Securing Cyber Space: Safeguarding Access to Critical Resources Peter Hager, CEO
... New API makes things easy ...
... New API makes things easy ...
Canon Send Error Codes - Electronic Business Machines
... -Check the SMTP server name or IP address. -Check the network status. -Check that the server is up and running. -Check that you have a valid DNS server IP address. -Check that you have the proper email domain name, and the from E-mail address is configured in your machine. -Check that the SMTP serve ...
... -Check the SMTP server name or IP address. -Check the network status. -Check that the server is up and running. -Check that you have a valid DNS server IP address. -Check that you have the proper email domain name, and the from E-mail address is configured in your machine. -Check that the SMTP serve ...
Juniper Networks Secure Access 2000, 4000, and 6000 Appliances
... greatly simplify administration of large diverse user resources, and significantly reduce the number of help desk calls. Feature ...
... greatly simplify administration of large diverse user resources, and significantly reduce the number of help desk calls. Feature ...
VMWARE PUBLIC CLOUD INFRASTRUCTURE – Development environment design and implementation
... and distributed resources. When a cluster is formed of two or more hosts, rapid recovery from a host failure is possible with high availability. ESXi hosts are constantly polled by a vCenter Server to ensure they respond, but hosts also communicate among themselves using a heartbeat signal to ensure ...
... and distributed resources. When a cluster is formed of two or more hosts, rapid recovery from a host failure is possible with high availability. ESXi hosts are constantly polled by a vCenter Server to ensure they respond, but hosts also communicate among themselves using a heartbeat signal to ensure ...
2.1 Use case: Login request
... The purpose of this document is to define user manual and describe use cases of mostly used functional requirements for Natura 2000 Pilot application (N2K). Use case scenarios are designed to follow creating and editing Natura 2000 Standard Data Forms (SDF) for Bosnia and Herzegovina. Additional sce ...
... The purpose of this document is to define user manual and describe use cases of mostly used functional requirements for Natura 2000 Pilot application (N2K). Use case scenarios are designed to follow creating and editing Natura 2000 Standard Data Forms (SDF) for Bosnia and Herzegovina. Additional sce ...
No Slide Title
... the standard and most OMG document are available for public download http://www.omg.org ...
... the standard and most OMG document are available for public download http://www.omg.org ...
Wi-Fi™ Module Product Training
... Click Configure (Note PC’s IP address in Interface box) Set port to 5000 (port number matches remote port of ...
... Click Configure (Note PC’s IP address in Interface box) Set port to 5000 (port number matches remote port of ...
Alteon Stackable Web switches 180 and ACEDirector
... the most available server associated with the destination VIP address specified. It monitors each session from start to finish, providing full address translation as it forwards packets between the client and server. VIP addresses can be administered in blocks, allowing virtually unlimited numbers o ...
... the most available server associated with the destination VIP address specified. It monitors each session from start to finish, providing full address translation as it forwards packets between the client and server. VIP addresses can be administered in blocks, allowing virtually unlimited numbers o ...
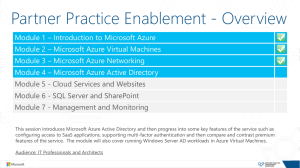
Azure AD
... Module 3 – Microsoft Azure Networking Module 4 – Microsoft Azure Active Directory Module 5 - Cloud Services and Websites Module 6 - SQL Server and SharePoint Module 7 - Management and Monitoring This session introduces Microsoft Azure Active Directory and then progress into some key features of the ...
... Module 3 – Microsoft Azure Networking Module 4 – Microsoft Azure Active Directory Module 5 - Cloud Services and Websites Module 6 - SQL Server and SharePoint Module 7 - Management and Monitoring This session introduces Microsoft Azure Active Directory and then progress into some key features of the ...
P2P-NAT - Universität Freiburg
... Summer 2008address as BBryan does. Applications must therefore authen- points (10.1.1.3:4321, 155.99.25.11:62000) on B’s priChristian Schindelhauer ticate all messages in some way to filter out such stray vate network, and by the endpoints (138.76.29.7:31000, traffic robustly. The messages might inc ...
... Summer 2008address as BBryan does. Applications must therefore authen- points (10.1.1.3:4321, 155.99.25.11:62000) on B’s priChristian Schindelhauer ticate all messages in some way to filter out such stray vate network, and by the endpoints (138.76.29.7:31000, traffic robustly. The messages might inc ...
CentreVu® Explorer
... Toll fraud is the unauthorized use of your telecommunications system by an unauthorized party, for example, persons other than your company’s employees, agents, subcontractors, or persons working on your company’s behalf. Note that there may be a risk of toll fraud associated with your telecommunica ...
... Toll fraud is the unauthorized use of your telecommunications system by an unauthorized party, for example, persons other than your company’s employees, agents, subcontractors, or persons working on your company’s behalf. Note that there may be a risk of toll fraud associated with your telecommunica ...
... E .Classification Results A. Network Layer Attack Generation The network layer attack generation module includes the network layer DDoS attacks such as Port Scanning, TCP Flooding, UDP Flooding, ICMP Flooding, Session Flooding. Here, A Port Scanning: is a software application designed to probe a ser ...
Grid Jobs for Network Monitoring for the Grid
... – Some low-level metrics can’t be implemented in the job Because we have no control of the “Worker Node” environment (hardware, software) where the job is running ...
... – Some low-level metrics can’t be implemented in the job Because we have no control of the “Worker Node” environment (hardware, software) where the job is running ...
Cisco ACS Radius Migration with Huawei
... 2- Create a domain to use the current radius scheme (in our example named “temp”). [Huawei _S5600_SW]domain system [Huawei _S5600_SW-isp-system] scheme radius-scheme temp ...
... 2- Create a domain to use the current radius scheme (in our example named “temp”). [Huawei _S5600_SW]domain system [Huawei _S5600_SW-isp-system] scheme radius-scheme temp ...
Presence
... determined by the availability of communication media but rather by the subscriber’s willingness and ability to communicate. Operators can determine if a subscriber is both willing and able to ...
... determined by the availability of communication media but rather by the subscriber’s willingness and ability to communicate. Operators can determine if a subscriber is both willing and able to ...
IMS Presentation
... • Selects the network in which the interworking with the PSTN/CS Domain is to occur. If the interworking is in another network, then the BGCF will forward the SIP signalling to the BGCF of that network. If the interworking is in another network and network hiding is required by the operator, the BGC ...
... • Selects the network in which the interworking with the PSTN/CS Domain is to occur. If the interworking is in another network, then the BGCF will forward the SIP signalling to the BGCF of that network. If the interworking is in another network and network hiding is required by the operator, the BGC ...
Basic Internetworking
... Each network’s MTU gives the size of the largest IP datagram that can be carried in a link-layer frame. Give the sizes and offsets of the sequence of fragments delivered to the network layer at the destination host. Assume all IP headers are 20 bytes. ...
... Each network’s MTU gives the size of the largest IP datagram that can be carried in a link-layer frame. Give the sizes and offsets of the sequence of fragments delivered to the network layer at the destination host. Assume all IP headers are 20 bytes. ...
Systems Management
... Different info provided on web console and reports. MDM bad integration with devices that have been previously in the platform. When I click on any serial number it sends me to the dell uk website and i am not in the UK and none of these dells are from UK. Wrong time records in the activiry report. ...
... Different info provided on web console and reports. MDM bad integration with devices that have been previously in the platform. When I click on any serial number it sends me to the dell uk website and i am not in the UK and none of these dells are from UK. Wrong time records in the activiry report. ...
Chapter 11 - Information Technology Gate
... In the Authentication Mode drop-down list, select one of the following (cont.): Guest authentication – All connections to the network are regulated by the settings for the Guest user account. This is the least restrictive and most flexible authentication and is recommended when you are creating a ...
... In the Authentication Mode drop-down list, select one of the following (cont.): Guest authentication – All connections to the network are regulated by the settings for the Guest user account. This is the least restrictive and most flexible authentication and is recommended when you are creating a ...
Cisco1Chapter4_ApplicationLayer
... SMTP - Send email from either a client or a server POP - Receive email messages from an email server IMAP - Internet Message Access Protocol Email client provides the functionality of both protocols within one application © 2008 Cisco Systems, Inc. All rights reserved. ...
... SMTP - Send email from either a client or a server POP - Receive email messages from an email server IMAP - Internet Message Access Protocol Email client provides the functionality of both protocols within one application © 2008 Cisco Systems, Inc. All rights reserved. ...
Embedded NGX 6.0 Release Notes
... autonomous system (AS). OSPF chooses the least-cost path as the best path. It is suitable for complex networks with a large number of routers because it provides equal-cost, multi-path routing, where packets to a single destination can be sent via more than one interface simultaneously. In a link-st ...
... autonomous system (AS). OSPF chooses the least-cost path as the best path. It is suitable for complex networks with a large number of routers because it provides equal-cost, multi-path routing, where packets to a single destination can be sent via more than one interface simultaneously. In a link-st ...
ACACIA – Context-aware Edge Computing for Continuous
... human behavior and uses GPU processing to accelerate computation. These efforts have mainly focused on reducing application level computation latency and do not address the networking complexities that arise in realizing such offloading in mobile networks. ACACIA aims to enable these offloading solu ...
... human behavior and uses GPU processing to accelerate computation. These efforts have mainly focused on reducing application level computation latency and do not address the networking complexities that arise in realizing such offloading in mobile networks. ACACIA aims to enable these offloading solu ...
Exam : 070-291 Title : Implementing, Managing, and
... tools that are on the Windows XP CD-ROM. Netcap provides capture abilities that are similar to the version of Network Monitor that is included with the Windows Server products; however, you must use Netcap at a command prompt. Netcap installs the Network Monitor driver and binds it to all adapters w ...
... tools that are on the Windows XP CD-ROM. Netcap provides capture abilities that are similar to the version of Network Monitor that is included with the Windows Server products; however, you must use Netcap at a command prompt. Netcap installs the Network Monitor driver and binds it to all adapters w ...
Hyper-V Cloud Fast Track
... Multiple logical paths with QoS (blade backplanes) 2x (or more) 10GbE 1 GbE management 4 or 8Gb FC or 10Gb based iSCSI SAN boot (blades), local boot (rack) Remote OOB management ...
... Multiple logical paths with QoS (blade backplanes) 2x (or more) 10GbE 1 GbE management 4 or 8Gb FC or 10Gb based iSCSI SAN boot (blades), local boot (rack) Remote OOB management ...