Storage Management for Files of Dynamic Records
... There are two difficulties in managing dynamic records on disk. The first is that they vary in length. The second is that each record can change in length over time. We propose a space management scheme in which records are stored in large, fixed-length blocks3 . In this scheme, records are numbered ...
... There are two difficulties in managing dynamic records on disk. The first is that they vary in length. The second is that each record can change in length over time. We propose a space management scheme in which records are stored in large, fixed-length blocks3 . In this scheme, records are numbered ...
The R+-Tree: A Dynamic Index for Multi
... Methods that divide the original space into appropriate sub-regions (overlapping or disjoint). If the regions are disjoint, any of the methods for points that we mentioned before, can be used to decompose the space. The only complication to be handled is that a rectangle may intersect a splitting hy ...
... Methods that divide the original space into appropriate sub-regions (overlapping or disjoint). If the regions are disjoint, any of the methods for points that we mentioned before, can be used to decompose the space. The only complication to be handled is that a rectangle may intersect a splitting hy ...
Starting Out with C++, 3 rd Edition
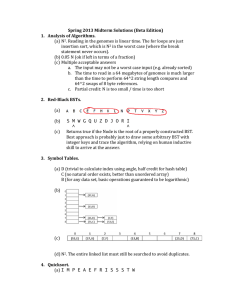
... • There are two possible situations when we are deleting a non-leaf node: – A) the node has one child, or – B) the node has two children. ...
... • There are two possible situations when we are deleting a non-leaf node: – A) the node has one child, or – B) the node has two children. ...
Probabilistic Data Structures for Priority Queues
... x.minsibling will point to the minimum node in y∈sib(x) DescSet(y). This will cause slight modifications in Delete and DeleteMin operations. Every time a node is removed from the sibling linked list of a base node, the minsibling pointer of the base node will be updated using the Bdescendant pointers ...
... x.minsibling will point to the minimum node in y∈sib(x) DescSet(y). This will cause slight modifications in Delete and DeleteMin operations. Every time a node is removed from the sibling linked list of a base node, the minsibling pointer of the base node will be updated using the Bdescendant pointers ...
ch17d-draw
... The algorithm to display a tree is a two step process. 1. The first step uses the recursive function buildShadowTree() to carry out an inorder scan of the tree which creates a second tree, called a shadow tree. Its nodes store the value of the node in the original tree formatted as a string and the ...
... The algorithm to display a tree is a two step process. 1. The first step uses the recursive function buildShadowTree() to carry out an inorder scan of the tree which creates a second tree, called a shadow tree. Its nodes store the value of the node in the original tree formatted as a string and the ...
Document
... filled in (has 2h-2 nodes) and The leaves on the bottom level are as far to the left as possible. ...
... filled in (has 2h-2 nodes) and The leaves on the bottom level are as far to the left as possible. ...
No Slide Title
... that if a node contains a value k, then every node in its left sub-tree contains a value less than k, and every node in its right sub-tree contains a value greater than or equal to k. An important consequence of the above property is that an inorder traversal on a binary tree will always visit the v ...
... that if a node contains a value k, then every node in its left sub-tree contains a value less than k, and every node in its right sub-tree contains a value greater than or equal to k. An important consequence of the above property is that an inorder traversal on a binary tree will always visit the v ...
Chapter2
... Let n be the number of elements in the stack The space used is O(n) Each operation runs in time O(1) ...
... Let n be the number of elements in the stack The space used is O(n) Each operation runs in time O(1) ...
$doc.title
... the remaining data points. P. One can simply use an ordered array (or equivalently, use a trivial hash function which simply returns the key as its own hash). Since there are only 65,536 different ...
... the remaining data points. P. One can simply use an ordered array (or equivalently, use a trivial hash function which simply returns the key as its own hash). Since there are only 65,536 different ...
Indexing and Hashing.key
... pointer, we also store a pointer to the records or bucket for that specific value (since it doesn’t repeat) ...
... pointer, we also store a pointer to the records or bucket for that specific value (since it doesn’t repeat) ...
A Space Efficient Persistent Implementation of an Index for DNA Sequences
... in the subtree below. Thereby the expensive storage of absolute pointers is avoided, which usually requires more memory than the data itself. But also, some of the relative pointers can get quite large. Therefore, in the topmost node the maximal number of 4 Bytes are needed. But, for the most nodes ...
... in the subtree below. Thereby the expensive storage of absolute pointers is avoided, which usually requires more memory than the data itself. But also, some of the relative pointers can get quite large. Therefore, in the topmost node the maximal number of 4 Bytes are needed. But, for the most nodes ...
Peripherals 2 - computing.northampton.ac.uk
... To use the disk has be formatted, the r/w head does under the control of the operating system. During formatting tracks are created on all the area of the disk used for storage, a track can be thought of as being concentric bands on the disk, similar idea to tree rings. Each track into sectors, the ...
... To use the disk has be formatted, the r/w head does under the control of the operating system. During formatting tracks are created on all the area of the disk used for storage, a track can be thought of as being concentric bands on the disk, similar idea to tree rings. Each track into sectors, the ...
OrderedMap with a BST Data Structure - University of Arizona
... Binary Search Trees A Binary Search Tree (BST) data structure is a binary tree with an ordering property BSTs are used to maintain order and faster retrieval, insertion, and removal of individual elements A Binary Search Tree (BST) is ...
... Binary Search Trees A Binary Search Tree (BST) data structure is a binary tree with an ordering property BSTs are used to maintain order and faster retrieval, insertion, and removal of individual elements A Binary Search Tree (BST) is ...
B-tree
In computer science, a B-tree is a tree data structure that keeps data sorted and allows searches, sequential access, insertions, and deletions in logarithmic time. The B-tree is a generalization of a binary search tree in that a node can have more than two children (Comer 1979, p. 123). Unlike self-balancing binary search trees, the B-tree is optimized for systems that read and write large blocks of data. B-trees are a good example of a data structure for external memory. It is commonly used in databases and filesystems.