a destination IP address
... The figure shown is an example of a layer 3 network. The components that make up the layer 3 network are shown. The source host computer has an installed network interface card (NIC), an assigned IP address and subnet mask. The subnet mask is used to determine if the data is to stay in the LAN or i ...
... The figure shown is an example of a layer 3 network. The components that make up the layer 3 network are shown. The source host computer has an installed network interface card (NIC), an assigned IP address and subnet mask. The subnet mask is used to determine if the data is to stay in the LAN or i ...
Network Operating Systems - Partha Dasgupta`s Workstation!
... top of the TCP-IP protocol. These programs include telnet, ftp and e-mail. The telnet program (as well as its cousins rlogin and rsh) program allow a user on one machine to transparently access another machine. Similarly, ftp allowed transmission of files between machines with ease. E-mail opened a ...
... top of the TCP-IP protocol. These programs include telnet, ftp and e-mail. The telnet program (as well as its cousins rlogin and rsh) program allow a user on one machine to transparently access another machine. Similarly, ftp allowed transmission of files between machines with ease. E-mail opened a ...
ppt
... • As long as applications can run over IP-based protocols, they can run on any network • As long as networks support IP, they can run any application ...
... • As long as applications can run over IP-based protocols, they can run on any network • As long as networks support IP, they can run any application ...
Lecturer: Dr. Ahmed M. Al
... • Time To Live (TTL) The maximum number of hops a packet can traverse between the source and destination hosts. Each packet switch (or router) that a packet crosses decrements the TTL field by one. When the TTL field becomes zero, the packet is no longer forwarded by a packet switch and is discarded ...
... • Time To Live (TTL) The maximum number of hops a packet can traverse between the source and destination hosts. Each packet switch (or router) that a packet crosses decrements the TTL field by one. When the TTL field becomes zero, the packet is no longer forwarded by a packet switch and is discarded ...
A close look at Seamless MPLS networking TextStart Seamless
... The LDP DoD label release mode is used between the UPE and AN. The AN must be cost-effective; therefore, DoD mode allows the AN to request the needed labels on demand. As a result, the specification requirement of the MPLS forwarding table is reduced. The LDP DU labels are distributed to the edge of ...
... The LDP DoD label release mode is used between the UPE and AN. The AN must be cost-effective; therefore, DoD mode allows the AN to request the needed labels on demand. As a result, the specification requirement of the MPLS forwarding table is reduced. The LDP DU labels are distributed to the edge of ...
Quality of Service Guarantee on 802.11 Networks
... host holding the token transmits the token to the next logical neighbor in the ring and transmits an ACK to the previous logical neighbor in the ring. With such a distributed token maintenance protocol there is no single point of failure in the network and hosts can join and leave the the ring at an ...
... host holding the token transmits the token to the next logical neighbor in the ring and transmits an ACK to the previous logical neighbor in the ring. With such a distributed token maintenance protocol there is no single point of failure in the network and hosts can join and leave the the ring at an ...
CCNP Routing Semester 5
... alert each other about downed links or newly discovered paths. Routers automatically “learn” a network’s topology and select optimum paths • Low maintenance configuration – after the basic parameters for a routing protocol are set correctly, administrative intervention is not required ...
... alert each other about downed links or newly discovered paths. Routers automatically “learn” a network’s topology and select optimum paths • Low maintenance configuration – after the basic parameters for a routing protocol are set correctly, administrative intervention is not required ...
HOPI Project Update
... • Internet2 set up to catalyze activities and provide for services that cannot be accomplished/provided by individual organizations • We have leverage if we act together ...
... • Internet2 set up to catalyze activities and provide for services that cannot be accomplished/provided by individual organizations • We have leverage if we act together ...
Unit 1
... connection-oriented services. We will first discuss UDP since it is the simpler of the two protocols and much of what is true of UDP is true for TCP. Two of the primary responsibilities of a transport layer protocol are end-toend delivery of data and making sure that data is delivered error-free (no ...
... connection-oriented services. We will first discuss UDP since it is the simpler of the two protocols and much of what is true of UDP is true for TCP. Two of the primary responsibilities of a transport layer protocol are end-toend delivery of data and making sure that data is delivered error-free (no ...
Protocols and the tcp/ip suite
... – Functional description that defines what services are provided, but not how the services are to be provided ...
... – Functional description that defines what services are provided, but not how the services are to be provided ...
Network+ Guide to Networks 5 th Edition Chapter 5
... – Signals travel from one device to all other devices – May or may not travel through intervening connectivity device – Bus logical topology used by networks with: • Physical bus topology • Star, star-wired bus topology ...
... – Signals travel from one device to all other devices – May or may not travel through intervening connectivity device – Bus logical topology used by networks with: • Physical bus topology • Star, star-wired bus topology ...
Malicious Threats of Peer-to-Peer Networking
... threat could register with the Napster centralized server and pass a specific, unique list of files. Then, a hacker would perform a search on those specific files, and when matched, he or she would be able to identify any infected systems. A request for a certain file would signal the infected machi ...
... threat could register with the Napster centralized server and pass a specific, unique list of files. Then, a hacker would perform a search on those specific files, and when matched, he or she would be able to identify any infected systems. A request for a certain file would signal the infected machi ...
uCast Presentation
... through single interface to facilitate a pair-wise comparison to obtain “closest” to destination • Implements a scoreboard algorithm ...
... through single interface to facilitate a pair-wise comparison to obtain “closest” to destination • Implements a scoreboard algorithm ...
Part I: Introduction
... • Arbitrary topologies can be supported, cycling is limited by TTL counters (and good routing protocols) • Provide firewall protection against broadcast storms ...
... • Arbitrary topologies can be supported, cycling is limited by TTL counters (and good routing protocols) • Provide firewall protection against broadcast storms ...
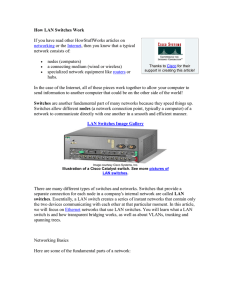
How LAN Switches Work
... A computer (Node A) on the first segment (Segment A) sends data to a computer (Node B) on another segment (Segment C). The switch gets the first packet of data from Node A. It reads the MAC address and saves it to the lookup table for Segment A. The switch now knows where to find Node A anytime a pa ...
... A computer (Node A) on the first segment (Segment A) sends data to a computer (Node B) on another segment (Segment C). The switch gets the first packet of data from Node A. It reads the MAC address and saves it to the lookup table for Segment A. The switch now knows where to find Node A anytime a pa ...
Question Answers
... There are three main types of hubs: 1) Passive 2) Active 3) Intelligent Passive Hubs: A passive hubs simply combines the signals of a network segments. There is no signal processing or regeneration. A passive hub reduces the cabling distance by half because it does not boost the signals and in fact ...
... There are three main types of hubs: 1) Passive 2) Active 3) Intelligent Passive Hubs: A passive hubs simply combines the signals of a network segments. There is no signal processing or regeneration. A passive hub reduces the cabling distance by half because it does not boost the signals and in fact ...
Providing Guaranteed Services without Per Flow Management
... • If all flows were sending at their reserved rates, computing Re is trivial; just measure traffic throughput • Problem: what if flows do not send at their reserved rates? • Solution: Associate with each packet a virtual length - virtual length = r * (time now - transmit time of previous packet) • U ...
... • If all flows were sending at their reserved rates, computing Re is trivial; just measure traffic throughput • Problem: what if flows do not send at their reserved rates? • Solution: Associate with each packet a virtual length - virtual length = r * (time now - transmit time of previous packet) • U ...
MCCME Moscow, 1998
... actually used. We'll consider only one in moderate detail: namely, the so-called thin Ethernet.1 This choice was made because Ethernet is not too hard to describe; because it is used in many places, so you are likely to encounter it; and because we had to choose something. We'll be describing thin E ...
... actually used. We'll consider only one in moderate detail: namely, the so-called thin Ethernet.1 This choice was made because Ethernet is not too hard to describe; because it is used in many places, so you are likely to encounter it; and because we had to choose something. We'll be describing thin E ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... GNS3 is an excellent complementary tool to real labs for network engineers, administrators and people want to study for certifications such as Cisco CCNA, CCNP, CCIP and CCIE as well as Juniper JNCIA, JNCIS and JNCIE.It can also be used to experiment features of Cisco IOS, Juniper JunOS or to check ...
... GNS3 is an excellent complementary tool to real labs for network engineers, administrators and people want to study for certifications such as Cisco CCNA, CCNP, CCIP and CCIE as well as Juniper JNCIA, JNCIS and JNCIE.It can also be used to experiment features of Cisco IOS, Juniper JunOS or to check ...
MPV2
... Consumption of Scarce Resources Using own resources against them: When a connection is established between two UDP services, each of which produces output, then these two services can produce a very high number of packets UDP Packet Storm – By connecting a host's chargen service to the echo service ...
... Consumption of Scarce Resources Using own resources against them: When a connection is established between two UDP services, each of which produces output, then these two services can produce a very high number of packets UDP Packet Storm – By connecting a host's chargen service to the echo service ...
CCNA3:LAN
... troubleshooting project using the skills gained in CCNA 3. Students will use the skills that have already been developed to use, make and connect the proper cabling to the appropriate devices. It is crucial to read and understand the scenarios to make sure that all requirements are fulfilled. Each s ...
... troubleshooting project using the skills gained in CCNA 3. Students will use the skills that have already been developed to use, make and connect the proper cabling to the appropriate devices. It is crucial to read and understand the scenarios to make sure that all requirements are fulfilled. Each s ...