P10 AMHS Transition Plan for CARSAM Region Hoang Tran
... IPv4 in separate sub-regions. Two of these sub-regions are interconnected via IPv6 using a network address and protocol translation technique whereby IPv4 messages are converted to IPv6 across the interface and then back to IPv4. ...
... IPv4 in separate sub-regions. Two of these sub-regions are interconnected via IPv6 using a network address and protocol translation technique whereby IPv4 messages are converted to IPv6 across the interface and then back to IPv4. ...
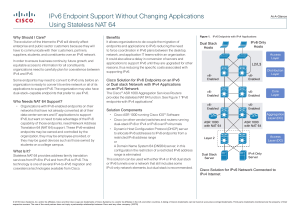
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... © 2010 Cisco Systems, Inc. and/or its affiliates. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of th ...
... © 2010 Cisco Systems, Inc. and/or its affiliates. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of th ...
Protection And Restoration In MPLS Networks
... and managing core networks. The networks may be data-centric like those of ISPs, voice-centric like those of traditional telecommunications companies, or one of the modern networks that combine voice and data. These networks are converging on a model that uses the Internet Protocol (IP) to transport ...
... and managing core networks. The networks may be data-centric like those of ISPs, voice-centric like those of traditional telecommunications companies, or one of the modern networks that combine voice and data. These networks are converging on a model that uses the Internet Protocol (IP) to transport ...
Ethernet POWERLINK (DRAFT)
... slot is available for non-POWERLINK frames. UDP/IP is the preferred data exchange mechanism in the asynchronous slot; however, it is possible to use any protocol. [2, page 40, ...
... slot is available for non-POWERLINK frames. UDP/IP is the preferred data exchange mechanism in the asynchronous slot; however, it is possible to use any protocol. [2, page 40, ...
CCNA5.0 Instructor PPT - Bina Darma e
... • Dedicate part of a routers resources for protocol operation, including CPU time and network link bandwidth Times when static routing is more appropriate Presentation_ID ...
... • Dedicate part of a routers resources for protocol operation, including CPU time and network link bandwidth Times when static routing is more appropriate Presentation_ID ...
IPv6
... Address registries for IPv6 are the same one as for IPv4, ARIN,RIPE and APNIC. • Only large network providers will ever obtain addresses directly from the registries, such as UNINET : one such provider in Thailand • If a /35 prefix is allocates, the registry internally will reserve a /32. • The basi ...
... Address registries for IPv6 are the same one as for IPv4, ARIN,RIPE and APNIC. • Only large network providers will ever obtain addresses directly from the registries, such as UNINET : one such provider in Thailand • If a /35 prefix is allocates, the registry internally will reserve a /32. • The basi ...
Guide to TCP/IP, Third Edition
... What is NetBIOS (and Why Do I care) • NetBIOS operates by – Maintaining a list of unique names assigned to network resources – Providing the services to establish, defend, and resolve these names – Carrying the needed communications between applications that make use of these network resources ...
... What is NetBIOS (and Why Do I care) • NetBIOS operates by – Maintaining a list of unique names assigned to network resources – Providing the services to establish, defend, and resolve these names – Carrying the needed communications between applications that make use of these network resources ...
Chapter 1
... transmitted within a series of routers without ever reaching its intended destination network. • The loop can be a result of: • Incorrectly configured static routes. • Inconsistent routing tables not being updated because of slow convergence in a changing network. • Distance vector routing protocols ...
... transmitted within a series of routers without ever reaching its intended destination network. • The loop can be a result of: • Incorrectly configured static routes. • Inconsistent routing tables not being updated because of slow convergence in a changing network. • Distance vector routing protocols ...
Quality of Service Networking
... Using policy-based routing, route maps are made to match on certain flow criteria and then set precedence bits when ACLs are matched. The capability to set IP precedence bits should not be confused with PBR’s primary capability: routing packets based on configured policies. Some applications or traf ...
... Using policy-based routing, route maps are made to match on certain flow criteria and then set precedence bits when ACLs are matched. The capability to set IP precedence bits should not be confused with PBR’s primary capability: routing packets based on configured policies. Some applications or traf ...
plug and play server load balancing and global server load
... of the MCU. The closest SLB manager supporting the anycast IP address will respond to the anycast ARP request with the individual IP addresses of all MCUs locally registered. The list will include an MCU health score for each registered MCU. The H.323 client can pick a preferred MCU from this list a ...
... of the MCU. The closest SLB manager supporting the anycast IP address will respond to the anycast ARP request with the individual IP addresses of all MCUs locally registered. The list will include an MCU health score for each registered MCU. The H.323 client can pick a preferred MCU from this list a ...
Defending Network-Based Services Against Denial of Service Attacks
... itself. In a directed end system attack, the objective is to thwart an end system or its subnet from sourcing or receiving multicast content. By overloading the state buffers at routers in its vicinity, a DoS attack can be executed against a multicast source (e.g. an Internet TV station) preventing ...
... itself. In a directed end system attack, the objective is to thwart an end system or its subnet from sourcing or receiving multicast content. By overloading the state buffers at routers in its vicinity, a DoS attack can be executed against a multicast source (e.g. an Internet TV station) preventing ...
Gossip-based Signaling Dissemination Extension for Next Steps In
... NSIS node, which may not be the next routing hop, and different transport and security services depending on the signaling application requirements. The actual signaling application logic is implemented in the higher layer of the NSIS stack, the NSIS Signaling Layer Protocol (NSLP). The NSIS protoco ...
... NSIS node, which may not be the next routing hop, and different transport and security services depending on the signaling application requirements. The actual signaling application logic is implemented in the higher layer of the NSIS stack, the NSIS Signaling Layer Protocol (NSLP). The NSIS protoco ...
cti - High Speed Network
... Established Channels will be increasingly augmented by Internet and Web-related technologies. Each of the technologies outlined below are available today. Several still require improvements in ...
... Established Channels will be increasingly augmented by Internet and Web-related technologies. Each of the technologies outlined below are available today. Several still require improvements in ...
CCNA5.0 Instructor PPT
... Purpose of Dynamic Routing Protocols (cont.) Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of message ...
... Purpose of Dynamic Routing Protocols (cont.) Main components of dynamic routing protocols include: Data structures - Routing protocols typically use tables or databases for its operations. This information is kept in RAM. Routing protocol messages - Routing protocols use various types of message ...
paper
... deliver them to two different neighbors in a single transmission whenever it knows that each of the two neighbors has overheard the packet destined to the other. Snooping not only extends the benefits of coding beyond duplex flows, but also enables us to code more than pairs of packets, producing a ...
... deliver them to two different neighbors in a single transmission whenever it knows that each of the two neighbors has overheard the packet destined to the other. Snooping not only extends the benefits of coding beyond duplex flows, but also enables us to code more than pairs of packets, producing a ...
Chapter 8 Lecture Presentation
... Protocol: specifies upper-layer protocol that is to receive IP data at the destination. Examples include TCP (protocol = 6), UDP (protocol = 17), and ICMP (protocol = 1). Header checksum: verifies the integrity of the IP header. Source IP address and destination IP address: contain the addresses of ...
... Protocol: specifies upper-layer protocol that is to receive IP data at the destination. Examples include TCP (protocol = 6), UDP (protocol = 17), and ICMP (protocol = 1). Header checksum: verifies the integrity of the IP header. Source IP address and destination IP address: contain the addresses of ...
Introduction to Computer Networks
... = speed of light ) A simple way to build an all optical-LAN is to use a passive star. To allow multiple transmissions at the same time, the spectrum is divided up into channels (wavelength bands) Each station is assigned two channels: one as a control channel to signal the station, and the other for ...
... = speed of light ) A simple way to build an all optical-LAN is to use a passive star. To allow multiple transmissions at the same time, the spectrum is divided up into channels (wavelength bands) Each station is assigned two channels: one as a control channel to signal the station, and the other for ...
TCP/IP Tutorial and Technical Overview
... 1.4 Future of the Internet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1.5 IBM and the Internet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1.5.1 The Network Computing Framework . . . . . . . . . . . . . . . . . . Chapter 2. Internetworking and Transport Layer Protoco ...
... 1.4 Future of the Internet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1.5 IBM and the Internet . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1.5.1 The Network Computing Framework . . . . . . . . . . . . . . . . . . Chapter 2. Internetworking and Transport Layer Protoco ...
PowerPoint
... – not widely deployed as LAN technology (no end-to-end connectivity) – no native ATM applications – IP over ATM: overhead – few applications supporting traffic profile definition – addressing scheme not compatible with IP – signalling only in few backbones -> lack of interoperability ...
... – not widely deployed as LAN technology (no end-to-end connectivity) – no native ATM applications – IP over ATM: overhead – few applications supporting traffic profile definition – addressing scheme not compatible with IP – signalling only in few backbones -> lack of interoperability ...
Metrics for Degree of Reordering in Packet Sequences
... without loss or duplication. Table 1 shows steps in computing displacements for RH. Initially, (see column 1) E, the expected sequence number is 1 and S, the arrived sequence number is also 1. The displacement value thus is 0 and hence frequency corresponding to displacement=0, F[0] becomes 1. For n ...
... without loss or duplication. Table 1 shows steps in computing displacements for RH. Initially, (see column 1) E, the expected sequence number is 1 and S, the arrived sequence number is also 1. The displacement value thus is 0 and hence frequency corresponding to displacement=0, F[0] becomes 1. For n ...
CS-TR-05-02 - Michigan Technological University
... characteristics such as administrative ease, ease of deployment and self-organization. Unstructured P2P networks however, pose significant challenges for anonymous communication protocols. An example of this kind of network is the Gnutella file sharing system, which is known to consume high bandwidt ...
... characteristics such as administrative ease, ease of deployment and self-organization. Unstructured P2P networks however, pose significant challenges for anonymous communication protocols. An example of this kind of network is the Gnutella file sharing system, which is known to consume high bandwidt ...
Internet protocol suite

The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP, because among many protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP) is the accepted and most widely used protocol in Internet. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. This functionality is organized into four abstraction layers which are used to sort all related protocols according to the scope of networking involved. From lowest to highest, the layers are the link layer, containing communication technologies for a single network segment (link); the internet layer, connecting hosts across independent networks, thus establishing internetworking; the transport layer handling host-to-host communication; and the application layer, which provides process-to-process application data exchange.The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF).