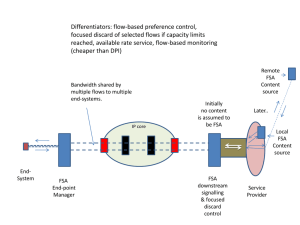
Protcols for Highly-Dynamic Airborne Networks
... • Specifies node congestion (defers packets from being forwarded) ...
... • Specifies node congestion (defers packets from being forwarded) ...
Internet and IP infrastructure
... • An internetwork composed of a collection of networks, routers, gateways, servers and clients linked by a set of telecommunication protocols – the IP family. • Client – a set of computers that receives services from servers • Server – a computer or software program that provides services to network ...
... • An internetwork composed of a collection of networks, routers, gateways, servers and clients linked by a set of telecommunication protocols – the IP family. • Client – a set of computers that receives services from servers • Server – a computer or software program that provides services to network ...
100% real exam questions answers
... A network device needs to be installed in the place of the icon labeled Network Device to accommodate a leased line attachment to the Internet. Which network device and interface configuration meets the minimum requirements for this installation? A. B. C. D. E. ...
... A network device needs to be installed in the place of the icon labeled Network Device to accommodate a leased line attachment to the Internet. Which network device and interface configuration meets the minimum requirements for this installation? A. B. C. D. E. ...
Computer Networks - Lynchburg College
... • Before we communicate with a computer on the network we have to be able to identify it. • Every computer on a network must have a unique “address”. • The system used on the Internet is called Internet Protocol (IP). Every machine on the Internet has a unique IP address.* ...
... • Before we communicate with a computer on the network we have to be able to identify it. • Every computer on a network must have a unique “address”. • The system used on the Internet is called Internet Protocol (IP). Every machine on the Internet has a unique IP address.* ...
Fundamentals of Computer Networks ECE 478/578
... fragmentation and re-assembly. Transport Layer: Flow (congestion) control, error control, transparent transport to upper layers Session Layer: Establishes connection among hosts, duplex, halfduplex, graceful connection termination, combination of streams Presentation Layer: Negotiation of format of ...
... fragmentation and re-assembly. Transport Layer: Flow (congestion) control, error control, transparent transport to upper layers Session Layer: Establishes connection among hosts, duplex, halfduplex, graceful connection termination, combination of streams Presentation Layer: Negotiation of format of ...
Unbuntu Installation
... designed to deal with a single human being at a time. Linux, like all Unix variants, is designed to handle multiple concurrent users. Windows, of course, can run many programs concurrently, as can Linux. There is a multi-user version of Windows called Terminal Server but this is not the Windows prei ...
... designed to deal with a single human being at a time. Linux, like all Unix variants, is designed to handle multiple concurrent users. Windows, of course, can run many programs concurrently, as can Linux. There is a multi-user version of Windows called Terminal Server but this is not the Windows prei ...
Network Hardware
... centralised, security is easier to manage, updates to the data are far easier to administer and it is far easier to backup the data centrally. ...
... centralised, security is easier to manage, updates to the data are far easier to administer and it is far easier to backup the data centrally. ...
Chapter 5 Local Area Network Concepts and Architecture
... Better service - response time and reliability Higher productivity Control or secure ...
... Better service - response time and reliability Higher productivity Control or secure ...
Networks - PEGSnet
... The most popular NOSes are: •Novell Netware (better, more expensive at first, cheaper over time) •Microsoft Server 2003 (now dominant) They offer similar services. ...
... The most popular NOSes are: •Novell Netware (better, more expensive at first, cheaper over time) •Microsoft Server 2003 (now dominant) They offer similar services. ...
Document
... message to all computers in the entire LAN, it is decided by this higher level device. This allows parallel communication to occur within the LAN without being effected by the higher level. To do this, the router needs to have a Dynamic Host Configuration Protocol (DHCP) ability. DHCP assigns each d ...
... message to all computers in the entire LAN, it is decided by this higher level device. This allows parallel communication to occur within the LAN without being effected by the higher level. To do this, the router needs to have a Dynamic Host Configuration Protocol (DHCP) ability. DHCP assigns each d ...
Document
... Packet Switching is a digital networking communications method that groups all transmitted data – regardless of content, type, or structure – into suitably-sized blocks, called packets. Packet switching features delivery of variable-bit-rate data streams (sequences of packets) over a shared network. ...
... Packet Switching is a digital networking communications method that groups all transmitted data – regardless of content, type, or structure – into suitably-sized blocks, called packets. Packet switching features delivery of variable-bit-rate data streams (sequences of packets) over a shared network. ...
answers - Princeton CS
... a. An application calling recv on a TCP socket will never get data out of order from the network. b. Ethernet allows for organizations to route traffic hierarchically to end hosts. c. Ethernet switches, like IP routers, use a form of forwarding table to determine which output links to send a packet. ...
... a. An application calling recv on a TCP socket will never get data out of order from the network. b. Ethernet allows for organizations to route traffic hierarchically to end hosts. c. Ethernet switches, like IP routers, use a form of forwarding table to determine which output links to send a packet. ...
Plutarch
... Locational: serve as descriptors allowing end-to-end services to be composed through network closures Mechanical: describe a set of communication mechanisms within which an endpoint might bind for a ...
... Locational: serve as descriptors allowing end-to-end services to be composed through network closures Mechanical: describe a set of communication mechanisms within which an endpoint might bind for a ...
NetworkingReview
... 5. Define the following terms: open network, closed network, proprietary network, MAN, LAN, WAN, bridge, repeater, switch, router, gateway, backbone. 6. Explain the hidden terminal problem for wireless networks. What is a solution? 7. At what layer in the TCP/IP protocol hierarchy would a firewall b ...
... 5. Define the following terms: open network, closed network, proprietary network, MAN, LAN, WAN, bridge, repeater, switch, router, gateway, backbone. 6. Explain the hidden terminal problem for wireless networks. What is a solution? 7. At what layer in the TCP/IP protocol hierarchy would a firewall b ...
Layer One Networking
... Application layer Presentation layer Session layer Transport layer Network layer Data link layer Physical layer ...
... Application layer Presentation layer Session layer Transport layer Network layer Data link layer Physical layer ...
CIS222 - Data Communications and Enterprise Networking
... Protocol Data Units are exchanged between peer entities at the same layer. The Network File System uses remote procedure calls to access files on a remote system. Simple Mail Transfer Protocol is used by mail clients to send and receive messages. ...
... Protocol Data Units are exchanged between peer entities at the same layer. The Network File System uses remote procedure calls to access files on a remote system. Simple Mail Transfer Protocol is used by mail clients to send and receive messages. ...
9/13/2010 Computer Network? The “nuts and bolts” view of the Internet
... ❍ “a communication medium used by millions” ...
... ❍ “a communication medium used by millions” ...
MAC, Scheduling, IP …
... Since netId is encoded into IP address, each host will have a unique IP address for each of its network connections Hence, IP addresses refer to network connections and not hosts Why will hosts have multiple network connections? ...
... Since netId is encoded into IP address, each host will have a unique IP address for each of its network connections Hence, IP addresses refer to network connections and not hosts Why will hosts have multiple network connections? ...
These reservations are recognized by the authority on TCP/IP
... protocol of the Internet. It can also be used as a communications protocol in a private network (Ethernet) When you set up a direct access to the Internet, your computer is provided with a copy of the TCP/IP program just as every other computer that you may send messages to or get information from a ...
... protocol of the Internet. It can also be used as a communications protocol in a private network (Ethernet) When you set up a direct access to the Internet, your computer is provided with a copy of the TCP/IP program just as every other computer that you may send messages to or get information from a ...
Slides for Chapter 3: Networking and Internetworking
... Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures ...
... Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures ...
chapter1
... Search Destination column of table entries with H-flag set which is an exact match to Destination IP in packet If found and Flag is G or H then Gateway is next hop; otherwise Destination IP is next hop. If not found then calculate Dest IP && Genmask for each entry that is not the default. If Dest IP ...
... Search Destination column of table entries with H-flag set which is an exact match to Destination IP in packet If found and Flag is G or H then Gateway is next hop; otherwise Destination IP is next hop. If not found then calculate Dest IP && Genmask for each entry that is not the default. If Dest IP ...
IST 201 - York Technical College
... • Getting messages from one network to another requires different approaches than getting messages from one host to another on a LAN • Internetworking – building networks of networks ...
... • Getting messages from one network to another requires different approaches than getting messages from one host to another on a LAN • Internetworking – building networks of networks ...
Parvus DuraMAR 1000 - Embedded Computing Design
... www.parvus.com DuraMAR 1000 Rugged Cisco 3200 IP Router – 5 Ethernet and 4 Serial on MIL-38999, MIL-810/704/1275/461 The DuraMAR™ 1000 is a rugged Mobile IP (Internet Protocol ) router designed for netcentric operations in harsh mobile environments. Leveraging Cisco Systems’ industry standard IOS® s ...
... www.parvus.com DuraMAR 1000 Rugged Cisco 3200 IP Router – 5 Ethernet and 4 Serial on MIL-38999, MIL-810/704/1275/461 The DuraMAR™ 1000 is a rugged Mobile IP (Internet Protocol ) router designed for netcentric operations in harsh mobile environments. Leveraging Cisco Systems’ industry standard IOS® s ...
internetworking ii
... What is the difference between actual and useable subnets? Actual subnets is how many total subnets are created by borrowing bits. Useable are the actual subnets less 2. The reason for this is that you can’t use the whole first subnet (it’s reserved for the network address) or the last subnet (it’s ...
... What is the difference between actual and useable subnets? Actual subnets is how many total subnets are created by borrowing bits. Useable are the actual subnets less 2. The reason for this is that you can’t use the whole first subnet (it’s reserved for the network address) or the last subnet (it’s ...