Systems Programming 8 (Connection
... Ethernet: may lose packets, detects corruption ATM: can lose packets, detects corruption & makes reordering less likely ...
... Ethernet: may lose packets, detects corruption ATM: can lose packets, detects corruption & makes reordering less likely ...
emc165_internet - Computer Science & Engineering
... Every machine on the Internet has a unique underlying number, called an IP address. The IP stands for Internet Protocol which is the language that computers use to communicate over the Internet. A protocol is a pre-defined way that someone who wants to use a service talks with that service. That som ...
... Every machine on the Internet has a unique underlying number, called an IP address. The IP stands for Internet Protocol which is the language that computers use to communicate over the Internet. A protocol is a pre-defined way that someone who wants to use a service talks with that service. That som ...
Key Contacts
... The CREST network consists of hardware and wireless connectivity. All PCs internal to CREST are either hardwired (most) and several are wireless (mostly laptops). The Wireless network is secured with WEP encryption thru the network router provided by the internet provider. The WEP key is distributed ...
... The CREST network consists of hardware and wireless connectivity. All PCs internal to CREST are either hardwired (most) and several are wireless (mostly laptops). The Wireless network is secured with WEP encryption thru the network router provided by the internet provider. The WEP key is distributed ...
Planning and Configuring Routing and Switching
... 70-293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network ...
... 70-293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network ...
Client-Server - EECS Instructional Support Group Home Page
... – One node plays the role of “coordinator” – Phase 1, coordinator sends out a request to commit » each participant responds with yes or no ...
... – One node plays the role of “coordinator” – Phase 1, coordinator sends out a request to commit » each participant responds with yes or no ...
Dynamic Host Configuration Protocol
... • Windows clients can register their own A records but they still rely on the DHCP server to create reverse lookup records ...
... • Windows clients can register their own A records but they still rely on the DHCP server to create reverse lookup records ...
Design and Implementation of
... Receives Data CID or Packet type for new connections from packet classifier Make decisions for generating MPDUs Give inputs to timing mechanism ...
... Receives Data CID or Packet type for new connections from packet classifier Make decisions for generating MPDUs Give inputs to timing mechanism ...
... A SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN requests to a target's system. A malicious client can skip sending this last ACK message. Or by spoofing the source IP address in the SYN, it makes the server send the SYN-ACK to the falsified IP address ...
DCE (distributed computing environment)
... automatically handle data type conversions between the client and the server without considering whether they run on the same or different architecture, or have same or different byte ordering. ...
... automatically handle data type conversions between the client and the server without considering whether they run on the same or different architecture, or have same or different byte ordering. ...
class1
... Goal: Reliable data transfer between end systems Handshaking: connection establishment Setup (prepare for) data transfer ahead of time Hello, hello back human protocol Set up “state” in two communicating hosts ...
... Goal: Reliable data transfer between end systems Handshaking: connection establishment Setup (prepare for) data transfer ahead of time Hello, hello back human protocol Set up “state” in two communicating hosts ...
9-0 Internet Protocol Attacks and some Defenses
... If attacker can guess current sequence number for an existing connection, can send Reset packet to close it • With 32-bit sequence numbers, probability of guessing correctly is 1/232 (not practical) • Most systems accept large windows of sequence numbers much higher probability of success – Need ...
... If attacker can guess current sequence number for an existing connection, can send Reset packet to close it • With 32-bit sequence numbers, probability of guessing correctly is 1/232 (not practical) • Most systems accept large windows of sequence numbers much higher probability of success – Need ...
About the Presentations - SUNYIT Computer Science
... – Installing, configuring, troubleshooting network server and client hardware and software – Understanding characteristics of transmission media – Understanding network design – Understanding network protocols – Understanding how users interact with network – Constructing a network with clients, ser ...
... – Installing, configuring, troubleshooting network server and client hardware and software – Understanding characteristics of transmission media – Understanding network design – Understanding network protocols – Understanding how users interact with network – Constructing a network with clients, ser ...
Presentation
... – Require a password – Set a minimum password length – Require that a password is changed within a specified interval – Require that a new password is used each time the old one is changed Chapter 9 ...
... – Require a password – Set a minimum password length – Require that a password is changed within a specified interval – Require that a new password is used each time the old one is changed Chapter 9 ...
VPN - Virtual Private Network
... VPN stands for "Virtual Private Network". The VPN client is software that allows an encrypted, secure and authenticated connection from remote locations to the ETH network. Once the connection is established, you get an ETH Zurich IP address. ...
... VPN stands for "Virtual Private Network". The VPN client is software that allows an encrypted, secure and authenticated connection from remote locations to the ETH network. Once the connection is established, you get an ETH Zurich IP address. ...
About the Presentations
... – Installing, configuring, troubleshooting network server and client hardware and software – Understanding characteristics of transmission media – Understanding network design – Understanding network protocols – Understanding how users interact with network – Constructing a network with clients, ser ...
... – Installing, configuring, troubleshooting network server and client hardware and software – Understanding characteristics of transmission media – Understanding network design – Understanding network protocols – Understanding how users interact with network – Constructing a network with clients, ser ...
... machine. It attacks on operating systems and cause serious crashes because of error in their TCP/IP packet header. Nuke Attack: Another type of DoS attack is Nuke which targeted on internet .It consists of invalid ICMP packets or fragmented packets which sent to the targeted system. This is achieved ...
Exam 70-681
... Active Directory domain named ABC Company.com. All servers on the network run Windows Server 2008 R2 and all client computers run Windows 7 Enterprise. The domain includes two domain controllers named CK-DC1 and CK-DC2. You are planning the deployment of Windows 7 and several applications to 40 new ...
... Active Directory domain named ABC Company.com. All servers on the network run Windows Server 2008 R2 and all client computers run Windows 7 Enterprise. The domain includes two domain controllers named CK-DC1 and CK-DC2. You are planning the deployment of Windows 7 and several applications to 40 new ...
Lecture 2 - University of Delaware
... switching is better than circuit switching. • If usage is very regular (e.g. TV!), circuit switching is best. • If losses and delay are not permissible, then circuit switching is best (e.g., remote controlled surgery). • With packet switching, congestion control is required. Also, there is more over ...
... switching is better than circuit switching. • If usage is very regular (e.g. TV!), circuit switching is best. • If losses and delay are not permissible, then circuit switching is best (e.g., remote controlled surgery). • With packet switching, congestion control is required. Also, there is more over ...
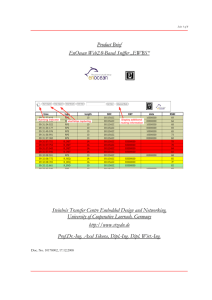
Datasheet - EnOcean Alliance
... get the telegrams from the sniffer in an efficient way since not all files have to be fetched from the server on refresh but only the telegram data.. This data is then interpreted and presented in a table structure, where it can easily be sorted, filtered or exported. Additionally all operations are ...
... get the telegrams from the sniffer in an efficient way since not all files have to be fetched from the server on refresh but only the telegram data.. This data is then interpreted and presented in a table structure, where it can easily be sorted, filtered or exported. Additionally all operations are ...
Internet Secure Protocols
... If a node is unreachable from the outside then the node is almost (but not quite) as safe as a node disconnected from the net. Internal routers should not advertise paths to such nodes to the outside. Filter routes learned from the outside: ...
... If a node is unreachable from the outside then the node is almost (but not quite) as safe as a node disconnected from the net. Internal routers should not advertise paths to such nodes to the outside. Filter routes learned from the outside: ...
Nessus
... Vulnerability found on port http (80/tcp) The remote WebDAV server may be vulnerable to a buffer overflow when it receives a too long request. ...
... Vulnerability found on port http (80/tcp) The remote WebDAV server may be vulnerable to a buffer overflow when it receives a too long request. ...
Lag
In online gaming, lag is a noticeable delay between the action of players and the reaction of the server. Although lag may be caused by high latency, it may also occur due to insufficient processing power in the client(Screen-lag). Screen-Lag can also happened in single player games as well.The tolerance for lag depends heavily on the type of game. For instance, a strategy game or a turn-based game with a low pace may have a high threshold or even be mostly unaffected by high delays, whereas a twitch gameplay game such as a first-person shooter with a considerably higher pace may require significantly lower delay to be able to provide satisfying gameplay. But, the specific characteristics of the game matter. For example, fast chess is a turn-based game that is fast action and may not tolerate high lag. And, some twitch games can be designed such that only events that don't impact the outcome of the game introduce lag, allowing for fast local response most of the time.