EMC Infrastructure for Microsoft Private Cloud
... Today, many organizations have made a decisive move to revamp the existing storage strategy by running critical applications like Microsoft Exchange Server, SharePoint Server, and SQL Server on a virtualized infrastructure. By consolidating application servers on a virtualized platform, customers ca ...
... Today, many organizations have made a decisive move to revamp the existing storage strategy by running critical applications like Microsoft Exchange Server, SharePoint Server, and SQL Server on a virtualized infrastructure. By consolidating application servers on a virtualized platform, customers ca ...
NetVanta 3200 Tolly Group Report
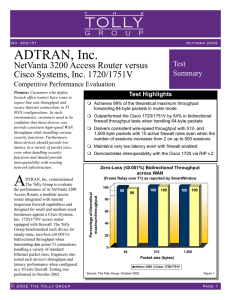
... using the SmartBits SmartWindow and the latency test defined in the RFC 2544 test suite. Traffic was generated at 10% of T1 line rate with 2 sessions running for baseline latency tests. For firewall latency tests, traffic was generated at 10%, 13% and 39% of the T1 line rate, while using 64-, 512- a ...
... using the SmartBits SmartWindow and the latency test defined in the RFC 2544 test suite. Traffic was generated at 10% of T1 line rate with 2 sessions running for baseline latency tests. For firewall latency tests, traffic was generated at 10%, 13% and 39% of the T1 line rate, while using 64-, 512- a ...
Three Challenges in Reliable Data Transport over Heterogeneous
... • Packet radio networks Metricom’s Ricochet, CDPD, etc. Adverse interactions between data and ACK flow ...
... • Packet radio networks Metricom’s Ricochet, CDPD, etc. Adverse interactions between data and ACK flow ...
Representing Information
... Do not know if they are email, streaming video, html web pages Do not know if they are encrypted or unencrypted You can invent your own new service adhering to IP standards Gain Internet’s best-effort service and possibility of undelivered packets ...
... Do not know if they are email, streaming video, html web pages Do not know if they are encrypted or unencrypted You can invent your own new service adhering to IP standards Gain Internet’s best-effort service and possibility of undelivered packets ...
Simple Network Management Protocol (SNMP
... SNMP Agent: used to make KEPServerEX data available to Network Management applications. PingItFirst: free utility installed with KEPServerEX We will focus on SNMP OPC Server and PingItFirst from Kepware for this presentation. These concern the connection from KEPServerEX to the Device, whereas SNMP ...
... SNMP Agent: used to make KEPServerEX data available to Network Management applications. PingItFirst: free utility installed with KEPServerEX We will focus on SNMP OPC Server and PingItFirst from Kepware for this presentation. These concern the connection from KEPServerEX to the Device, whereas SNMP ...
ICS 156: Advanced Computer Networks
... supervision. The time to complete a lab session should be three hours on the average, but may vary. Complete the laboratory activities to the extent that you can. The activities during the lab session are not graded, however, data collected during the lab session are needed to complete a lab report. ...
... supervision. The time to complete a lab session should be three hours on the average, but may vary. Complete the laboratory activities to the extent that you can. The activities during the lab session are not graded, however, data collected during the lab session are needed to complete a lab report. ...
Tech FAQ for Dist 10524A PDF print 2 07
... builder that enables end users to build their own customized reports. Destiny also allows read-only access to all your data from virtually any custom reporting tool such as Microsoft Access, Crystal Reports® and other web-based reporting tools. In addition, the Destiny Custom Reporting Service is av ...
... builder that enables end users to build their own customized reports. Destiny also allows read-only access to all your data from virtually any custom reporting tool such as Microsoft Access, Crystal Reports® and other web-based reporting tools. In addition, the Destiny Custom Reporting Service is av ...
Transmission Control Protocol
... if (timer currently not running) start timer pass segment to IP NextSeqNum = NextSeqNum + length(data) event: timer timeout retransmit not-yet-acknowledged segment with ...
... if (timer currently not running) start timer pass segment to IP NextSeqNum = NextSeqNum + length(data) event: timer timeout retransmit not-yet-acknowledged segment with ...
Mobile Node
... TURN relies on a server that is inserted in the media and signalling path. This TURN server is located either in the customers DMZ or in the Service Provider network. The TURN-enabled SIP client sends an exploratory packet to the TURN server, which responds with the public IP address and port used b ...
... TURN relies on a server that is inserted in the media and signalling path. This TURN server is located either in the customers DMZ or in the Service Provider network. The TURN-enabled SIP client sends an exploratory packet to the TURN server, which responds with the public IP address and port used b ...
Firewall
... • Netfilter is a framework inside Linux kernel which offers flexibility for various networking-related operations to be implemented in form of customized handlers – offers various options for packet filtering, network address translation, and port translation – these functions provide the functional ...
... • Netfilter is a framework inside Linux kernel which offers flexibility for various networking-related operations to be implemented in form of customized handlers – offers various options for packet filtering, network address translation, and port translation – these functions provide the functional ...
firewalls - Faculty Personal Homepage
... It is an advanced packet filter that keeps track of the state of the network connections going through it. Take into account the state of the connection; an incoming packet is matched to its outbound request for the packet to be allowed in. Examine and filter based on packet content; for example, dr ...
... It is an advanced packet filter that keeps track of the state of the network connections going through it. Take into account the state of the connection; an incoming packet is matched to its outbound request for the packet to be allowed in. Examine and filter based on packet content; for example, dr ...
Trace-Driven Analysis of ICN Caching Algorithms on Video-on-Demand Workloads
... rooted in the observation that Internet traffic consumption is largely content driven, as users largely care about “what” content they want as opposed to “where” the content is delivered from. This decoupling promises to simplify several aspects of networking today by eliminating complex optimizatio ...
... rooted in the observation that Internet traffic consumption is largely content driven, as users largely care about “what” content they want as opposed to “where” the content is delivered from. This decoupling promises to simplify several aspects of networking today by eliminating complex optimizatio ...
thesis_talk_mar5
... = e-t/17.26 (t in seconds) half the users will abandon call after 12s 2,566 have at least one outage 946 of 2,566 expected to be dropped 1.53% of all calls ...
... = e-t/17.26 (t in seconds) half the users will abandon call after 12s 2,566 have at least one outage 946 of 2,566 expected to be dropped 1.53% of all calls ...
Chapter 4 Socket Programming Preliminary
... History of Sockets • In early 1980s, the Advanced Research Projects Agency (ARPA) funded a group at UC Berkeley to transport TCP/IP software to the UNIX operating system. • As part of the project, the designers created an interface that applications use for network communication. • The interface us ...
... History of Sockets • In early 1980s, the Advanced Research Projects Agency (ARPA) funded a group at UC Berkeley to transport TCP/IP software to the UNIX operating system. • As part of the project, the designers created an interface that applications use for network communication. • The interface us ...
A Peer-to-Peer based Video broadcast solution
... Since each peer tries to lower its depth, so the probability for (articulation) critical points to occur ...
... Since each peer tries to lower its depth, so the probability for (articulation) critical points to occur ...
Wireless Data Topics
... Virtual IP for host identification; actual IP for routing Address translation in client as well as in NAT Existing protocols like DHCP for signaling Mobility manager to handle nodes in a domain NAT acts as a dynamic home agent Inter-NAT packet flow for inter-domain mobility ...
... Virtual IP for host identification; actual IP for routing Address translation in client as well as in NAT Existing protocols like DHCP for signaling Mobility manager to handle nodes in a domain NAT acts as a dynamic home agent Inter-NAT packet flow for inter-domain mobility ...
thesis-final-pune
... management tools. Various mechanisms and techniques have evolved that bridge the two requirements without much compromise in loss of program organization semantics and the underlying architectural efficiency. But the techniques requiring serious user intervention, such as adapting an application to ...
... management tools. Various mechanisms and techniques have evolved that bridge the two requirements without much compromise in loss of program organization semantics and the underlying architectural efficiency. But the techniques requiring serious user intervention, such as adapting an application to ...
address… - ECSE - Rensselaer Polytechnic Institute
... not other UDP apps when reply is broadcast Does not wake up other servers during broadcast reply Shivkumar Kalyanaraman ...
... not other UDP apps when reply is broadcast Does not wake up other servers during broadcast reply Shivkumar Kalyanaraman ...
A Combined Routing+Queueing Approach to Improving
... those that emphasize speed, for example round-robin schedulers, and those that emphasize fairness, for example timestamp schedulers. In this paper we propose a scheduling algorithm that attempts to bridge the gap between the two. It has very good fairness characteristics, is extremely simple making ...
... those that emphasize speed, for example round-robin schedulers, and those that emphasize fairness, for example timestamp schedulers. In this paper we propose a scheduling algorithm that attempts to bridge the gap between the two. It has very good fairness characteristics, is extremely simple making ...
Slides - SIGMOBILE
... – Ditto design limits applicability Improvements in several wireless scenarios ...
... – Ditto design limits applicability Improvements in several wireless scenarios ...
router`s
... protocol whose address needs to be mapped onto the hardware, for example, IP - 0800. HLEN, Hardware address LENgth (8 bits): This specifies the length in bytes of the hardware address in this packet, for example, Ethernet - 6. PLEN, Protocol address LENgth (8 bits): This specifies the length in byte ...
... protocol whose address needs to be mapped onto the hardware, for example, IP - 0800. HLEN, Hardware address LENgth (8 bits): This specifies the length in bytes of the hardware address in this packet, for example, Ethernet - 6. PLEN, Protocol address LENgth (8 bits): This specifies the length in byte ...
A Robust Push-to-Talk Service for Wireless Mesh Networks
... RTP packets to ensure that the end-node receives it). In our approach, we intercept DTMF signals for control purposes between the end-client and the mesh. For example, a client dials “#12#” to join PTT group 12. In the same way, every time a user wishes to speak, pressing “5” or any pre-defined key ...
... RTP packets to ensure that the end-node receives it). In our approach, we intercept DTMF signals for control purposes between the end-client and the mesh. For example, a client dials “#12#” to join PTT group 12. In the same way, every time a user wishes to speak, pressing “5” or any pre-defined key ...
Kismet Menus - SciTech Connect
... least some settings have been changed from their factory defaults. The red color code is the signature of a network that is using the factory defaults. You may also see the F flag with this network. If the user hasn’t changed the factory configuration, you just might find that they haven’t changed t ...
... least some settings have been changed from their factory defaults. The red color code is the signature of a network that is using the factory defaults. You may also see the F flag with this network. If the user hasn’t changed the factory configuration, you just might find that they haven’t changed t ...
Network Address Translation (NAT) Virtual Private Networks (VPN)
... • Hosts on private IP networks need to access public Internet • All traffic travels through a gateway to/from public Internet • Traffic needs to use IP address of gateway ...
... • Hosts on private IP networks need to access public Internet • All traffic travels through a gateway to/from public Internet • Traffic needs to use IP address of gateway ...
Diapositiva 1 - Gaming Standards Association
... the protocol to participate in the slot network • Event and Meter subscriptions allow a host to subscribe to specific information • Operators can “try out” new products to see if they like them • Products can compete using the same data – e.g. two data mining packages can be connected to the network ...
... the protocol to participate in the slot network • Event and Meter subscriptions allow a host to subscribe to specific information • Operators can “try out” new products to see if they like them • Products can compete using the same data – e.g. two data mining packages can be connected to the network ...
Lag
In online gaming, lag is a noticeable delay between the action of players and the reaction of the server. Although lag may be caused by high latency, it may also occur due to insufficient processing power in the client(Screen-lag). Screen-Lag can also happened in single player games as well.The tolerance for lag depends heavily on the type of game. For instance, a strategy game or a turn-based game with a low pace may have a high threshold or even be mostly unaffected by high delays, whereas a twitch gameplay game such as a first-person shooter with a considerably higher pace may require significantly lower delay to be able to provide satisfying gameplay. But, the specific characteristics of the game matter. For example, fast chess is a turn-based game that is fast action and may not tolerate high lag. And, some twitch games can be designed such that only events that don't impact the outcome of the game introduce lag, allowing for fast local response most of the time.