TCP and UDP
... limits messages to some finite size delivers messages after an arbitrarily long delay ...
... limits messages to some finite size delivers messages after an arbitrarily long delay ...
ECE544
... – Correction mode (optional): Correct 1 bit errors else discard when error detected • Reduced cell loss in face of single bit errors • Reduced error detection for multiple bit errors ...
... – Correction mode (optional): Correct 1 bit errors else discard when error detected • Reduced cell loss in face of single bit errors • Reduced error detection for multiple bit errors ...
FEATURES PIN ASSIGNMENT
... used to transmit potentiometer wiper settings and the stack select bit configuration to the 17-bit I/O shift register of the DS1267B. Figure 9(a) presents the 3-wire serial port protocol. As shown, the 3-wire port is inactive when the RST signal input is low. Communication with the DS1267B requires ...
... used to transmit potentiometer wiper settings and the stack select bit configuration to the 17-bit I/O shift register of the DS1267B. Figure 9(a) presents the 3-wire serial port protocol. As shown, the 3-wire port is inactive when the RST signal input is low. Communication with the DS1267B requires ...
PDF
... growing user demands for higher data rate and coverage. The fundamental challenge for significantly improving WLAN performance lies in the fact that wireless links suffer from high bit error rate (BER). Despite the advances of PHY layer capabilities [27] [2] [8] [15], achieving reliable communicatio ...
... growing user demands for higher data rate and coverage. The fundamental challenge for significantly improving WLAN performance lies in the fact that wireless links suffer from high bit error rate (BER). Despite the advances of PHY layer capabilities [27] [2] [8] [15], achieving reliable communicatio ...
15-744: Computer Networking
... • The Network Security Monitor developed at the University of California Davis was the first IDS to work directly with network data as opposed to log data • Essentially a packet sniffer feeding data to an analysis engine ...
... • The Network Security Monitor developed at the University of California Davis was the first IDS to work directly with network data as opposed to log data • Essentially a packet sniffer feeding data to an analysis engine ...
Word - ITU
... The structural features of the DSRC-ASL are as follows: The DSRC-ASL interfaces between the DSRC protocol stacks and the network applications or non-network applications. It provides supplemental communication functions for DSRC communications. The structure of the core of the DSRC-ASL is shown in F ...
... The structural features of the DSRC-ASL are as follows: The DSRC-ASL interfaces between the DSRC protocol stacks and the network applications or non-network applications. It provides supplemental communication functions for DSRC communications. The structure of the core of the DSRC-ASL is shown in F ...
Application Note 300 Watt Class E Amplifier Using MRF151A
... MOSFETS in the 1MHz-1GHz frequency range, has been a communication industry standard for more than 30 years. These devices are also used in many switch-mode amplifier applications and can yield much higher power and efficiency levels than specified in the traditional class AB designs. This applicati ...
... MOSFETS in the 1MHz-1GHz frequency range, has been a communication industry standard for more than 30 years. These devices are also used in many switch-mode amplifier applications and can yield much higher power and efficiency levels than specified in the traditional class AB designs. This applicati ...
74HC133 13-input NAND gate
... reasonably be expected to result in personal injury. Philips Semiconductors customers using or selling these products for use in such applications do so at their own risk and agree to fully indemnify Philips Semiconductors for any damages resulting from such application. Right to make changes — Phil ...
... reasonably be expected to result in personal injury. Philips Semiconductors customers using or selling these products for use in such applications do so at their own risk and agree to fully indemnify Philips Semiconductors for any damages resulting from such application. Right to make changes — Phil ...
Evolving Toward a Self-Managing Network Jennifer Rexford Princeton University
... • Idea #1: add abstraction on top – Compile high-level spec into box configuration – But, must grapple with inherent complexity ...
... • Idea #1: add abstraction on top – Compile high-level spec into box configuration – But, must grapple with inherent complexity ...
A1604_Bluetooth_Technology_Powerpoint
... Detect errors in the transmission Correct errors -> Ability to correct them ...
... Detect errors in the transmission Correct errors -> Ability to correct them ...
A Preview of Use of the Simple Network Management Protocol in
... the trap is received. If no acknowledgement is received, the Agent software can re-send the trap until it gets a response, greatly enhancing the surety of the alarm message being received. In all cases, a trap can be an alarm message to indicate some sort of error or problem detected in the Agent d ...
... the trap is received. If no acknowledgement is received, the Agent software can re-send the trap until it gets a response, greatly enhancing the surety of the alarm message being received. In all cases, a trap can be an alarm message to indicate some sort of error or problem detected in the Agent d ...
Controlling and Monitoring Audio Systems with Simple Network
... and the IP transport itself, we determined that a couple other protocols from the IP suite would be required. The Address Resolution Protocol (ARP) translates IP addresses to Ethernet Media Access Control (MAC) addresses. The Internet Control Message Protocol (ICMP) provides basic diagnostic service ...
... and the IP transport itself, we determined that a couple other protocols from the IP suite would be required. The Address Resolution Protocol (ARP) translates IP addresses to Ethernet Media Access Control (MAC) addresses. The Internet Control Message Protocol (ICMP) provides basic diagnostic service ...
wireless local area networks - BWN-Lab
... Note that some of the end systems are stand-alone devices such as a workstation or a server. In addition, hubs or other user modules (UM) (PORTAL before) that control a number of stations off a wired LAN may also be part of the wireless LAN configuration. IFA’2004 ...
... Note that some of the end systems are stand-alone devices such as a workstation or a server. In addition, hubs or other user modules (UM) (PORTAL before) that control a number of stations off a wired LAN may also be part of the wireless LAN configuration. IFA’2004 ...
DS1868 - Maxim Integrated
... Communication and control of the DS1868 is accomplished through a 3-wire serial port interface that drives an internal control logic unit. The 3-wire serial interface consists of the three input signals: RST , CLK, and DQ. The RST control signal is used to enable the 3-wire serial port operation of ...
... Communication and control of the DS1868 is accomplished through a 3-wire serial port interface that drives an internal control logic unit. The 3-wire serial interface consists of the three input signals: RST , CLK, and DQ. The RST control signal is used to enable the 3-wire serial port operation of ...
ATM - DSpace
... A second point in this same scenario is that the high speed of the links coupled with the small size of the cells means that, despite interleaving, cells from each line arrive at their respective destinations in an approximation of a continuous stream (much as a movie appears to your brain to ...
... A second point in this same scenario is that the high speed of the links coupled with the small size of the cells means that, despite interleaving, cells from each line arrive at their respective destinations in an approximation of a continuous stream (much as a movie appears to your brain to ...
OSI
... Structure of an ATM Network -based on the concept of two end point devices communicating by means of intermediate switches. - 2 types of interfaces in ATM networks : a) User-to-Network Interface (UNI) - connection is made up of end-point device and private or public ATM Switch b) Network-to-Network ...
... Structure of an ATM Network -based on the concept of two end point devices communicating by means of intermediate switches. - 2 types of interfaces in ATM networks : a) User-to-Network Interface (UNI) - connection is made up of end-point device and private or public ATM Switch b) Network-to-Network ...
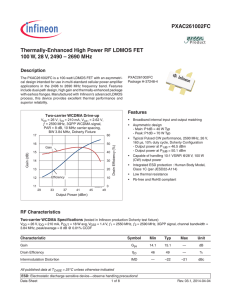
PXAC261002FC Thermally-Enhanced High Power RF LDMOS FET Description
... Revision History Revision ...
... Revision History Revision ...
CCNA1 Complete Lecture Set Mod 1 to 11
... hubs or switches. A hierarchical topology is similar to an extended star. However, instead of linking the hubs or switches together, the system is linked to a computer that controls the traffic on the topology. A mesh topology is implemented to provide as much protection as possible from interruptio ...
... hubs or switches. A hierarchical topology is similar to an extended star. However, instead of linking the hubs or switches together, the system is linked to a computer that controls the traffic on the topology. A mesh topology is implemented to provide as much protection as possible from interruptio ...