05 LAES presentation
... Call-identifying information "dialing" or signaling which identifies the destination, direction, origin or termination of each communication generated or received by a subscriber by means of any equipment, facility, or service of a TSP Call content actual voice or, for data, the payload ...
... Call-identifying information "dialing" or signaling which identifies the destination, direction, origin or termination of each communication generated or received by a subscriber by means of any equipment, facility, or service of a TSP Call content actual voice or, for data, the payload ...
The Internet and the World Wide Web
... Provides a “virtual circuit” between two computers. Defines a port HTTP: 80, IRC 194) Guarantees reliable and in-order delivery of packets. ...
... Provides a “virtual circuit” between two computers. Defines a port HTTP: 80, IRC 194) Guarantees reliable and in-order delivery of packets. ...
Chapter 13 WAN Technologies and Routing
... Packet switching systems in WAN use store-and-forward switching. Incoming packets are stored in a buffer queue. The processor is interrupted to forward (queue) the packet to the proper outgoing port. This technique allows a packet switch to buffer a short burst of packets that arrive simultaneously. ...
... Packet switching systems in WAN use store-and-forward switching. Incoming packets are stored in a buffer queue. The processor is interrupted to forward (queue) the packet to the proper outgoing port. This technique allows a packet switch to buffer a short burst of packets that arrive simultaneously. ...
Interconnection Networks
... More expensive : need to replicated medium Higher total bandwidth No arbitration Added latency to go through the switch ...
... More expensive : need to replicated medium Higher total bandwidth No arbitration Added latency to go through the switch ...
Internet slides
... • IP addresses are assigned to hosts by their internet service providers • Not physical addresses: IP address does not identify a single node, can swap machines and reuse the same IP address • Not entirely virtual: the IP address determines how packets get to you, and changes when you change your ...
... • IP addresses are assigned to hosts by their internet service providers • Not physical addresses: IP address does not identify a single node, can swap machines and reuse the same IP address • Not entirely virtual: the IP address determines how packets get to you, and changes when you change your ...
Only $7000 USD - Network Forensics | Lawful Interception
... Forensics Analysis System Only at US$ 7000. ...
... Forensics Analysis System Only at US$ 7000. ...
投影片 1
... Roaming support of wireless component communication Switching support of component communication using network processors Streaming support of component communication for multimedia applications Transcoding support (On-going) ...
... Roaming support of wireless component communication Switching support of component communication using network processors Streaming support of component communication for multimedia applications Transcoding support (On-going) ...
lecture02
... • TTL (prevents messages from looping around forever; packets “die” if they “get lost”) ...
... • TTL (prevents messages from looping around forever; packets “die” if they “get lost”) ...
Artificial Intelligence in Networking: Ant Colony Optimization
... “Good news travels slow, bad news travels fast.” ...
... “Good news travels slow, bad news travels fast.” ...
The Next Generation of IP
... T. Bonald, S. Oueslati and J. W. Robert, “Flow-aware admission control for a commercially viable Internet”, EURESCOM, 2002 L. G. Roberts, “The Next Generation of IP-Flow routing”, SSGRR International ...
... T. Bonald, S. Oueslati and J. W. Robert, “Flow-aware admission control for a commercially viable Internet”, EURESCOM, 2002 L. G. Roberts, “The Next Generation of IP-Flow routing”, SSGRR International ...
Lecture 1 - Department Of Computer Science
... sending first data packet While the connection request contains the full address for destination, each data packet contains only a small identifier, making the per-packet header overhead small If a switch or a link in a connection fails, the connection is broken and a new one needs to be established ...
... sending first data packet While the connection request contains the full address for destination, each data packet contains only a small identifier, making the per-packet header overhead small If a switch or a link in a connection fails, the connection is broken and a new one needs to be established ...
Network_Layer
... path length we put weight for each link. This weight could be distance, cost… etc. or any number of them. See example Figure 5-7 page 353-354 (Tanenbaum) Flooding Routing: Packets are sent on every outgoing link. Problems: can send multiple unneeded packets. Packets may take loops. Solutions: ...
... path length we put weight for each link. This weight could be distance, cost… etc. or any number of them. See example Figure 5-7 page 353-354 (Tanenbaum) Flooding Routing: Packets are sent on every outgoing link. Problems: can send multiple unneeded packets. Packets may take loops. Solutions: ...
ppt - NOISE
... • Source routing: Complete route is contained in each data packet • Circuit Switching: Signaling protocol sets up entire path out-of-band. (cf. the phone network) • Virtual Circuits: Hybrid approach. Packets carry “tags” to indicate path, forwarding over IP ...
... • Source routing: Complete route is contained in each data packet • Circuit Switching: Signaling protocol sets up entire path out-of-band. (cf. the phone network) • Virtual Circuits: Hybrid approach. Packets carry “tags” to indicate path, forwarding over IP ...
PowerPoint XP
... Network: physical connection that allows two computers to communicate Packet: a unit of transfer ...
... Network: physical connection that allows two computers to communicate Packet: a unit of transfer ...
Document
... Network: physical connection that allows two computers to communicate Packet: a unit of transfer ...
... Network: physical connection that allows two computers to communicate Packet: a unit of transfer ...
This morning one of our programmers, Zundra Daniel went up to
... This mass replication of packets leads to extremely high levels of network traffic and causes severe packet collision problems. This does not occur on most wired networks because most networks use switches or routers (wired not wireless) instead of hubs. Switches and routers are "intelligent" and kn ...
... This mass replication of packets leads to extremely high levels of network traffic and causes severe packet collision problems. This does not occur on most wired networks because most networks use switches or routers (wired not wireless) instead of hubs. Switches and routers are "intelligent" and kn ...
PH19510 Lecture 12
... Building networks is a collaborative enterprise. RFC mechanism came out of ARPA Serve as mechanism for dissemination for information Some become adopted as standards ...
... Building networks is a collaborative enterprise. RFC mechanism came out of ARPA Serve as mechanism for dissemination for information Some become adopted as standards ...
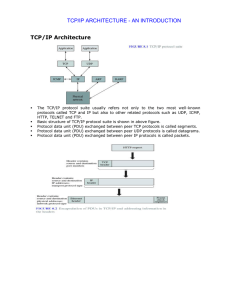
TCP/IP Architecture TCP/IP ARCHITECTURE
... IP address needs to be resolved to physical address at each IP network interface Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are ...
... IP address needs to be resolved to physical address at each IP network interface Example: Ethernet uses 48-bit addresses o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address o First 24 bits identify NIC manufacturer; second 24 bits are ...
Firewalls - Eastern Michigan University
... Firewalls – Type of Protection Packet Inspection IP, TCP, UDP, ICMP Static packet filtering (Stateless filtering) ...
... Firewalls – Type of Protection Packet Inspection IP, TCP, UDP, ICMP Static packet filtering (Stateless filtering) ...
Overview of Communications Technologies
... Digital Subscriber Lines DSL uses packet switching technology that operates independent of the voice telephone system, allowing the telephone companies to provide the service and not ...
... Digital Subscriber Lines DSL uses packet switching technology that operates independent of the voice telephone system, allowing the telephone companies to provide the service and not ...