public_key_cryptography
... All secret key algorithms & hash algorithms do the same thing but public key algorithms look very different from each other. The thing that is common among all of them is that each participant has two keys, public and private, and most of them are based on modular arithmetic. Modular Arithmetic x mo ...
... All secret key algorithms & hash algorithms do the same thing but public key algorithms look very different from each other. The thing that is common among all of them is that each participant has two keys, public and private, and most of them are based on modular arithmetic. Modular Arithmetic x mo ...
Document
... Encrypt the message STOP (18 19 14 15) using the RSA cryptosystem with p = 43 and q = 59, so that n = 43‧59 = 2537, and with e = 13. (2537, 13) is a public key. Note that gcd(e, (p – 1)(q – 1) = gcd(13, 42.58) = 1. We encrypt each block using the mapping C = Me mod n, that is, C = M13 mod 2537. Comp ...
... Encrypt the message STOP (18 19 14 15) using the RSA cryptosystem with p = 43 and q = 59, so that n = 43‧59 = 2537, and with e = 13. (2537, 13) is a public key. Note that gcd(e, (p – 1)(q – 1) = gcd(13, 42.58) = 1. We encrypt each block using the mapping C = Me mod n, that is, C = M13 mod 2537. Comp ...
Full text
... for a natural algebraic and geometric setting for their analysis. In this way many known results are unified and simplified and new results are obtained. Some of the results extend to Fibonacci representations of higher order, but we do not present these because we have been unable to extend the the ...
... for a natural algebraic and geometric setting for their analysis. In this way many known results are unified and simplified and new results are obtained. Some of the results extend to Fibonacci representations of higher order, but we do not present these because we have been unable to extend the the ...
List of Shell Programs
... count the number of vowels in a line of text find the sum of odd digits and even digits from a find the smallest and largest number from a set check the given number and its reverse are generate Fibonacci Series find the sum of square of Individual Digits find the sum of cube of Individual digits of ...
... count the number of vowels in a line of text find the sum of odd digits and even digits from a find the smallest and largest number from a set check the given number and its reverse are generate Fibonacci Series find the sum of square of Individual Digits find the sum of cube of Individual digits of ...
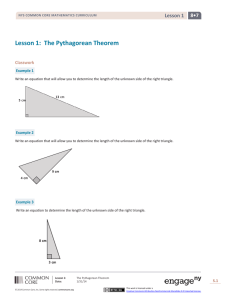
Key Introduction What is a Fraction
... When a solution to a problem, such as addition of fractions, turns out to be an improper fraction typically it should be converted to a mixed number. You can do this by following three steps. The first step is to divide the numerator of the improper fraction by the denominator. For example, when con ...
... When a solution to a problem, such as addition of fractions, turns out to be an improper fraction typically it should be converted to a mixed number. You can do this by following three steps. The first step is to divide the numerator of the improper fraction by the denominator. For example, when con ...
Cube and Cube Roots
... We can estimate the cube root of a given cube number through a step by step process. We get 375 and 857 as two groups of three digits each. First group, i.e., 375 will give you the one’s (or unit’s) digit of the required cube root. The number 375 ends with 5. We know that 5 comes at the unit’s place ...
... We can estimate the cube root of a given cube number through a step by step process. We get 375 and 857 as two groups of three digits each. First group, i.e., 375 will give you the one’s (or unit’s) digit of the required cube root. The number 375 ends with 5. We know that 5 comes at the unit’s place ...
Arithmetic

Arithmetic or arithmetics (from the Greek ἀριθμός arithmos, ""number"") is the oldest and most elementary branch of mathematics. It consists of the study of numbers, especially the properties of the traditional operations between them—addition, subtraction, multiplication and division. Arithmetic is an elementary part of number theory, and number theory is considered to be one of the top-level divisions of modern mathematics, along with algebra, geometry, and analysis. The terms arithmetic and higher arithmetic were used until the beginning of the 20th century as synonyms for number theory and are sometimes still used to refer to a wider part of number theory.