set_9
... Ñ Closed-loop: Deal with congestion when it happens: Use current information about network to deal with congestion. ...
... Ñ Closed-loop: Deal with congestion when it happens: Use current information about network to deal with congestion. ...
Chapter 16
... packets for all available buffers Only waits if no signal arrives before transmission Receiving side Sends ...
... packets for all available buffers Only waits if no signal arrives before transmission Receiving side Sends ...
for TCP
... – Keep number of packets in the network constant. – Don’t inject new packet until old one leaves. ...
... – Keep number of packets in the network constant. – Don’t inject new packet until old one leaves. ...
TCP - Feng Xia
... But after timeout event: CongWin instead set to 1 MSS; window then grows exponentially to a threshold, then grows linearly CongWin ...
... But after timeout event: CongWin instead set to 1 MSS; window then grows exponentially to a threshold, then grows linearly CongWin ...
Wireless Communications and Networks
... The nature of the signals The data rate Other related matters ...
... The nature of the signals The data rate Other related matters ...
Wireless Communications and Networks
... The nature of the signals The data rate Other related matters ...
... The nature of the signals The data rate Other related matters ...
CMPT 880: Internet Architectures and Protocols
... When window is W, throughput is W/RTT Just after loss, window drops to W/2, throughput to W/2RTT Average throughout: 0.75 W/RTT ...
... When window is W, throughput is W/RTT Just after loss, window drops to W/2, throughput to W/2RTT Average throughout: 0.75 W/RTT ...
Slide 1
... to the end of its physical trajectory • The velocity of propagation of the circuit depends mainly on the actual distance of the physical circuit • In the majority of cases this is close to the speed of light. For d = distance, s = propagation velocity ...
... to the end of its physical trajectory • The velocity of propagation of the circuit depends mainly on the actual distance of the physical circuit • In the majority of cases this is close to the speed of light. For d = distance, s = propagation velocity ...
ppt
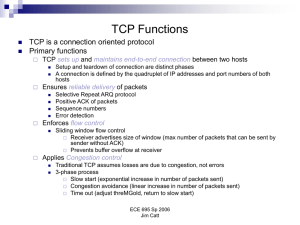
... • TCP uses ACKs (acknowledgement messages), timeouts, and retransmissions for error control • ACK are cumulative • Flow control is implemented by TCP through a sliding window mechanism - The window size is the maximum number of bytes that can be sent before an acknowledgement is received - Window si ...
... • TCP uses ACKs (acknowledgement messages), timeouts, and retransmissions for error control • ACK are cumulative • Flow control is implemented by TCP through a sliding window mechanism - The window size is the maximum number of bytes that can be sent before an acknowledgement is received - Window si ...
Recitation_ECN
... • Use packet drops, as is currently done. • Use specific field in a packet header as an indication of congestion. This has the potential of reducing the impact of loss on latencysensitive flows. AQM drops/indicates packets based on the average queue length exceeding a threshold, rather than only whe ...
... • Use packet drops, as is currently done. • Use specific field in a packet header as an indication of congestion. This has the potential of reducing the impact of loss on latencysensitive flows. AQM drops/indicates packets based on the average queue length exceeding a threshold, rather than only whe ...
lecture14 - Academic Csuohio
... • At loss event, Threshold is set to 1/2 of cwnd just before loss event Fall Semester 2008 ...
... • At loss event, Threshold is set to 1/2 of cwnd just before loss event Fall Semester 2008 ...
part 5
... This didn’t take off, but its interesting to look at, and to see where things stand now ...
... This didn’t take off, but its interesting to look at, and to see where things stand now ...
$doc.title
... b. Ethernet allows for organizations to route traffic hierarchically to end hosts. c. Ethernet switches, like IP routers, use a form of forwarding table to determine which output links to send a p ...
... b. Ethernet allows for organizations to route traffic hierarchically to end hosts. c. Ethernet switches, like IP routers, use a form of forwarding table to determine which output links to send a p ...
Lecture04
... No connection set-up delay UDP sends without establishing a connection No connection state ...
... No connection set-up delay UDP sends without establishing a connection No connection state ...
Factors that influence TCP performance
... Due to latency and packet loss, congestion control mechanisms may be triggered which cause needless reduction in throughput if traditional TCP is utilized in wireless. ECE 695 Sp 2006 Jim Catt ...
... Due to latency and packet loss, congestion control mechanisms may be triggered which cause needless reduction in throughput if traditional TCP is utilized in wireless. ECE 695 Sp 2006 Jim Catt ...
Chapter 20 Transport Protocols
... Segments may arrive out of order Number segments sequentially TCP numbers each octet sequentially Segments are numbered by the first octet number in the segment ...
... Segments may arrive out of order Number segments sequentially TCP numbers each octet sequentially Segments are numbered by the first octet number in the segment ...
network-performance
... to the end of its physical trajectory • The velocity of propagation of the circuit depends mainly on the actual distance of the physical circuit • In the majority of cases this is close to the speed of light. For d = distance, s = propagation velocity ...
... to the end of its physical trajectory • The velocity of propagation of the circuit depends mainly on the actual distance of the physical circuit • In the majority of cases this is close to the speed of light. For d = distance, s = propagation velocity ...
Sender window includes bytes sent but not acknowledged
... Mechanisms for detecting corrupted segments, lost segments, out-of-order segments, and duplicated segments Tools: checksum (corruption), ACK, and time-out (one timeout counter per segment) Lost segment or corrupted segment are the same situation: segment will be retransmitted after time-out (no N ...
... Mechanisms for detecting corrupted segments, lost segments, out-of-order segments, and duplicated segments Tools: checksum (corruption), ACK, and time-out (one timeout counter per segment) Lost segment or corrupted segment are the same situation: segment will be retransmitted after time-out (no N ...
28-roundup
... packets, or both. Can calculate length/distance based on transmission rate and propagation speed. – Messy: propagation speed is media-dependent, low-level protocol details, .. – Minimum packet size is 64 bytes • Cable length ~256 bit times – Example: maximum coax cable length is 2.5 km ...
... packets, or both. Can calculate length/distance based on transmission rate and propagation speed. – Messy: propagation speed is media-dependent, low-level protocol details, .. – Minimum packet size is 64 bytes • Cable length ~256 bit times – Example: maximum coax cable length is 2.5 km ...
Design and performance evaluation of an improved TCP congestion
... the most popular End-to-End transport protocol on the Internet, and it is implemented in several versions (i.e. Tahoe, Reno, Vegas…) all of which aim to improve the network utilization. ...
... the most popular End-to-End transport protocol on the Internet, and it is implemented in several versions (i.e. Tahoe, Reno, Vegas…) all of which aim to improve the network utilization. ...