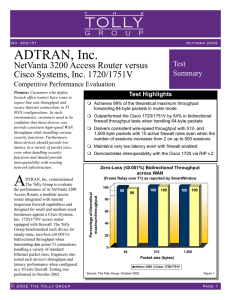
Timing is everything: Accurate, Minimum-cost, Available Bandwidth Estimation in High-speed Wired Network
... /I/ characters as well as data characters of the cross traffic packets, but the measurement will still be exact (i.e. /I/ and data characters represent time with sub-nanosecond precision). This level of access from software is unprecedented. Traditionally, however, an end host may timestamp packets ...
... /I/ characters as well as data characters of the cross traffic packets, but the measurement will still be exact (i.e. /I/ and data characters represent time with sub-nanosecond precision). This level of access from software is unprecedented. Traditionally, however, an end host may timestamp packets ...
Timing is Everything: Accurate, Minimum Overhead, Available Bandwidth Estimation in High-speed Wired Networks
... is important [17, 43, 45]. It is necessary for designing high performant networked systems, improving network protocols, building distributed systems, and improving application performance. The problems associated with available bandwidth estimation stem from a simple concept: Send a train of probe ...
... is important [17, 43, 45]. It is necessary for designing high performant networked systems, improving network protocols, building distributed systems, and improving application performance. The problems associated with available bandwidth estimation stem from a simple concept: Send a train of probe ...
Smart Dust and TinyOS: Hardware and Software for Network
... – Frequency of time-synch protocol communication increases with required accuracy and with variations in clocks. – If you lose synch, it is hard to regain it because you don’t know when the node is listening. You must transmit continuously or wait for it to go into a watchdog full listen. ...
... – Frequency of time-synch protocol communication increases with required accuracy and with variations in clocks. – If you lose synch, it is hard to regain it because you don’t know when the node is listening. You must transmit continuously or wait for it to go into a watchdog full listen. ...
overview of the project
... Almost all IDS are signature based, also known as knowledge based. Signature based IDS monitor network traffic and analyzes this traffic against specific predefined attacks. When an attack is detected an alarm is generated. This means that any traffic that doesn’t specifically match a signature is c ...
... Almost all IDS are signature based, also known as knowledge based. Signature based IDS monitor network traffic and analyzes this traffic against specific predefined attacks. When an attack is detected an alarm is generated. This means that any traffic that doesn’t specifically match a signature is c ...
cs240-yhe-measurements
... • Recursive probing to identify the path • Send three packets at a time ...
... • Recursive probing to identify the path • Send three packets at a time ...
3rd Edition: Chapter 4
... UDP segment eventually arrives at destination host Destination returns ICMP “host unreachable” packet (type 3, code 3) When source gets this ICMP, stops. ...
... UDP segment eventually arrives at destination host Destination returns ICMP “host unreachable” packet (type 3, code 3) When source gets this ICMP, stops. ...
Chapter 26 PPT
... • First, protocol details must be chosen carefully – Small design errors can result in incorrect operation, unnecessary packets, or delays – For example, if sequence numbers are used, each packet must contain a sequence number in the packet header – The field must be large enough so sequence numbers ...
... • First, protocol details must be chosen carefully – Small design errors can result in incorrect operation, unnecessary packets, or delays – For example, if sequence numbers are used, each packet must contain a sequence number in the packet header – The field must be large enough so sequence numbers ...
Taxonomy of IP Traceback - College of Engineering and Computing
... the companies experienced DoS attack; while in 2005 the number tumbled down to a meager 50 %. This is a good indicator of the development of security schemes. With the wide deployment of traceback schemes and intrusion detection systems; comprehensive security architecture can be envisioned that wou ...
... the companies experienced DoS attack; while in 2005 the number tumbled down to a meager 50 %. This is a good indicator of the development of security schemes. With the wide deployment of traceback schemes and intrusion detection systems; comprehensive security architecture can be envisioned that wou ...
PDF
... before decoding, then the receiver can exploit these predictions to identify the correct coding path, reducing decoding errors. Tab. 2 shows an example. We compare the costs of the correct path (PATH-1) and a faulty path (PATH-2). Due to the large amount of errors in received codeword sequence, a co ...
... before decoding, then the receiver can exploit these predictions to identify the correct coding path, reducing decoding errors. Tab. 2 shows an example. We compare the costs of the correct path (PATH-1) and a faulty path (PATH-2). Due to the large amount of errors in received codeword sequence, a co ...
Magnum Network Software – DX
... in the IP stack. A packet may be sent to a waiting DX application process or it may be passed to a different IP interface for transmission. Packets sent by DX application processes are also first passed to this stage to determine the appropriate output interface. NAT OUT This is the DX NAT Output st ...
... in the IP stack. A packet may be sent to a waiting DX application process or it may be passed to a different IP interface for transmission. Packets sent by DX application processes are also first passed to this stage to determine the appropriate output interface. NAT OUT This is the DX NAT Output st ...
3/11
... If an attacker runs a Sniffer on one system on LAN, he can gather data sent to and from any other system on the LAN Majority of the Sniffer tools are well suited to sniff data in a hub environment These tools are called passive sniffers as they passively wait for the data to be sent to them, silentl ...
... If an attacker runs a Sniffer on one system on LAN, he can gather data sent to and from any other system on the LAN Majority of the Sniffer tools are well suited to sniff data in a hub environment These tools are called passive sniffers as they passively wait for the data to be sent to them, silentl ...
$doc.title
... needed for the communication so that the illusion of a dedicated link is provided. The teardown phase is needed to release any reserved resources. A common (but not the only) way to implement circuit switching is using time-division multiplexing (TDM), also known as isochronous transmission. Here, t ...
... needed for the communication so that the illusion of a dedicated link is provided. The teardown phase is needed to release any reserved resources. A common (but not the only) way to implement circuit switching is using time-division multiplexing (TDM), also known as isochronous transmission. Here, t ...
pptx
... DarkC.Boot -> MainC; DarkC.Leds -> LedsC; DarkC.TheftTimer -> Ttimer; DarkC.Light -> PhotoC; ...
... DarkC.Boot -> MainC; DarkC.Leds -> LedsC; DarkC.TheftTimer -> Ttimer; DarkC.Light -> PhotoC; ...
The Internet Underwater: An IP-compatible Protocol Stack for Commercial Undersea Modems
... isting networks based on the TCP/IP architecture. A similar situation was also experienced by wireless sensor networks, until IPv6 over Low power Wireless Personal Area Networks (6LoWPAN) [2] became part of the Internet suite of standardized protocols. It is now essential to design, deploy, and test ...
... isting networks based on the TCP/IP architecture. A similar situation was also experienced by wireless sensor networks, until IPv6 over Low power Wireless Personal Area Networks (6LoWPAN) [2] became part of the Internet suite of standardized protocols. It is now essential to design, deploy, and test ...
PPT Version
... Stop transmitting before transport detects loss? Based on unauthenticated notification? NO! Notification had to be advisory – add complexity SCTP interest for switchover – if they could trust it ...
... Stop transmitting before transport detects loss? Based on unauthenticated notification? NO! Notification had to be advisory – add complexity SCTP interest for switchover – if they could trust it ...
ppt - Courses
... system (AS), is a collection of IP networks and routers, usually under the control of a single administrative entity, that presents a common routing policy to the ...
... system (AS), is a collection of IP networks and routers, usually under the control of a single administrative entity, that presents a common routing policy to the ...