15-744: Computer Networking
... • Humans use readable host names • E.g. www.cmu.edu • Globally unique (can correspond to multiple hosts) ...
... • Humans use readable host names • E.g. www.cmu.edu • Globally unique (can correspond to multiple hosts) ...
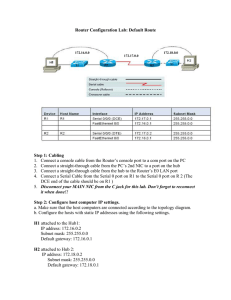
3 Router Configuration - Cisco Networking Academy
... Router #show running-config (or show run) Step 20 Check to see that your interfaces are up and running a. Check the Interface status Router # show interfaces (or show int) b. Each interface should be shown separately, with a status line that tells you if that interface is up and running. The int ...
... Router #show running-config (or show run) Step 20 Check to see that your interfaces are up and running a. Check the Interface status Router # show interfaces (or show int) b. Each interface should be shown separately, with a status line that tells you if that interface is up and running. The int ...
Microsoft Windows 2000? Router Configuration Guide
... The advantage of static routing is that for remote sites or a subnet with only one link to outside connectivity, all non-local traffic can be directed to the next subnet or router. This is an advantage for remote office networks because the routing is simplified by routing all non-local traffic over ...
... The advantage of static routing is that for remote sites or a subnet with only one link to outside connectivity, all non-local traffic can be directed to the next subnet or router. This is an advantage for remote office networks because the routing is simplified by routing all non-local traffic over ...
Configuring RIP
... • A procedure for sending and receiving reachability information about network to other routers • A procedure for calculating optimal routes – Routes are calculated using a shortest path algorithm: • Goal: Given a network were each link is assigned a cost. Find the path with the least cost between t ...
... • A procedure for sending and receiving reachability information about network to other routers • A procedure for calculating optimal routes – Routes are calculated using a shortest path algorithm: • Goal: Given a network were each link is assigned a cost. Find the path with the least cost between t ...
Slides
... formed from the union of the incoming statelet’s route and an imaginary direct span joining the tandem node to cycler node. Hopcount is the number of spans so far traversed in the statelet’s ...
... formed from the union of the incoming statelet’s route and an imaginary direct span joining the tandem node to cycler node. Hopcount is the number of spans so far traversed in the statelet’s ...
Chapter 7
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
Sample Chapter
... of interactive modules, each of which provides a specific functionality. The term hierarchical means that each upper level protocol is supported by the services provided by one or more lower level protocols. The original TCP/IP protocol suite was defined as four software layers built upon the hardwa ...
... of interactive modules, each of which provides a specific functionality. The term hierarchical means that each upper level protocol is supported by the services provided by one or more lower level protocols. The original TCP/IP protocol suite was defined as four software layers built upon the hardwa ...
M051055
... protocol. As the name implies, EIGRP is better than IGRP. So, we hypothesized network using EIGRP will have a better routing performance. This paper consist of comparisons of OSPF, IGRP with EIGRP, Implementation of dynamic routing protocol EIGRP in the IPv6 network, and gives how the routing tables ...
... protocol. As the name implies, EIGRP is better than IGRP. So, we hypothesized network using EIGRP will have a better routing performance. This paper consist of comparisons of OSPF, IGRP with EIGRP, Implementation of dynamic routing protocol EIGRP in the IPv6 network, and gives how the routing tables ...
Security in Computer Networks
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
Chp7
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
Lecture note 7
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking ...
router - DAINF
... • errors caused by signal attenuation, noise. • receiver detects presence of errors: • signals sender for retransmission or drops frame ...
... • errors caused by signal attenuation, noise. • receiver detects presence of errors: • signals sender for retransmission or drops frame ...
Address Resolution Protocol
... For the purposes of IP mapping, Ethernet, Token Ring, and FDDI frames contain the destination and source addresses. Frame Relay and Asynchronous Transfer Mode (ATM) networks, which are packet-switched, data packets take different routes to reach the same destination. At the receiving end, the packet ...
... For the purposes of IP mapping, Ethernet, Token Ring, and FDDI frames contain the destination and source addresses. Frame Relay and Asynchronous Transfer Mode (ATM) networks, which are packet-switched, data packets take different routes to reach the same destination. At the receiving end, the packet ...
SWIM: Scalable Weakly-consistent Infection-style Process Group Membership Protocol
... heartbeating. Each process periodically sends out an incremented heartbeat counter to the outside world. Another process is detected as failed when a heartbeat is not received from it for some time. However, actual implementations of heartbeating suffer from scalability limitations. Sending all hear ...
... heartbeating. Each process periodically sends out an incremented heartbeat counter to the outside world. Another process is detected as failed when a heartbeat is not received from it for some time. However, actual implementations of heartbeating suffer from scalability limitations. Sending all hear ...
CSMA/CD - ECSE - Rensselaer Polytechnic Institute
... User gets frequency band and can transmit continuously in that band. Matches need of continuous streams (eg analog video) Bandwidth wasted due to guard bands All-optical networks uses variant: “WDMA” Combination of time/frequency: CDMA Code Division Multiple Access Divvy up both time a ...
... User gets frequency band and can transmit continuously in that band. Matches need of continuous streams (eg analog video) Bandwidth wasted due to guard bands All-optical networks uses variant: “WDMA” Combination of time/frequency: CDMA Code Division Multiple Access Divvy up both time a ...
OS6850 AOS 6.4.3 R01 Release Notes
... The software versions listed below are the minimum required, except where otherwise noted. Switches running the minimum versions, as listed below, do not require any Uboot, Miniboot, or FPGA uprades when upgrading to AOS 6.4.3.R01. Switches not running the minimum version required should upgrade to ...
... The software versions listed below are the minimum required, except where otherwise noted. Switches running the minimum versions, as listed below, do not require any Uboot, Miniboot, or FPGA uprades when upgrading to AOS 6.4.3.R01. Switches not running the minimum version required should upgrade to ...
Link Layer
... • errors caused by signal attenuation, noise. • receiver detects presence of errors: • signals sender for retransmission or drops frame ...
... • errors caused by signal attenuation, noise. • receiver detects presence of errors: • signals sender for retransmission or drops frame ...
... D-Link wireless products are based on industry standards to provide high-speed wireless connectivity that is easy to use within your home, business or public access wireless networks. D-Link wireless products provides you with access to the data you want, whenever and wherever you want it. Enjoy the ...
A modeling framework for gossip-based information spread
... There is previous work [18] on a simple gossip-based membership protocol with nonatomic protocol actions in the presence of message loss of up to 1%. The authors proposed to use a push-based gossip protocol, in which only an active node sends data to its peer, and immediately removes the sent data f ...
... There is previous work [18] on a simple gossip-based membership protocol with nonatomic protocol actions in the presence of message loss of up to 1%. The authors proposed to use a push-based gossip protocol, in which only an active node sends data to its peer, and immediately removes the sent data f ...
Installing Template Theme Files
... • IP provides unique addresses What if phone companies assigned the same number to two different phones? For communication to be possible, you need uniqueness ...
... • IP provides unique addresses What if phone companies assigned the same number to two different phones? For communication to be possible, you need uniqueness ...
ppt
... Reasons for Lower Improvement in TCP • COPE introduces packet re-ordering • Router queue is small smaller coding opportunity • TCP congestion window does not sufficiently open up due to wireless losses ...
... Reasons for Lower Improvement in TCP • COPE introduces packet re-ordering • Router queue is small smaller coding opportunity • TCP congestion window does not sufficiently open up due to wireless losses ...
Microsoft RDMA Update
... Specifies the Common Internet File System (CIFS) Protocol, a cross-platform, transport-independent protocol that provides a mechanism for client systems to use file and print services made available by server systems over a network. ...
... Specifies the Common Internet File System (CIFS) Protocol, a cross-platform, transport-independent protocol that provides a mechanism for client systems to use file and print services made available by server systems over a network. ...
Routed Protocol - Faculty of Computer Science and Information
... A protocol is a set of rules that determines how computers communicate with each other across networks. A protocol describes the following: The format that a message must conform to The way in which computers must exchange a message within the context of a particular activity ...
... A protocol is a set of rules that determines how computers communicate with each other across networks. A protocol describes the following: The format that a message must conform to The way in which computers must exchange a message within the context of a particular activity ...
3rd Edition, Chapter 5 - Simon Fraser University
... IP hierarchical address NOT portable depends on IP subnet to which node is attached ...
... IP hierarchical address NOT portable depends on IP subnet to which node is attached ...