Document
... Hypertext Transfer Protocol (HTTP) - TCP Port 80 Simple Mail Transfer Protocol (SMTP) - TCP Port 25 Post Office Protocol (POP) - UDP Port 110 Telnet - TCP Port 23 Dynamic Host Configuration Protocol - UDP Port 67 File Transfer Protocol (FTP) - TCP Ports 20 and 21 ...
... Hypertext Transfer Protocol (HTTP) - TCP Port 80 Simple Mail Transfer Protocol (SMTP) - TCP Port 25 Post Office Protocol (POP) - UDP Port 110 Telnet - TCP Port 23 Dynamic Host Configuration Protocol - UDP Port 67 File Transfer Protocol (FTP) - TCP Ports 20 and 21 ...
Lec9 Networking
... 1st browser – Mosaic – Developed by NCSA National Center for Supercomputer Applications. Launched in 1991 Web browsing surpassed FTP File Transfer Protocol ...
... 1st browser – Mosaic – Developed by NCSA National Center for Supercomputer Applications. Launched in 1991 Web browsing surpassed FTP File Transfer Protocol ...
Review For Final - Eastern Illinois University
... 2. Replace hub Y with a switch. Now, what workstations and servers will receive a copy of a packet if the following workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
... 2. Replace hub Y with a switch. Now, what workstations and servers will receive a copy of a packet if the following workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
Review For Final - Eastern Illinois University
... 2. Replace hub Y with a switch. Now, what workstations and servers will receive a copy of a packet if the following workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
... 2. Replace hub Y with a switch. Now, what workstations and servers will receive a copy of a packet if the following workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
Intro to Wireless Mesh Networks - McMaster Computing and Software
... – If S(X) > S(Y), then X ignores the routing information received from Y – If S(X) = S(Y), and cost of going through Y is smaller than the route known to X, then X sets Y as the next hop to Z – If S(X) < S(Y), then X sets Y as the next hop to Z, and S(X) is updated to equal S(Y) ...
... – If S(X) > S(Y), then X ignores the routing information received from Y – If S(X) = S(Y), and cost of going through Y is smaller than the route known to X, then X sets Y as the next hop to Z – If S(X) < S(Y), then X sets Y as the next hop to Z, and S(X) is updated to equal S(Y) ...
Network Installation Procedure - Chartwell
... and Server Installation when installing) - Register and activate the software (See ‟Guide for license registration and software activation”). - If Cabri II Plus is to be run from client workstations without having to install the software on each computer, ensure that the installation folder is visib ...
... and Server Installation when installing) - Register and activate the software (See ‟Guide for license registration and software activation”). - If Cabri II Plus is to be run from client workstations without having to install the software on each computer, ensure that the installation folder is visib ...
You are entrusted with the design of a network to
... a. You are the administrator of an Ethernet network for dorms on a university campus. There was a sale in town on cheap hardware, where some crappy vendor cheaped out and instead of assigning MAC addresses properly, used the same 40-bit prefix and just cycled through the lower bits. End result: you ...
... a. You are the administrator of an Ethernet network for dorms on a university campus. There was a sale in town on cheap hardware, where some crappy vendor cheaped out and instead of assigning MAC addresses properly, used the same 40-bit prefix and just cycled through the lower bits. End result: you ...
Exam Paper Stationery - University of East Anglia
... -43. (a)(i) Explain the operation of a block interleaver and show how the interleaver is able to reduce the effect of burst-like packet loss when transmitting packets across an unreliable network. [8 marks] (ii) The interleaving function of a block interleaver is given as ...
... -43. (a)(i) Explain the operation of a block interleaver and show how the interleaver is able to reduce the effect of burst-like packet loss when transmitting packets across an unreliable network. [8 marks] (ii) The interleaving function of a block interleaver is given as ...
Internetworking
... • A network is either a directly connected or a switched network that uses one technology. An internetwork is an interconnected collection of such networks. • An internetwork is a logical network built out a collection of physical networks. • An internetwork is often referred to as a “network of net ...
... • A network is either a directly connected or a switched network that uses one technology. An internetwork is an interconnected collection of such networks. • An internetwork is a logical network built out a collection of physical networks. • An internetwork is often referred to as a “network of net ...
GENI Networking Demos
... – External network virtualization (most of this talk) • Combining many networks, or parts of networks, into a virtual unit. ...
... – External network virtualization (most of this talk) • Combining many networks, or parts of networks, into a virtual unit. ...
Solutions
... • 4B/5B encoding solves the problem of long sequences of zeroes but still has issues with long sequences of 1s. o No. 4B/5B uses NRZI to get over the issue of a long series of 1s. • When bandwidth is plenty and errors are rare, error checking may actually add unnecessary overhead. If you interpret t ...
... • 4B/5B encoding solves the problem of long sequences of zeroes but still has issues with long sequences of 1s. o No. 4B/5B uses NRZI to get over the issue of a long series of 1s. • When bandwidth is plenty and errors are rare, error checking may actually add unnecessary overhead. If you interpret t ...
Local Area Networks; Ethernet
... and number of hops to reach them – autonomous system: group of networks under single authority – passes reachability info to core for use by other autonomous systems – interior gateway protocols exchange routing info within a single AS ...
... and number of hops to reach them – autonomous system: group of networks under single authority – passes reachability info to core for use by other autonomous systems – interior gateway protocols exchange routing info within a single AS ...
Internet Vulnerabilities & Criminal Activities
... – All data represented by only 2 signals – 0’s and 1’s for representation ...
... – All data represented by only 2 signals – 0’s and 1’s for representation ...
Evolution of Data Networks - Electrical & Computer
... • There is no round trip time delay waiting for connection setup; a host can send data as soon as it is ready. • Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. • Since packets are treated independently , it is possible to rou ...
... • There is no round trip time delay waiting for connection setup; a host can send data as soon as it is ready. • Source host has no way of knowing if the network is capable of delivering a packet or if the destination host is even up. • Since packets are treated independently , it is possible to rou ...
Networking BASICS
... demand priority channel access method instead of CSMA/CD. This means that when a device needs to transmit a packet, it must first send a request to the hub and then wait for permission before transmitting. Unlike CSMA/CD, demand priority prevents collisions that slow down the network. Another advant ...
... demand priority channel access method instead of CSMA/CD. This means that when a device needs to transmit a packet, it must first send a request to the hub and then wait for permission before transmitting. Unlike CSMA/CD, demand priority prevents collisions that slow down the network. Another advant ...
CSC 311 Fragmentation
... address system is inefficient, many addresses are wasted and we are starting to run out. Using the smaller class C addresses increases the number of network addresses that routers must deal with, thereby complicating the routing problem. ...
... address system is inefficient, many addresses are wasted and we are starting to run out. Using the smaller class C addresses increases the number of network addresses that routers must deal with, thereby complicating the routing problem. ...
Introduction to Multimedia Systems
... direct/indirect router interface number --------------------------------------------------------------------development direct
...
... direct/indirect router interface number --------------------------------------------------------------------development direct
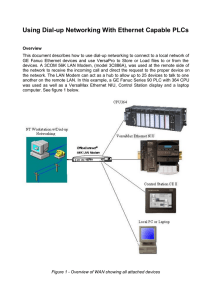
Using Dial-up Networking With Ethernet Capable PLCs
... network do not support DHCP, (such as the CPU364), DHCP was enabled so that a technician with a laptop can just connect to the network without having to first assign him or herself an IP address. Next, connect the ControlStation to the LAN Modem and give it an IP Address of 192.168.1.4, a Subnet Add ...
... network do not support DHCP, (such as the CPU364), DHCP was enabled so that a technician with a laptop can just connect to the network without having to first assign him or herself an IP address. Next, connect the ControlStation to the LAN Modem and give it an IP Address of 192.168.1.4, a Subnet Add ...
ppt
... services 5.2 Error detection and correction 5.3Multiple access protocols 5.4 Link-Layer Addressing (ARP) 5.5 Ethernet ...
... services 5.2 Error detection and correction 5.3Multiple access protocols 5.4 Link-Layer Addressing (ARP) 5.5 Ethernet ...
FSP 150CC-T3204 - ADVA Optical Networking
... Our FSP 150CC-T3204 provides Carrier Ethernet 2.0 service extension over one or two bonded T3 or E3 facilities with up to 89Mbit/s or 68Mbit/s, respectively. With four Ethernet service ports and advanced servicedefinition capabilities, the FSP 150CC-T3204 is capable of supporting multiple services o ...
... Our FSP 150CC-T3204 provides Carrier Ethernet 2.0 service extension over one or two bonded T3 or E3 facilities with up to 89Mbit/s or 68Mbit/s, respectively. With four Ethernet service ports and advanced servicedefinition capabilities, the FSP 150CC-T3204 is capable of supporting multiple services o ...
06-ethernet_sh
... How can we tell which type (DIX or 802.3) frame we received? Look at 2 bytes after MAC fields in the received Ethernet frame: •If this 2 byte field < 1500 this is a valid length and we have an 802.3 frame. Since this is 802.3 we have a “Logical Link Control (LLC) subnetwork attachment point (SNAP) H ...
... How can we tell which type (DIX or 802.3) frame we received? Look at 2 bytes after MAC fields in the received Ethernet frame: •If this 2 byte field < 1500 this is a valid length and we have an 802.3 frame. Since this is 802.3 we have a “Logical Link Control (LLC) subnetwork attachment point (SNAP) H ...
lecture9
... protocol in use today, although there are some questions about its capability to serve the Internet community much longer. IPv4 was finished in the 1970s and has started to show its age. The main issue surrounding IPv4 is addressing—or, the lack of addressing—because many experts believe that we are ...
... protocol in use today, although there are some questions about its capability to serve the Internet community much longer. IPv4 was finished in the 1970s and has started to show its age. The main issue surrounding IPv4 is addressing—or, the lack of addressing—because many experts believe that we are ...
communicate
... There are three key performance reasons for persistent connections: • connection setup overhead • TCP slow start: just do it and get it over with • pipelining as an alternative to multiple connections And some new complexities resulting from their use, e.g.: • request/response framing and pairing • ...
... There are three key performance reasons for persistent connections: • connection setup overhead • TCP slow start: just do it and get it over with • pipelining as an alternative to multiple connections And some new complexities resulting from their use, e.g.: • request/response framing and pairing • ...