IP packet filtering Packet filtering
... Stateful packet filtering • Allows for more complex policies based on current state of connections between two machines. – Let incoming UDP packets through only if they are responses to outgoing UDP packets you have seen. – Accept TCP packets with SYN set only as part of TCP connection initiation. ...
... Stateful packet filtering • Allows for more complex policies based on current state of connections between two machines. – Let incoming UDP packets through only if they are responses to outgoing UDP packets you have seen. – Accept TCP packets with SYN set only as part of TCP connection initiation. ...
NetworkingReview
... and data travels over the link at the speed of light 3 × 108 m/s. a. Calculate the minimum RTT for the link. b. Calculate the delay × bandwidth product for the link. c. A camera on the rover takes pictures of its surroundings and sends these to Earth. How quickly after a picture is taken can it reac ...
... and data travels over the link at the speed of light 3 × 108 m/s. a. Calculate the minimum RTT for the link. b. Calculate the delay × bandwidth product for the link. c. A camera on the rover takes pictures of its surroundings and sends these to Earth. How quickly after a picture is taken can it reac ...
final examination - School of Computer Science
... Transport services and protocols ______________ . A) provide logical communication between app processes running on different hosts B) are provided in end systems C) make more than one transport protocol available to applications D) All of the above responses are correct ...
... Transport services and protocols ______________ . A) provide logical communication between app processes running on different hosts B) are provided in end systems C) make more than one transport protocol available to applications D) All of the above responses are correct ...
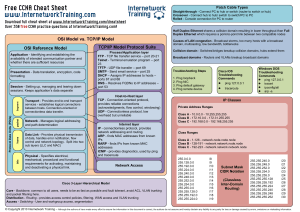
CCNA cheat sheet - Internetwork Training
... Half Duplex Ethernet shares a collision domain resulting in lower throughput than Full Duplex Ethernet which requires a point-to-point link between two compatible nodes ...
... Half Duplex Ethernet shares a collision domain resulting in lower throughput than Full Duplex Ethernet which requires a point-to-point link between two compatible nodes ...
WWW Tutorial - SpaceAgeTimes.com
... » Workstation 1 sends an ARP to ask EA of router if EA of router is not available in ARP cache. » Workstation 1 sends data frame for Workstation 2 to router. » Router sends an ARP to ask EA of Workstation 2. » Router sends Workstation 1‘s data to Workstation 2. ...
... » Workstation 1 sends an ARP to ask EA of router if EA of router is not available in ARP cache. » Workstation 1 sends data frame for Workstation 2 to router. » Router sends an ARP to ask EA of Workstation 2. » Router sends Workstation 1‘s data to Workstation 2. ...
IRIS Project
... • If pattern is 1111111 Whenever the sender sees a sequence of 6 ones in the data, it inserts a zero (reverse this operation at receiver) ...
... • If pattern is 1111111 Whenever the sender sees a sequence of 6 ones in the data, it inserts a zero (reverse this operation at receiver) ...
1-up PPT
... • If pattern is 1111111 Whenever the sender sees a sequence of 6 ones in the data, it inserts a zero (reverse this operation at receiver) ...
... • If pattern is 1111111 Whenever the sender sees a sequence of 6 ones in the data, it inserts a zero (reverse this operation at receiver) ...
High-Performance Data Transfer for Hybrid Optical
... TCP provides reliable transmission of byte streams over best-effort packet networks ...
... TCP provides reliable transmission of byte streams over best-effort packet networks ...
Firewalls
... dest host. Gateway relays data between 2 connections 3. router filter blocks all telnet connections not originating from gateway. ...
... dest host. Gateway relays data between 2 connections 3. router filter blocks all telnet connections not originating from gateway. ...
TCPdump
... flags: S (SYN), F (FIN), P(PUSH), R(RST), . (no flags) Data-seqno: describes the portion of sequence space covered by the data in the packet Ack: sequence number of the next data Window: the number of byte of receive buffer space Urg: indicates there is “urgent” data in the packet Options: tcp optio ...
... flags: S (SYN), F (FIN), P(PUSH), R(RST), . (no flags) Data-seqno: describes the portion of sequence space covered by the data in the packet Ack: sequence number of the next data Window: the number of byte of receive buffer space Urg: indicates there is “urgent” data in the packet Options: tcp optio ...
9/13/2010 Computer Network? The “nuts and bolts” view of the Internet
... ❍ Physical transfer of “bits” from server to client ...
... ❍ Physical transfer of “bits” from server to client ...
Efficient Communication Across the Internet in
... employs a slow-start mechanism for network congestion control. When ACKs do not arrive for packets that were sent out, or when the rate of ACK receipt is very low compared to the rate of sending packets, then TCP assumes congestion in the network and slows down its rate of sending packets. In slow-s ...
... employs a slow-start mechanism for network congestion control. When ACKs do not arrive for packets that were sent out, or when the rate of ACK receipt is very low compared to the rate of sending packets, then TCP assumes congestion in the network and slows down its rate of sending packets. In slow-s ...
ppt - Network and Systems Laboratory
... • nodes – end hosts and less number of routers – homes and local/remote post offices ...
... • nodes – end hosts and less number of routers – homes and local/remote post offices ...
Slide 1
... Analyze and address a number of situations in which security in networks can be compromised. Understand and apply selected technologies used to ensure security. Apply the algorithms behind some current network security protocols. Understand firewalls and their applications.. Demonstrate detailed ...
... Analyze and address a number of situations in which security in networks can be compromised. Understand and apply selected technologies used to ensure security. Apply the algorithms behind some current network security protocols. Understand firewalls and their applications.. Demonstrate detailed ...
Introduction - Computer Sciences User Pages
... • By ’79 the Internet had grown to 200 nodes and by the end of ’89 it had grown to over 100K! – Much growth fueled by connecting universities – L. Landweber from UW was an important part of this! ...
... • By ’79 the Internet had grown to 200 nodes and by the end of ’89 it had grown to over 100K! – Much growth fueled by connecting universities – L. Landweber from UW was an important part of this! ...
Overlay Network and Data Transmission over Wireless
... All these works on multimedia over wireless focus on How to combat with channel error What should we do when packet loss happens But one step back @ what rate should we send multimedia data? Send @ maximum available rate, how? Over wired network: TCP-friendly Over wireless network?.. ...
... All these works on multimedia over wireless focus on How to combat with channel error What should we do when packet loss happens But one step back @ what rate should we send multimedia data? Send @ maximum available rate, how? Over wired network: TCP-friendly Over wireless network?.. ...
PDF Version
... control procedures at the source and loss of throughput. In addition, wireless links have lower bandwidth and are less reliable than wired links. This adversely affects end-to-end performance of transport protocols like TCP. Various solutions have been proposed for this problem. In the split-connect ...
... control procedures at the source and loss of throughput. In addition, wireless links have lower bandwidth and are less reliable than wired links. This adversely affects end-to-end performance of transport protocols like TCP. Various solutions have been proposed for this problem. In the split-connect ...
OSI Model Pyramid - Redbird Internet Services
... ethernet, token ring; FDDI occurs here; devices: brouters, routers. Switches; protocols: HDLC, LLS Flow Control, SLSP & PPP ...
... ethernet, token ring; FDDI occurs here; devices: brouters, routers. Switches; protocols: HDLC, LLS Flow Control, SLSP & PPP ...