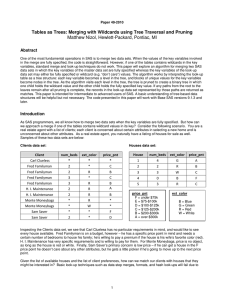
Tables As Trees: Merging with Wildcards Using Tree Traversal and Pruning
... Because a tree structure is typically dynamic and can grow and shrink over time, programmers traditionally use dynamic memory allocation to store trees. The structure of a single node is determined by the programmer, and then nodes are created and destroyed on an as-needed basis during program run-t ...
... Because a tree structure is typically dynamic and can grow and shrink over time, programmers traditionally use dynamic memory allocation to store trees. The structure of a single node is determined by the programmer, and then nodes are created and destroyed on an as-needed basis during program run-t ...
Prefix Based Numbering Schemes for XML: Techniques
... designed to determine the parent-child relationship between two given nodes. The major advantages of bit-vector schemes are that (i) the decision process uses a bit comparison and runs in constant time, and (ii) the construction time is linear. However, bit-vector schemes are inappropriate for vario ...
... designed to determine the parent-child relationship between two given nodes. The major advantages of bit-vector schemes are that (i) the decision process uses a bit comparison and runs in constant time, and (ii) the construction time is linear. However, bit-vector schemes are inappropriate for vario ...
Scapegoat and Splay Trees
... First let’s consider the simple case where we start with a perfectly-balanced tree, and we only want to perform searches and deletions. To get good search and delete times, we can use a technique called global rebuilding. When we get a delete request, we locate and mark the node to be deleted, but w ...
... First let’s consider the simple case where we start with a perfectly-balanced tree, and we only want to perform searches and deletions. To get good search and delete times, we can use a technique called global rebuilding. When we get a delete request, we locate and mark the node to be deleted, but w ...
PPT - UNSW
... An algorithm is a finite sequence of well-defined instructions for solving a problem and guaranteed to terminate in a finite time. An algorithm does not necessarily need to be executable in a computer, but can be converted into a program. ...
... An algorithm is a finite sequence of well-defined instructions for solving a problem and guaranteed to terminate in a finite time. An algorithm does not necessarily need to be executable in a computer, but can be converted into a program. ...
Time and location: COS 226 Midterm Review Fall 2015
... – Add(item) - decrement the counter and add the node to a LLRB with the new counter. The new one is the smallest and supposed to be the left most element in LLRB – Decrementing the priority of all others is implicit. Explicit do not work as it would require N time to do this. – Move to front(index i ...
... – Add(item) - decrement the counter and add the node to a LLRB with the new counter. The new one is the smallest and supposed to be the left most element in LLRB – Decrementing the priority of all others is implicit. Explicit do not work as it would require N time to do this. – Move to front(index i ...
McBride-ICFP-2014-How-to-keep-your-neighbours-in
... David Turner [17] notes that whilst quicksort is often cited as a program which defies structural recursion, it performs the same sorting algorithm (although not with the same memory usage pattern) as building a binary search tree and then flattening it. The irony is completed by noting that the lat ...
... David Turner [17] notes that whilst quicksort is often cited as a program which defies structural recursion, it performs the same sorting algorithm (although not with the same memory usage pattern) as building a binary search tree and then flattening it. The irony is completed by noting that the lat ...
breadth-first traversal
... moves out from those nodes to all nodes two edges away from the start. This continues until either the goal node is found or the entire tree is searched. 2. Characteristics of breadth-first algorithm Breadth-first search is complete; It will find a solution if one exists. But it is neither optim ...
... moves out from those nodes to all nodes two edges away from the start. This continues until either the goal node is found or the entire tree is searched. 2. Characteristics of breadth-first algorithm Breadth-first search is complete; It will find a solution if one exists. But it is neither optim ...
Relativistic Red-Black Trees - PDXScholar
... the tree. This is possible because if prev(new-node) is an internal node, then from the observation above, the new node must be a leaf. If prev(new-node) is a leaf, the new node will be a child of that node on an empty branch. The insert may leave the tree unbalanced. If so, restructures or recolors ...
... the tree. This is possible because if prev(new-node) is an internal node, then from the observation above, the new node must be a leaf. If prev(new-node) is a leaf, the new node will be a child of that node on an empty branch. The insert may leave the tree unbalanced. If so, restructures or recolors ...
Parallel Euler tour and Post Ordering for Parallel Tree Accumulations
... The Euler tour is a traversal of a graph such that each edge of this graph is visited exactly once. The Euler tour technique is essential for different parallel computations on graphs. For example, computing the post order of the tree which is equivalent to conducting a depth first search is inheren ...
... The Euler tour is a traversal of a graph such that each edge of this graph is visited exactly once. The Euler tour technique is essential for different parallel computations on graphs. For example, computing the post order of the tree which is equivalent to conducting a depth first search is inheren ...
B-tree
In computer science, a B-tree is a tree data structure that keeps data sorted and allows searches, sequential access, insertions, and deletions in logarithmic time. The B-tree is a generalization of a binary search tree in that a node can have more than two children (Comer 1979, p. 123). Unlike self-balancing binary search trees, the B-tree is optimized for systems that read and write large blocks of data. B-trees are a good example of a data structure for external memory. It is commonly used in databases and filesystems.