Module 09 Presentation
... TFTP is a connectionless service that uses the User Datagram Protocol (UDP). ...
... TFTP is a connectionless service that uses the User Datagram Protocol (UDP). ...
Introduction
... each of which is a separate collision domain. That is, they were designed to create more useable bandwidth. The purpose of a bridge is to filter traffic on a LAN—to keep local traffic local—yet allow connectivity to other parts (segments) of the LAN for traffic that is directed there. You might wond ...
... each of which is a separate collision domain. That is, they were designed to create more useable bandwidth. The purpose of a bridge is to filter traffic on a LAN—to keep local traffic local—yet allow connectivity to other parts (segments) of the LAN for traffic that is directed there. You might wond ...
socks for proxy - Linux Magazine
... conf (Listing 1). In line 1, a logoutput instruction tells Dante where to send the logfiles (Syslog or Stdout). The internal and external network interfaces are specified by interface names in lines 4 and 5. This is useful for computers with a DHCP-based configuration. Lines 6 and 7 show that IP add ...
... conf (Listing 1). In line 1, a logoutput instruction tells Dante where to send the logfiles (Syslog or Stdout). The internal and external network interfaces are specified by interface names in lines 4 and 5. This is useful for computers with a DHCP-based configuration. Lines 6 and 7 show that IP add ...
old_Ch3
... If two routers are attached over a point to point link, this is still considered as a network to the routers, it just does not have any other network devices on it except for the router at the other end. Because of the way the internet has grown, most ASs don’t have a single network ID. They general ...
... If two routers are attached over a point to point link, this is still considered as a network to the routers, it just does not have any other network devices on it except for the router at the other end. Because of the way the internet has grown, most ASs don’t have a single network ID. They general ...
module_42 - Faculty Personal Homepage
... G.711 codec samples 20ms of voice per packet. Therefore, 50 such packets need to be transmitted per second. Each packet contains 160 voice samples in order to give 8000 samples per second. Each packet is sent in one Ethernet frame. With every packet of size 160 bytes, headers of additional proto ...
... G.711 codec samples 20ms of voice per packet. Therefore, 50 such packets need to be transmitted per second. Each packet contains 160 voice samples in order to give 8000 samples per second. Each packet is sent in one Ethernet frame. With every packet of size 160 bytes, headers of additional proto ...
IP address
... A protocol such as IP that defines addresses has an address space. An address space is the total number of addresses available to the protocol. If a protocol uses N bits to define an address, the address space is 2N because each bit can have two different values (0 and 1); N bits can have 2N values. ...
... A protocol such as IP that defines addresses has an address space. An address space is the total number of addresses available to the protocol. If a protocol uses N bits to define an address, the address space is 2N because each bit can have two different values (0 and 1); N bits can have 2N values. ...
NENA Emergency Services IP Network Design for NG9-1
... Many 9-1-1 entities have built, are building, or will build in the near future an Emergency Services IP network (ESInet) to connect PSAPs and other public safety agencies within a region and provide interconnect to other ESInets and originating service providers within a region or state. The effort ...
... Many 9-1-1 entities have built, are building, or will build in the near future an Emergency Services IP network (ESInet) to connect PSAPs and other public safety agencies within a region and provide interconnect to other ESInets and originating service providers within a region or state. The effort ...
M051055
... attached networks. Routers must also discover when their neighbors becomeunreachable or inoperative. This process is achieved with low overhead by periodically sendingsmall hello packets. As long as a router receives hello packets from a neighboring router, itassumes that the neighbor is functioning ...
... attached networks. Routers must also discover when their neighbors becomeunreachable or inoperative. This process is achieved with low overhead by periodically sendingsmall hello packets. As long as a router receives hello packets from a neighboring router, itassumes that the neighbor is functioning ...
EX4500 Ethernet Switch
... parameters found in any router powered by the Junos OS. 2. The EX4500 also includes the integrated Juniper Networks J-Web Software, an embedded web-based device manager that allows users to configure, monitor, troubleshoot, and perform system maintenance on individual switches via a browserbased gra ...
... parameters found in any router powered by the Junos OS. 2. The EX4500 also includes the integrated Juniper Networks J-Web Software, an embedded web-based device manager that allows users to configure, monitor, troubleshoot, and perform system maintenance on individual switches via a browserbased gra ...
Module 2 - OoCities
... Time allowed for the packet to persist in the internet before being discarded by a router or host. Q19: The HTTP protocol allows you to get pages from Internet, and to communicate with the web. (Answer: True). Q20: PPP stands for _______________________. (Point to Point protocol). Note: Point-to-Poi ...
... Time allowed for the packet to persist in the internet before being discarded by a router or host. Q19: The HTTP protocol allows you to get pages from Internet, and to communicate with the web. (Answer: True). Q20: PPP stands for _______________________. (Point to Point protocol). Note: Point-to-Poi ...
ISDN
... Sub addressing (SUB) - The SUB supplementary service permits the called user to expand his addressing capacity beyond the one given by the ISDN number. The sub-addressing information is transparently transported by the network from the calling to the called user and can be used for multi-application ...
... Sub addressing (SUB) - The SUB supplementary service permits the called user to expand his addressing capacity beyond the one given by the ISDN number. The sub-addressing information is transparently transported by the network from the calling to the called user and can be used for multi-application ...
Link-State Routing Protocols
... Link-State Routing Process – step 2 Sending Hello Packets to Neighbors Link state routing protocols use a hello protocol Purpose of a hello protocol: To discover neighbors (that use the same link state routing protocol) on its link ...
... Link-State Routing Process – step 2 Sending Hello Packets to Neighbors Link state routing protocols use a hello protocol Purpose of a hello protocol: To discover neighbors (that use the same link state routing protocol) on its link ...
Communication - Ubiquitous Computing Lab
... -Data link layer: +Deals with detecting and correcting bit transmission errors +Bits are group into frames +Checksums are used for integrity ...
... -Data link layer: +Deals with detecting and correcting bit transmission errors +Bits are group into frames +Checksums are used for integrity ...
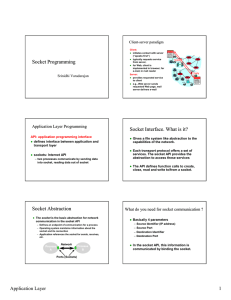
Socket Programming Socket Interface. What is it? Socket Abstraction
... Each transport protocol offers a set of services. The socket API provides the abstraction to access these services ...
... Each transport protocol offers a set of services. The socket API provides the abstraction to access these services ...
Ethernet frames - La Salle University
... takes the signal from or puts the signal onto the transmission line (“touches” physical layer) – The LLC (Logical Link Control) sublayer: starts to interpret the signal as data, includes timing (synchronization) and error checking. CSIT 220 (Blum) ...
... takes the signal from or puts the signal onto the transmission line (“touches” physical layer) – The LLC (Logical Link Control) sublayer: starts to interpret the signal as data, includes timing (synchronization) and error checking. CSIT 220 (Blum) ...
Mobile Communications
... • Protocol of the transport layer within the WAP architecture • uses directly transports mechanisms of different network technologies • offers a common interface for higher layer protocols • allows for transparent communication using different transport technologies (GSM [SMS, CSD, USSD, GPRS, ...], ...
... • Protocol of the transport layer within the WAP architecture • uses directly transports mechanisms of different network technologies • offers a common interface for higher layer protocols • allows for transparent communication using different transport technologies (GSM [SMS, CSD, USSD, GPRS, ...], ...
Document
... Each host computer would be attached to this specialized computer In 1969, the ARPANET was a reality- with four nodes, UCLA, UCSB, Stanford Research Institute, University of Utah. Software used was called Network Control Protocol (NCP). McGraw-Hill ...
... Each host computer would be attached to this specialized computer In 1969, the ARPANET was a reality- with four nodes, UCLA, UCSB, Stanford Research Institute, University of Utah. Software used was called Network Control Protocol (NCP). McGraw-Hill ...
networks
... – Source-based routing: message specifies path to the destination (changes of direction) – Virtual Circuit: circuit established from source to destination, message picks the circuit to follow – Destination-based routing: message specifies destination, switch must pick the path ...
... – Source-based routing: message specifies path to the destination (changes of direction) – Virtual Circuit: circuit established from source to destination, message picks the circuit to follow – Destination-based routing: message specifies destination, switch must pick the path ...
About the Presentations
... • Common rules for packet filtering: – Drop all inbound connections except connection requests for configured servers – Eliminate packets bound for all ports that should not be available to the Internet – Filter out any ICMP redirect or echo (ping) messages – Drop all packets that use the IP header ...
... • Common rules for packet filtering: – Drop all inbound connections except connection requests for configured servers – Eliminate packets bound for all ports that should not be available to the Internet – Filter out any ICMP redirect or echo (ping) messages – Drop all packets that use the IP header ...
Virtual Private Netorks: An Overview
... and more flexible than a network with dedicated connections such as permanent circuits over leased ...
... and more flexible than a network with dedicated connections such as permanent circuits over leased ...
User Guide - Datastorm Users
... the Internet via satellite signals. The DW6000 is independent of operating platforms. Whether your computers use Windows® or MacIntosh® operating systems, they can surf the Internet now that they are connected to the DW6000. Because the satellite access software is on the DW6000, there is no need to ...
... the Internet via satellite signals. The DW6000 is independent of operating platforms. Whether your computers use Windows® or MacIntosh® operating systems, they can surf the Internet now that they are connected to the DW6000. Because the satellite access software is on the DW6000, there is no need to ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).