The Network Layer
... – Each FA periodically announces its existence and address. The newly-arrived mobile host (MH) waits for one of these messages. If no message is received, it broadcasts a message and asks for FAs. – The MH sends its home address, link layer address, and some security info to the FA. – The FA contrac ...
... – Each FA periodically announces its existence and address. The newly-arrived mobile host (MH) waits for one of these messages. If no message is received, it broadcasts a message and asks for FAs. – The MH sends its home address, link layer address, and some security info to the FA. – The FA contrac ...
Aalborg Universitet
... that reported in [6] at similar settings. The authors conclude that deployment is not a problem, however it is mentioned that throughput for g=32 is the best case, unfortunately no performance for g>32 is presented. In [9] tables are not used for Galois field multiplication, instead the authors impl ...
... that reported in [6] at similar settings. The authors conclude that deployment is not a problem, however it is mentioned that throughput for g=32 is the best case, unfortunately no performance for g>32 is presented. In [9] tables are not used for Galois field multiplication, instead the authors impl ...
Delay- and Disruption-Tolerant Networks (DTNs)
... an alternate link. Packets contain both application-program user data (the payload part) and a header (the control part). The header contains a destination address and other information that determines how the packet is switched from one router to another. The packets in a given message may arrive o ...
... an alternate link. Packets contain both application-program user data (the payload part) and a header (the control part). The header contains a destination address and other information that determines how the packet is switched from one router to another. The packets in a given message may arrive o ...
The Token Based Switch: Per-Packet Access Authorisation to Optical Shortcuts Mihai-Lucian Cristea
... and Y with some sort of token to signal to remote domains that they should be pushed across the optical shortcuts. At the same time, we want to prevent rogue users (e.g., the ISPB client indicated in the figure) to tag their packets with similar tokens to gain unauthorised access to the shortcuts. I ...
... and Y with some sort of token to signal to remote domains that they should be pushed across the optical shortcuts. At the same time, we want to prevent rogue users (e.g., the ISPB client indicated in the figure) to tag their packets with similar tokens to gain unauthorised access to the shortcuts. I ...
Reorder Density (RD): A Formal, Comprehensive Metric for Packet Reordering
... possibly to increased congestion [4]. Approaches for mitigating the impact of out-oforder packet delivery on TCP performance include adjusting ‘dupthresh’ parameter, i.e., the number of duplicate ACKs to be allowed before classifying a following nonacknowledged packet as lost [19]. In delay sensitiv ...
... possibly to increased congestion [4]. Approaches for mitigating the impact of out-oforder packet delivery on TCP performance include adjusting ‘dupthresh’ parameter, i.e., the number of duplicate ACKs to be allowed before classifying a following nonacknowledged packet as lost [19]. In delay sensitiv ...
Internet Technology and Security
... You assume all responsibility for use and potential liability associated with any use of the material. Material contains copyrighted content, used in accordance with U.S. law. Copyright holders of content included in this material should contact [email protected] with any questions, correction ...
... You assume all responsibility for use and potential liability associated with any use of the material. Material contains copyrighted content, used in accordance with U.S. law. Copyright holders of content included in this material should contact [email protected] with any questions, correction ...
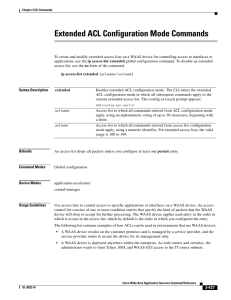
Extended ACL Configuration Mode Commands
... on the chosen protocol. For IP, use the following syntax to add a condition: [insert line-num] deny {gre | icmp | tcp | udp | ip | proto-num} {source-ip [wildcard] | host source-ip | any} {dest-ip [wildcard] | host dest-ip | any} no deny {gre | icmp | tcp | udp | ip | proto-num} {source-ip [wildcard ...
... on the chosen protocol. For IP, use the following syntax to add a condition: [insert line-num] deny {gre | icmp | tcp | udp | ip | proto-num} {source-ip [wildcard] | host source-ip | any} {dest-ip [wildcard] | host dest-ip | any} no deny {gre | icmp | tcp | udp | ip | proto-num} {source-ip [wildcard ...
Secured VPN Models for LTE Backhaul Networks
... during the DDoS attack also. When the numbers of attackers increase, total system down time also increases and system rapidly approaches to zero throughput status. C. Impact of TCP reset attack TCP reset attack is an IP based attack where an attacker sends forge TCP packets to endpoints by setting t ...
... during the DDoS attack also. When the numbers of attackers increase, total system down time also increases and system rapidly approaches to zero throughput status. C. Impact of TCP reset attack TCP reset attack is an IP based attack where an attacker sends forge TCP packets to endpoints by setting t ...
Multimedia Communications
... delay loss: IP datagram arrives too late for playout at receiver ...
... delay loss: IP datagram arrives too late for playout at receiver ...
Chapter 2: Application layer
... How the application is structured over various end systems Client-server Peer-to-peer (P2P) Hybrid of client-server and P2P ...
... How the application is structured over various end systems Client-server Peer-to-peer (P2P) Hybrid of client-server and P2P ...
About the Presentations
... • Common rules for packet filtering: – Drop all inbound connections except connection requests for configured servers – Eliminate packets bound for all ports that should not be available to the Internet – Filter out any ICMP redirect or echo (ping) messages – Drop all packets that use the IP header ...
... • Common rules for packet filtering: – Drop all inbound connections except connection requests for configured servers – Eliminate packets bound for all ports that should not be available to the Internet – Filter out any ICMP redirect or echo (ping) messages – Drop all packets that use the IP header ...
COMET—COMBO Ethernet Tester
... the item can be read. For item that is writeble, we can also change its value. e writeable items are used to control hardware. erefore, this library can be used in other projects that need to read a set of data from the COMBOv2 card. e comstat(1) console application can be used to perform the functi ...
... the item can be read. For item that is writeble, we can also change its value. e writeable items are used to control hardware. erefore, this library can be used in other projects that need to read a set of data from the COMBOv2 card. e comstat(1) console application can be used to perform the functi ...
Security in Computer Networks
... software & hardware implementation ease implementation attacks flexibility (in en/decrypt, keying, other factors) ...
... software & hardware implementation ease implementation attacks flexibility (in en/decrypt, keying, other factors) ...
slides
... then, fill rate = constant rate - packet loss short playout delay (2-5 seconds) to compensate for network delay jitter error recover: time permitting ...
... then, fill rate = constant rate - packet loss short playout delay (2-5 seconds) to compensate for network delay jitter error recover: time permitting ...
Building a Reliable Ethernet/IP Network: GSFC Prototype
... • Application layer: – Rx & tx packet latency through the stack is highly variable and non-deterministic (regardless of direction) – Latency up to several milliseconds on a MCP750 @ 233mhz ...
... • Application layer: – Rx & tx packet latency through the stack is highly variable and non-deterministic (regardless of direction) – Latency up to several milliseconds on a MCP750 @ 233mhz ...
Chapter 2 Lecture Presentation
... IP table at server indicates packet should be sent to router, so IP packet is encapsulated in Ethernet frame with addresses s and r Ethernet frame is broadcast by server NIC and captured by router NIC NIC examines protocol type field and then delivers packet to its IP layer IP layer examines IP pack ...
... IP table at server indicates packet should be sent to router, so IP packet is encapsulated in Ethernet frame with addresses s and r Ethernet frame is broadcast by server NIC and captured by router NIC NIC examines protocol type field and then delivers packet to its IP layer IP layer examines IP pack ...
A Survey on Network Attacks
... computer usage that can't be detected by a conventional firewall. This includes network attacks against vulnerable services, data driven attacks on applications, host based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware (viruses, Trojan horses, a ...
... computer usage that can't be detected by a conventional firewall. This includes network attacks against vulnerable services, data driven attacks on applications, host based attacks such as privilege escalation, unauthorized logins and access to sensitive files, and malware (viruses, Trojan horses, a ...
EURESCOM - SALTAMONTES
... Label stacks allow the creation of nested label switched paths, in which one large LSP uses several smaller LSPs on the way to the destination. MPLS supports LIFO (last in first out) for label stacks. However, now LSRs have to do some more than mapping to
... Label stacks allow the creation of nested label switched paths, in which one large LSP uses several smaller LSPs on the way to the destination. MPLS supports LIFO (last in first out) for label stacks. However, now LSRs have to do some more than mapping
comm3380-slides-week08_PA1
... RIP broadcast from a neighbouring router • If the destination is not in the table, then create a new table entry for it. • If the destination is already in the table via a different route but the received list gives a shorter distance to it, then change the table entry. • If the destination is alre ...
... RIP broadcast from a neighbouring router • If the destination is not in the table, then create a new table entry for it. • If the destination is already in the table via a different route but the received list gives a shorter distance to it, then change the table entry. • If the destination is alre ...
ANALYSIS OF RED PACKET LOSS PERFORMANCE IN A SIMULATED IP WAN
... transmit packets regardless of network conditions, dropping packets without changing its transmission rates. However, TCP traffic flows concern itself with the network condition, reducing the packet transmission rate based on packet loss. Packet loss indicates that a network is congested. The slidin ...
... transmit packets regardless of network conditions, dropping packets without changing its transmission rates. However, TCP traffic flows concern itself with the network condition, reducing the packet transmission rate based on packet loss. Packet loss indicates that a network is congested. The slidin ...
Chapter 7
... network loss: IP datagram lost due to network congestion (router buffer overflow) delay loss: IP datagram arrives too late for playout at receiver delays: processing, queueing in network; endsystem (sender, receiver) delays typical maximum tolerable delay: 400 ms loss tolerance: depending on voi ...
... network loss: IP datagram lost due to network congestion (router buffer overflow) delay loss: IP datagram arrives too late for playout at receiver delays: processing, queueing in network; endsystem (sender, receiver) delays typical maximum tolerable delay: 400 ms loss tolerance: depending on voi ...
Multimedia Networking
... timestamp increases by 160 for each RTP packet when source is active. Timestamp clock continues to increase at constant rate when source is inactive. ...
... timestamp increases by 160 for each RTP packet when source is active. Timestamp clock continues to increase at constant rate when source is inactive. ...
Draft CCNA 3
... Module 11: TCP/IP Transport and Application Layers 11.1 TCP/IP Transport Layer 11.2 TCP/IP Application Layer Case Study: Structured Cabling What has changed from CCNA versions 2.x? More information on optical and wireless More cable testing terminology and concepts More details on the operation of ...
... Module 11: TCP/IP Transport and Application Layers 11.1 TCP/IP Transport Layer 11.2 TCP/IP Application Layer Case Study: Structured Cabling What has changed from CCNA versions 2.x? More information on optical and wireless More cable testing terminology and concepts More details on the operation of ...