VoIP Performance in SIP-Based Vertical Handovers Between WLAN
... environment is Voice over IP (VoIP,) which permits to carry out voice calls over packet-switched networks. One of the most challenging problems for system integration is the provision of seamless mobility support among different access technologies. Several protocols have been proposed for handling ...
... environment is Voice over IP (VoIP,) which permits to carry out voice calls over packet-switched networks. One of the most challenging problems for system integration is the provision of seamless mobility support among different access technologies. Several protocols have been proposed for handling ...
$doc.title
... – Detects changes made to mailbox by other clients – Server keeps message state (e.g., read, replied to) ...
... – Detects changes made to mailbox by other clients – Server keeps message state (e.g., read, replied to) ...
Selling an Idea or a Product
... Face similar issues as in TCP when building big messages on small ones, when messages can get dropped. Ack each fragment? Lots of acks One ack for entire big message? Re-transmit all fragments, even if only one gets dropped “Blast protocol” – send one ack, tells sender which pieces were missing. Sel ...
... Face similar issues as in TCP when building big messages on small ones, when messages can get dropped. Ack each fragment? Lots of acks One ack for entire big message? Re-transmit all fragments, even if only one gets dropped “Blast protocol” – send one ack, tells sender which pieces were missing. Sel ...
MSG(13)034xxx Pseudo CHANGE REQUEST 124 229 Version 11.9
... As described in 3GPP TS 22.101, the eCall only UE, determined by information configured in the USIM, has limitation in the services it may receive based on the information configured in the USIM. The eCall only UE can initiate eCall emergency services and received call-back from the PSAP. The eCall ...
... As described in 3GPP TS 22.101, the eCall only UE, determined by information configured in the USIM, has limitation in the services it may receive based on the information configured in the USIM. The eCall only UE can initiate eCall emergency services and received call-back from the PSAP. The eCall ...
Check Point Endpoint Security with Pointsec
... delegates attend the authorised training course(s), study the official manual (provided only on authorised courses) and have 6 months experience using the technology. ...
... delegates attend the authorised training course(s), study the official manual (provided only on authorised courses) and have 6 months experience using the technology. ...
download
... • Transmits to proper destination host Via SMTP transaction Over one or more TCP connections to port 25 • Host may have multiple senders active • Host should be able to create receivers on demand • When delivery complete, sender deletes destination from list for that message • When all destinations ...
... • Transmits to proper destination host Via SMTP transaction Over one or more TCP connections to port 25 • Host may have multiple senders active • Host should be able to create receivers on demand • When delivery complete, sender deletes destination from list for that message • When all destinations ...
William Stallings Data and Computer Communications
... Ability for receivers to make reservations Deal gracefully with changes in multicast group membership Specify resource requirements such that aggregate resources reflect requirements Enable receivers to select one source Deal gracefully with changes in routes ...
... Ability for receivers to make reservations Deal gracefully with changes in multicast group membership Specify resource requirements such that aggregate resources reflect requirements Enable receivers to select one source Deal gracefully with changes in routes ...
William Stallings Data and Computer Communications
... • Ability for receivers to make reservations • Deal gracefully with changes in multicast group membership • Specify resource requirements such that aggregate resources reflect requirements • Enable receivers to select one source • Deal gracefully with changes in routes ...
... • Ability for receivers to make reservations • Deal gracefully with changes in multicast group membership • Specify resource requirements such that aggregate resources reflect requirements • Enable receivers to select one source • Deal gracefully with changes in routes ...
In NGN networks, call and service control is
... Equipment) network. IPVsuite-200 provides key provisioning services such as security, address resolution, real-time monitoring, service activation, analysis and error management. It also generates usage and CDR information and provides massive remote upgrading capabilities. RESELLER SEGMENTATION The ...
... Equipment) network. IPVsuite-200 provides key provisioning services such as security, address resolution, real-time monitoring, service activation, analysis and error management. It also generates usage and CDR information and provides massive remote upgrading capabilities. RESELLER SEGMENTATION The ...
When WiMAX meets IMS TextStart WiMAX features wide coverage
... The Huawei WiMAX+IMS convergence solution can provide end-to-end QoS assurance and can deploy static QoS and dynamic QoS solutions in different phases according to the QoS requirements for carried services. The solution offers end-to-end QoS features for carried services. At the air interface on the ...
... The Huawei WiMAX+IMS convergence solution can provide end-to-end QoS assurance and can deploy static QoS and dynamic QoS solutions in different phases according to the QoS requirements for carried services. The solution offers end-to-end QoS features for carried services. At the air interface on the ...
Survey On Massive Multimedia Content Delivery In
... channel, the selected channel number is signaled to the streaming server which then immediately starts to forward the multimedia content of the new channel to the client. But the quality of the delivered multimedia content is low. For this purpose the service called Multimedia Broadcast Multicast Se ...
... channel, the selected channel number is signaled to the streaming server which then immediately starts to forward the multimedia content of the new channel to the client. But the quality of the delivered multimedia content is low. For this purpose the service called Multimedia Broadcast Multicast Se ...
Document
... corresponding nodes’ RSA public key. When routing, each proxy can decrypt the most out layer of the message. Finally, the message is sent out to destination server until all layers are striped out by corresponding nodes. The return message can route back to initiator in reverse way. In MIX, each nod ...
... corresponding nodes’ RSA public key. When routing, each proxy can decrypt the most out layer of the message. Finally, the message is sent out to destination server until all layers are striped out by corresponding nodes. The return message can route back to initiator in reverse way. In MIX, each nod ...
Chapter06
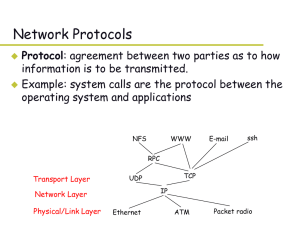
... • Why two distinct layers? – App programs can be written using standard primitives and have them work on a wide variety of networks - ignoring subnet interfaces and poor transmission – Isolates upper layers from imperfections of subnet – Bottom 4 layers are transport service provider – Upper layers ...
... • Why two distinct layers? – App programs can be written using standard primitives and have them work on a wide variety of networks - ignoring subnet interfaces and poor transmission – Isolates upper layers from imperfections of subnet – Bottom 4 layers are transport service provider – Upper layers ...
Internet Telephony Conference & Expo San Diego
... Single network in a multi-node environment. Transparency between nodes. Tele-workers. SIP clients and applications. SIP trunks. Remote phones. ...
... Single network in a multi-node environment. Transparency between nodes. Tele-workers. SIP clients and applications. SIP trunks. Remote phones. ...
Tor: The Second-Generation Onion Router
... how many relay data cells allowed to the OR for packaging back to the OP. The delivery window: tracks how many relay data cells given to TCP streams outside the network. OR after receiving enough data cells, it sends a send me relay to the OP with streamID zero. It then increments the packaging wind ...
... how many relay data cells allowed to the OR for packaging back to the OP. The delivery window: tracks how many relay data cells given to TCP streams outside the network. OR after receiving enough data cells, it sends a send me relay to the OP with streamID zero. It then increments the packaging wind ...
Tor: The Second-Generation Onion Router
... how many relay data cells allowed to the OR for packaging back to the OP. The delivery window: tracks how many relay data cells given to TCP streams outside the network. OR after receiving enough data cells, it sends a send me relay to the OP with streamID zero. It then increments the packaging wind ...
... how many relay data cells allowed to the OR for packaging back to the OP. The delivery window: tracks how many relay data cells given to TCP streams outside the network. OR after receiving enough data cells, it sends a send me relay to the OP with streamID zero. It then increments the packaging wind ...
EEE449 Computer Networks
... For each data unit transmitted by A, A makes a decision as to which router should receive the data unit. The data unit hops across the internet from one router to the next until it reaches the destination network. At each router, a routing decision is made (independently for each data unit) concerni ...
... For each data unit transmitted by A, A makes a decision as to which router should receive the data unit. The data unit hops across the internet from one router to the next until it reaches the destination network. At each router, a routing decision is made (independently for each data unit) concerni ...
Solving the problems of IMS using P2P technology By Adrian
... What is so special about P2P technology? 1. Join/Leave: Nodes may come and go at any time, the network topology reconfigures itself 2. Lookup: The network can locate deterministically the node that serves a specific user or service 3. Routing: The network can route a message regardless of network to ...
... What is so special about P2P technology? 1. Join/Leave: Nodes may come and go at any time, the network topology reconfigures itself 2. Lookup: The network can locate deterministically the node that serves a specific user or service 3. Routing: The network can route a message regardless of network to ...
Real-time visibility: HPE End User Management for application
... Get organized - Monitor All users, All locations, All the time. HPE Real User Monitor software lets you measure the true experience of all of your users, all the time and all locations. You can then gauge the business impact of performance issues and outages, and isolate user trends in detail. Using ...
... Get organized - Monitor All users, All locations, All the time. HPE Real User Monitor software lets you measure the true experience of all of your users, all the time and all locations. You can then gauge the business impact of performance issues and outages, and isolate user trends in detail. Using ...
Chapter 10
... » If root server has answer, results are returned » If root server recognizes domain name but not extension in front of domain name, root server will query server at domain name’s location » When domain’s server returns results, they are passed back through chain of servers (and their caches) Data C ...
... » If root server has answer, results are returned » If root server recognizes domain name but not extension in front of domain name, root server will query server at domain name’s location » When domain’s server returns results, they are passed back through chain of servers (and their caches) Data C ...
Chapter 8
... ICMP messages not generated if error results from datagram carrying ICMP error message ...
... ICMP messages not generated if error results from datagram carrying ICMP error message ...
CSCI6268L20
... • Our local routing table (on host of user1) is not going to have a route to IP of user2 – Routing table will therefore send our packet to the gateway – Gateway is the machine/router on the “edge” of the network responsible for processing all incoming/outgoing traffic from/to the LAN • NAT boxing, f ...
... • Our local routing table (on host of user1) is not going to have a route to IP of user2 – Routing table will therefore send our packet to the gateway – Gateway is the machine/router on the “edge” of the network responsible for processing all incoming/outgoing traffic from/to the LAN • NAT boxing, f ...