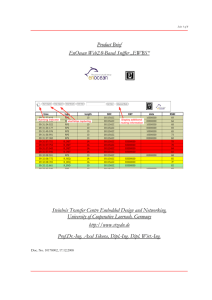
Semiconductors (opens in a new window)
... The Cl source was progressively pulsed off and on during growth, for differing periods. SIMS provided information about the growth rate of the whole structure, together with a profile of Cl in the doped layers. Note also the Cl pulse when the source shutter is first opened, shown by a small peak at ...
... The Cl source was progressively pulsed off and on during growth, for differing periods. SIMS provided information about the growth rate of the whole structure, together with a profile of Cl in the doped layers. Note also the Cl pulse when the source shutter is first opened, shown by a small peak at ...
Effective Anomaly Detection in Sensor Networks Data Streams
... Let X = [x1 , . . . , xL ] denote the network data matrix in which xi ∈ RN is a N -dimensional vector representing the status of N nodes at time instance i. A central monitor collects information from these distributed nodes to make a decision, and two cases can be considered: Case 1: It is difficul ...
... Let X = [x1 , . . . , xL ] denote the network data matrix in which xi ∈ RN is a N -dimensional vector representing the status of N nodes at time instance i. A central monitor collects information from these distributed nodes to make a decision, and two cases can be considered: Case 1: It is difficul ...
Week13_1 - FSU Computer Science Department
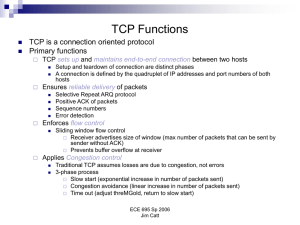
... • Informally: “too many sources sending too much data too fast for network to handle” • Different from flow control, caused by the network not by the receiver • How does the sender know whether there is congestion? Manifestations: – Lost packets (buffer overflow at routers) – Long delays (queuing in ...
... • Informally: “too many sources sending too much data too fast for network to handle” • Different from flow control, caused by the network not by the receiver • How does the sender know whether there is congestion? Manifestations: – Lost packets (buffer overflow at routers) – Long delays (queuing in ...
Hands-on Networking Fundamentals
... Layered protocol structure compatible with OSI model Channels in multiples of 64 Kbps, 384 Kbps, 1536 Kbps Has switched and non-switched connection services Broadband ISDN capabilities of 155 Mbps and higher ...
... Layered protocol structure compatible with OSI model Channels in multiples of 64 Kbps, 384 Kbps, 1536 Kbps Has switched and non-switched connection services Broadband ISDN capabilities of 155 Mbps and higher ...
Software Architecture to Integrate Sensors and
... packet. This is two bytes in length, allowing up to 65,536 separate data slots to be linked between the remote and base stations. The length field is next having two bytes. This indicates the length of the data field. Lastly there is the data field which can be up to 65,535 bytes in length. The data ...
... packet. This is two bytes in length, allowing up to 65,536 separate data slots to be linked between the remote and base stations. The length field is next having two bytes. This indicates the length of the data field. Lastly there is the data field which can be up to 65,535 bytes in length. The data ...
Data - Ingram Micro
... • Having the SSM mode in the data path must mean that there will be a performance impact on my server to storage data flow. – The SSM doesn’t not sit in the data path. It is able to tap of the data stream due to the MDS architecture which benefited from years of Cisco data networking experience. ...
... • Having the SSM mode in the data path must mean that there will be a performance impact on my server to storage data flow. – The SSM doesn’t not sit in the data path. It is able to tap of the data stream due to the MDS architecture which benefited from years of Cisco data networking experience. ...
CS514: Intermediate Course in Operating Systems
... Multicast addresses start with 1110 as the first 4 bits (Class D address) ...
... Multicast addresses start with 1110 as the first 4 bits (Class D address) ...
sink
... Structured approaches have several limitations for event-based application. -For dynamic scenarios, the overhead of construction and maintenance of the structure may outweigh the benefits of data aggregation. ...
... Structured approaches have several limitations for event-based application. -For dynamic scenarios, the overhead of construction and maintenance of the structure may outweigh the benefits of data aggregation. ...
module_30
... – Propagation velocity varies with frequency – Called also “Intersymbol Interference”. Due to delay distortions, some of the signal components of one bit position will spill over into other bit positions. ...
... – Propagation velocity varies with frequency – Called also “Intersymbol Interference”. Due to delay distortions, some of the signal components of one bit position will spill over into other bit positions. ...
Bridges - s3.amazonaws.com
... + Bridge tables are self learning - All traffic confined to spanning tree, even when alternative bandwidth is available - Bridges do not offer protection from broadcast ...
... + Bridge tables are self learning - All traffic confined to spanning tree, even when alternative bandwidth is available - Bridges do not offer protection from broadcast ...
Introduction to a Network Application Project
... to make signals that can carry information, we have to add several different sine waves (composite signals) ...
... to make signals that can carry information, we have to add several different sine waves (composite signals) ...
Chp. 4, Part II - comp
... – When sending datagrams to each other, the sender uses its IP address as the source address and the other’s IP address as the destination address. – Each performs IP-in-IP encapsulation/decapsulation and then IP routing. – A datagram may traverse several IP tunnels before arriving at the destinatio ...
... – When sending datagrams to each other, the sender uses its IP address as the source address and the other’s IP address as the destination address. – Each performs IP-in-IP encapsulation/decapsulation and then IP routing. – A datagram may traverse several IP tunnels before arriving at the destinatio ...
3rd Edition, Chapter 5
... today: ATM, MPLS … “invisible” at internetwork layer. Looks like a link layer technology to IP! ...
... today: ATM, MPLS … “invisible” at internetwork layer. Looks like a link layer technology to IP! ...
Physical Layer - NOISE | Network Operations and Internet
... highest signal rate that can be carried is 2B • So, C = 2B – But (stay tuned), each signal element can represent more than one bit (e.g., suppose more than two signal levels are used) – So … C = 2B lg M ...
... highest signal rate that can be carried is 2B • So, C = 2B – But (stay tuned), each signal element can represent more than one bit (e.g., suppose more than two signal levels are used) – So … C = 2B lg M ...
CT1303 LAN
... • Each centralized unit will send empty frames to the channel, which can be used by connected nodes to transmit data. • Each frame has 2 flags; one to identify whether the frame is empty and ready for used or has been reserved by another node. • The other flag identifies if there is a Reservation re ...
... • Each centralized unit will send empty frames to the channel, which can be used by connected nodes to transmit data. • Each frame has 2 flags; one to identify whether the frame is empty and ready for used or has been reserved by another node. • The other flag identifies if there is a Reservation re ...
Receiver-driven Layered Multicast
... Best possible service to all receivers Ability to cope with Congestion in the network All this should be done with just best effort service on the internet ...
... Best possible service to all receivers Ability to cope with Congestion in the network All this should be done with just best effort service on the internet ...
chapter5_1
... Deliver messages in the same order they are sent Deliver at most one copy of each message Support arbitrarily large messages Support synchronization Allow the receiver to flow control the sender Support multiple application processes on each host ...
... Deliver messages in the same order they are sent Deliver at most one copy of each message Support arbitrarily large messages Support synchronization Allow the receiver to flow control the sender Support multiple application processes on each host ...
ppt - NOISE
... highest signal rate that can be carried is 2B • So, C = 2B – But (stay tuned), each signal element can represent more than one bit (e.g., suppose more than two signal levels are used) – So … C = 2B lg M ...
... highest signal rate that can be carried is 2B • So, C = 2B – But (stay tuned), each signal element can represent more than one bit (e.g., suppose more than two signal levels are used) – So … C = 2B lg M ...
Real Time Data Techniques
... allows for connections to be resumed, eliminating most data gaps. The ability to resume data streams is primarily dependant on how much data, time-wise, the remote SeedLink has in its buffer. Special, out-of-band packets created by a seedlink server and recognized by libslink are used to communicate ...
... allows for connections to be resumed, eliminating most data gaps. The ability to resume data streams is primarily dependant on how much data, time-wise, the remote SeedLink has in its buffer. Special, out-of-band packets created by a seedlink server and recognized by libslink are used to communicate ...
SlinkRT
... allows for connections to be resumed, eliminating most data gaps. The ability to resume data streams is primarily dependant on how much data, time-wise, the remote SeedLink has in its buffer. Special, out-of-band packets created by a seedlink server and recognized by libslink are used to communicate ...
... allows for connections to be resumed, eliminating most data gaps. The ability to resume data streams is primarily dependant on how much data, time-wise, the remote SeedLink has in its buffer. Special, out-of-band packets created by a seedlink server and recognized by libslink are used to communicate ...