Wide-Area Ethernet Network Configuration for System
... the full volume of substation IEC 61850 GOOSE traffic published on the network in parallel, as described in the next subsection. Each central controller processor is able to receive or subscribe to all incoming field data on the LAN, and perform its own processing without individual data connections ...
... the full volume of substation IEC 61850 GOOSE traffic published on the network in parallel, as described in the next subsection. Each central controller processor is able to receive or subscribe to all incoming field data on the LAN, and perform its own processing without individual data connections ...
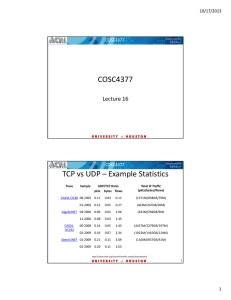
COSC4377 TCP vs UDP – Example Statistics
... routers. Routers advertise prefixes that identify the subnet(s) associated with a link, while hosts generate an "interface identifier" that uniquely identifies an interface on a subnet. An address is formed by combining the two. In the absence of routers, a host can only generate link‐local addre ...
... routers. Routers advertise prefixes that identify the subnet(s) associated with a link, while hosts generate an "interface identifier" that uniquely identifies an interface on a subnet. An address is formed by combining the two. In the absence of routers, a host can only generate link‐local addre ...
PowerPoint - DePaul University
... IP Type of Service Field "The Type of Service provides an indication of the abstract parameters of the quality of service ...
... IP Type of Service Field "The Type of Service provides an indication of the abstract parameters of the quality of service ...
ppt
... • Think twice before implementing functionality in the network • If hosts can implement functionality correctly, implement it in a lower layer only as a performance enhancement • But do so only if it does not impose burden on applications that do not require that functionality ...
... • Think twice before implementing functionality in the network • If hosts can implement functionality correctly, implement it in a lower layer only as a performance enhancement • But do so only if it does not impose burden on applications that do not require that functionality ...
Mobile Node
... existing Firewall/NAT installations to a public address space server. This method requires a new server within the private network and another in the public network. These devices create a tunnel between them that carries all the SIP traffic through a reconfigured Firewall. The external server modif ...
... existing Firewall/NAT installations to a public address space server. This method requires a new server within the private network and another in the public network. These devices create a tunnel between them that carries all the SIP traffic through a reconfigured Firewall. The external server modif ...
Lecture 24: IP Routing
... A-B link goes down, B knows this and looks for another route to A B has route to C and C has route to A – distance 2 + 1(from B)… So update the routing table in B, C, D in this scenario ...
... A-B link goes down, B knows this and looks for another route to A B has route to C and C has route to A – distance 2 + 1(from B)… So update the routing table in B, C, D in this scenario ...
Global Information Systems and Software Technology (GISST)
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
ch_01_Network_Overview - Faculty Web Hosting
... Best known example – a cable TV network. Originally intended for TV only, it quickly became used for computer networks once the cable companies determined that there was money to Jozef Goetz, 2009 be made. ...
... Best known example – a cable TV network. Originally intended for TV only, it quickly became used for computer networks once the cable companies determined that there was money to Jozef Goetz, 2009 be made. ...
Distance Vector Routing Protocols
... seconds for RIP and 90 seconds for IGRP). – Even if the topology has not changed in several days, periodic updates continue to be sent to all neighbors. – Neighbors are routers that share a link and are configured to use the same routing protocol. – The router is only aware of the network addresses ...
... seconds for RIP and 90 seconds for IGRP). – Even if the topology has not changed in several days, periodic updates continue to be sent to all neighbors. – Neighbors are routers that share a link and are configured to use the same routing protocol. – The router is only aware of the network addresses ...
Cisco QoS Notes - The Cisco Learning Network
... By default, Cisco IOS devices that use Tunnel interfaces copy the ToS byte from the IP header of Packets and attach them to the ToS byte of the Tunnel Headers before put on the VPN. QoS Preclassify: Used when you want to classify traffic not based on the ToS Byte / DSCP markings as they traverse a t ...
... By default, Cisco IOS devices that use Tunnel interfaces copy the ToS byte from the IP header of Packets and attach them to the ToS byte of the Tunnel Headers before put on the VPN. QoS Preclassify: Used when you want to classify traffic not based on the ToS Byte / DSCP markings as they traverse a t ...
Multiprotocol Label Switching (MPLS)
... • BGP-Free Core • The peer-to-peer model for MPLS VPN • Optimal Traffic Flow • Traffic Engineering ...
... • BGP-Free Core • The peer-to-peer model for MPLS VPN • Optimal Traffic Flow • Traffic Engineering ...
document
... global Internet may not be scalable in the long term • An Internet-wide replacement of IPv4 with ipv6 represents a one-in-a-generation opportunity to either continue current trends or to deploy something truly innovative and sustainable • As currently specified, routing and addressing with ipv6 does ...
... global Internet may not be scalable in the long term • An Internet-wide replacement of IPv4 with ipv6 represents a one-in-a-generation opportunity to either continue current trends or to deploy something truly innovative and sustainable • As currently specified, routing and addressing with ipv6 does ...
module21-mcast
... who has joined the multicast group • If an application is terminated, the multicast address is (implicitly) released. ...
... who has joined the multicast group • If an application is terminated, the multicast address is (implicitly) released. ...
Measurement-based models enable predictable wireless behavior
... • Interference range is twice the transmission range ...
... • Interference range is twice the transmission range ...
Efficiency through Eavesdropping: Link-layer Packet Caching
... The key contributions of the current work are the design of RTS-id and a backwards-compatible implementation on a real 802.11 hardware platform, CalRadio. We show that RTS-id can decrease air time usage by 25.2% when two nodes communicate to each other through an access point in our testbed. Moreove ...
... The key contributions of the current work are the design of RTS-id and a backwards-compatible implementation on a real 802.11 hardware platform, CalRadio. We show that RTS-id can decrease air time usage by 25.2% when two nodes communicate to each other through an access point in our testbed. Moreove ...
Broadband Router with built-in ADSL Modem
... computer or other electronic device to send any message via a telephone facsimile machine unless such message clearly contains, in a margin at the top or bottom of each transmitted page or on the first page of the transmission the date and time it is sent and an identification of the business, other ...
... computer or other electronic device to send any message via a telephone facsimile machine unless such message clearly contains, in a margin at the top or bottom of each transmitted page or on the first page of the transmission the date and time it is sent and an identification of the business, other ...
slides
... • XML class model, specified in UML 2.0, is used for modeling • Separation of “application” development from the lower levels integration (Basic SoftwareBSW) • The separator: Runtime environment (RTE) – RTE uses Virtual Functional Bus (VFB) as abstracting communication principle • No need to know wh ...
... • XML class model, specified in UML 2.0, is used for modeling • Separation of “application” development from the lower levels integration (Basic SoftwareBSW) • The separator: Runtime environment (RTE) – RTE uses Virtual Functional Bus (VFB) as abstracting communication principle • No need to know wh ...
Aalborg Universitet Morten Videbæk
... of g packets (each batch is called a generation). For each generation, the source generates coded packets using random linear network coding, then it stores them in the MAC layer queue. Once the coded packets are buffered in the MAC queue for transmission, they cannot be removed from the MAC queue b ...
... of g packets (each batch is called a generation). For each generation, the source generates coded packets using random linear network coding, then it stores them in the MAC layer queue. Once the coded packets are buffered in the MAC queue for transmission, they cannot be removed from the MAC queue b ...
"Anonymous Gossip: Improving Multicast Reliability in Mobile Ad-Hoc Networks"
... associated with a nexthop contains the distance to the nearest group member from this node by taking the link through this nexthop node. This adds very little overhead to the existing multicast route table. Whenever a gossip message is received, a nexthop node is chosen so that a nexthop with a smal ...
... associated with a nexthop contains the distance to the nearest group member from this node by taking the link through this nexthop node. This adds very little overhead to the existing multicast route table. Whenever a gossip message is received, a nexthop node is chosen so that a nexthop with a smal ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).