No Slide Title
... A simple intradomain protocol Straightforward implementation of Distance Vector Routing Each router advertises its distance vector every 30 seconds (or whenever its routing table changes) RIP always uses the hop-count as link metric. Maximum hop count is 15, with “16” equal to “”. Routes timeout af ...
... A simple intradomain protocol Straightforward implementation of Distance Vector Routing Each router advertises its distance vector every 30 seconds (or whenever its routing table changes) RIP always uses the hop-count as link metric. Maximum hop count is 15, with “16” equal to “”. Routes timeout af ...
address address address address
... There are two types of broadcasts: –Directed Broadcast •A directed broadcast is sent to all hosts on a specific network. –This type of broadcast is useful for sending a broadcast to all hosts on a nonlocal network. –Routers do not forward directed broadcasts by default, they may be configured to d ...
... There are two types of broadcasts: –Directed Broadcast •A directed broadcast is sent to all hosts on a specific network. –This type of broadcast is useful for sending a broadcast to all hosts on a nonlocal network. –Routers do not forward directed broadcasts by default, they may be configured to d ...
chap2v3sem3 - Virtual Access
... gateway of last resort not redistributed interface network type mismatch no loopback interface configured administrative distance mismatch inconsistent authentication configuration 3 What information can be obtained from the output of the show ip ospf interface command? (Choose three.) link-state ag ...
... gateway of last resort not redistributed interface network type mismatch no loopback interface configured administrative distance mismatch inconsistent authentication configuration 3 What information can be obtained from the output of the show ip ospf interface command? (Choose three.) link-state ag ...
l4 - Heyook Lab
... RIP - Routing Information Protocol • A simple intradomain protocol • Straightforward implementation of Distance Vector Routing • Each router advertises its distance vector every 30 seconds (or whenever its routing table changes) to all of its neighbors • RIP always uses 1 as link metric • Maximum h ...
... RIP - Routing Information Protocol • A simple intradomain protocol • Straightforward implementation of Distance Vector Routing • Each router advertises its distance vector every 30 seconds (or whenever its routing table changes) to all of its neighbors • RIP always uses 1 as link metric • Maximum h ...
PXG3.L, PXG3.M BACnet Router
... Routing between BACnet/IP , BACnet/LonTalk (PXG3.L only), and BACnet MS/TP Compliant with ANSI/ASHRAE 135-2010 Compliant with ISO 16484-5 Support for BBMD (BACnet Broadcast Management Device) Support for Foreign Device Configuration via Xworks Plus or Web browser Access to network statistics via Web ...
... Routing between BACnet/IP , BACnet/LonTalk (PXG3.L only), and BACnet MS/TP Compliant with ANSI/ASHRAE 135-2010 Compliant with ISO 16484-5 Support for BBMD (BACnet Broadcast Management Device) Support for Foreign Device Configuration via Xworks Plus or Web browser Access to network statistics via Web ...
address… - ECSE - Rensselaer Polytechnic Institute
... Simple: Works as an application protocol running over UDP Agent and manager apps work on top of SNMP Proxy-SNMP can be used to manage a variety of devices (serial lines, bridges, modems etc). Proxy (similar to bridge) is needed because these devices may not run UDP/IP For each new device d ...
... Simple: Works as an application protocol running over UDP Agent and manager apps work on top of SNMP Proxy-SNMP can be used to manage a variety of devices (serial lines, bridges, modems etc). Proxy (similar to bridge) is needed because these devices may not run UDP/IP For each new device d ...
Proceedings of USITS ’03: 4th USENIX Symposium on Internet Technologies and Systems
... In Section 3.1, we described how nodes establish long links with other nodes. The average number of incoming links is k per node. In practice, a link between two nodes would see continuous routing traf c. This would be materialized as a bidirectional TCP connection to leverage TCP's ow control, dup ...
... In Section 3.1, we described how nodes establish long links with other nodes. The average number of incoming links is k per node. In practice, a link between two nodes would see continuous routing traf c. This would be materialized as a bidirectional TCP connection to leverage TCP's ow control, dup ...
FLIP: an Internetwork Protocol for Supporting Distributed Systems,
... traditional network systems. Network systems run all of a user’s applications on a single workstation. Workstations run a copy of the complete operating system; the only thing that is shared is the file system. Applications are sequential; they make no use of any available parallelism. In such an en ...
... traditional network systems. Network systems run all of a user’s applications on a single workstation. Workstations run a copy of the complete operating system; the only thing that is shared is the file system. Applications are sequential; they make no use of any available parallelism. In such an en ...
WAN_Unit_8-SMDS
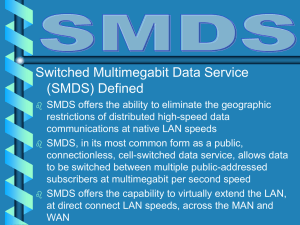
... The interconnection of multiple SMDS or DQDB subnetworks forms a Metropolitan Area Network (MAN). The MAN can provide shared media for voice, data, and video transmissions over a local geographic area, as well as high-speed extension of each LAN and WAN attached Cells are routed through the MAN wide ...
... The interconnection of multiple SMDS or DQDB subnetworks forms a Metropolitan Area Network (MAN). The MAN can provide shared media for voice, data, and video transmissions over a local geographic area, as well as high-speed extension of each LAN and WAN attached Cells are routed through the MAN wide ...
Peer
... Conceived by Sun Microsystems + designed by a small number of experts from academic institutions and industry • team identified a number of shortcomings in many existing peer-to-peer systems and set up project JXTA in order to address these. • their 3 main objectives of were to achieve interoperabil ...
... Conceived by Sun Microsystems + designed by a small number of experts from academic institutions and industry • team identified a number of shortcomings in many existing peer-to-peer systems and set up project JXTA in order to address these. • their 3 main objectives of were to achieve interoperabil ...
KMBE - RADProductsOnline, Buy RAD Products Online at Great Prices
... intellectual property or other proprietary rights relating to this manual and to the KMBE and any software components contained therein are proprietary products of RAD protected under international copyright law and shall be and remain solely with RAD. KMBE is a registered trademark of RAD. No right ...
... intellectual property or other proprietary rights relating to this manual and to the KMBE and any software components contained therein are proprietary products of RAD protected under international copyright law and shall be and remain solely with RAD. KMBE is a registered trademark of RAD. No right ...
Introduction - School of Computing and Information Sciences
... enough information to allow an implementer to write a program or develop the hardware for each layer so that it will correctly obey the appropriate protocols. Neither the details of implementation nor the specification of interfaces is part of the architecture because these are hidden inside a machi ...
... enough information to allow an implementer to write a program or develop the hardware for each layer so that it will correctly obey the appropriate protocols. Neither the details of implementation nor the specification of interfaces is part of the architecture because these are hidden inside a machi ...
Router Anatomy - Institute for Systems Research
... Switching Interface: Use switching element to pass packets between line cards directly and simultaneously. ...
... Switching Interface: Use switching element to pass packets between line cards directly and simultaneously. ...
ppt
... encapsulate datagram into frame, adding header, trailer implement channel access if shared medium, ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! ...
... encapsulate datagram into frame, adding header, trailer implement channel access if shared medium, ‘physical addresses’ used in frame headers to identify source, dest • different from IP address! ...
MTA Networking Lessons 1-8 Question Bank
... Explanation: A switch switches very fast between multiple connections, which allow multiple computers to communicate at the same time. As a result, each client can send and receive at the same time (full duplex), which gives better performance. 5. What do you use to isolate a group of computers with ...
... Explanation: A switch switches very fast between multiple connections, which allow multiple computers to communicate at the same time. As a result, each client can send and receive at the same time (full duplex), which gives better performance. 5. What do you use to isolate a group of computers with ...
Activity 6.4.1: Basic VLSM Calculation and Addressing Design
... Task 2: Design an IP Addressing Scheme Step 1: Determine the subnet information for the largest network segment or segments. In this case, the two HQ LANs are the largest subnets. 1. How many IP addresses are needed for each LAN? _______ 2. What is the smallest size subnet that can be used to meet t ...
... Task 2: Design an IP Addressing Scheme Step 1: Determine the subnet information for the largest network segment or segments. In this case, the two HQ LANs are the largest subnets. 1. How many IP addresses are needed for each LAN? _______ 2. What is the smallest size subnet that can be used to meet t ...
Abstract: The Internet Engineering Task force began an effort to
... and educational sites are not a problem. The transition risk is small and the technological perspective is often seen as the primary factor for the decision. In an ideal transition concept the pushing force would be the technical advantage and new features offered by IPng, not any commonly decided t ...
... and educational sites are not a problem. The transition risk is small and the technological perspective is often seen as the primary factor for the decision. In an ideal transition concept the pushing force would be the technical advantage and new features offered by IPng, not any commonly decided t ...
Adaptive Packetization for Error-Prone Transmission over 802.11
... Krishnan et. al. have developed a new technique for estimating probabilities of various components of packet loss, namely, direct and staggered collisions and fading. Motivated by this work, in this paper, we exploit ways in which packetization can be used to improve throughput performance of WLANs. ...
... Krishnan et. al. have developed a new technique for estimating probabilities of various components of packet loss, namely, direct and staggered collisions and fading. Motivated by this work, in this paper, we exploit ways in which packetization can be used to improve throughput performance of WLANs. ...
3rd Edition, Chapter 5 - Department of Computer and Information
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) old-fashioned Ethernet upstream HFC (hybrid fiber-coaxial cable) 802.11 wireless LAN ...
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) old-fashioned Ethernet upstream HFC (hybrid fiber-coaxial cable) 802.11 wireless LAN ...
Proxy Server - California State University, Los Angeles
... configured in Auto Dial as an: RAS Client - to dial out only. RAS Server - can be both dial out and receive calls or just receive calls only. RAS Server requires a high level of security on you Intranet. ...
... configured in Auto Dial as an: RAS Client - to dial out only. RAS Server - can be both dial out and receive calls or just receive calls only. RAS Server requires a high level of security on you Intranet. ...
Lecture 3 TCP/IP model
... that tells the sender how many bytes it can send before the receiver will have to toss it away (due to fixed buffer size). ...
... that tells the sender how many bytes it can send before the receiver will have to toss it away (due to fixed buffer size). ...
Performance Enhancement of TFRC in Wireless Networks
... Spec says can use four separate twisted pairs of Cat 3 UTP (now Cat 5e). Utilize three pair in both directions (at 33 1/3 Mbps) with other pair for carrier sense/collision detection. Three-level ternary code is used 8B/6T:: Prior to transmission each set of 8 bits is converted into 6 ternary symbols ...
... Spec says can use four separate twisted pairs of Cat 3 UTP (now Cat 5e). Utilize three pair in both directions (at 33 1/3 Mbps) with other pair for carrier sense/collision detection. Three-level ternary code is used 8B/6T:: Prior to transmission each set of 8 bits is converted into 6 ternary symbols ...
Connection-oriented internetworking
... popping it off if outgoing port is untagged – The form of mux/demux on each port is changeable on a packet-by-packet basis – quite amazing! • on packet can come in w/o a VLAN tag requiring the switch to forward it according to rules of its untagged VLAN setting • another packet can come in with a VL ...
... popping it off if outgoing port is untagged – The form of mux/demux on each port is changeable on a packet-by-packet basis – quite amazing! • on packet can come in w/o a VLAN tag requiring the switch to forward it according to rules of its untagged VLAN setting • another packet can come in with a VL ...