Cisco ME 6500 Series Ethernet Switch
... in identifying user’s MAC and IP address and port number, hence preventing attacks from malicious users. Malicious attacks can jeopardize the functionality of the network by compromising the switch CPU, MAC table, etc. Features such as Port Security and Per-VLAN MAC Limiting restrict the number of M ...
... in identifying user’s MAC and IP address and port number, hence preventing attacks from malicious users. Malicious attacks can jeopardize the functionality of the network by compromising the switch CPU, MAC table, etc. Features such as Port Security and Per-VLAN MAC Limiting restrict the number of M ...
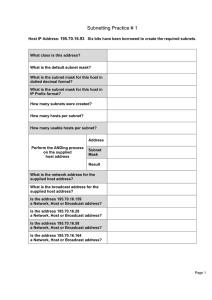
Subnetting Practice # 1
... You are the network administrator for Mangiare Food Supplies in Rome and are required to subnet the network according to the diagram. You have decided to use the network 172.31.0.0. It is the corporate policy that the IP address assigned to a default gateway is always the last host address in the su ...
... You are the network administrator for Mangiare Food Supplies in Rome and are required to subnet the network according to the diagram. You have decided to use the network 172.31.0.0. It is the corporate policy that the IP address assigned to a default gateway is always the last host address in the su ...
3rd Edition, Chapter 5
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
The Virtual Local Area Network (VLAN) Technology
... VLAN purely by port group does not allow multiple VLAN to include the same physical segment (or switch port). However, the primary limitation of defining VLAN by port is that the network manager must reconfigure VLAN membership when a user moves from one port to another. ...
... VLAN purely by port group does not allow multiple VLAN to include the same physical segment (or switch port). However, the primary limitation of defining VLAN by port is that the network manager must reconfigure VLAN membership when a user moves from one port to another. ...
Wireless Access Point Router with 4-Port Switch
... the Internet. The Router processes and regulates the data that travels between these two networks. ...
... the Internet. The Router processes and regulates the data that travels between these two networks. ...
Chp7
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
cisco 2-11
... • Purpose is to encrypt & authenticate routing information • This is an interface specific configuration • Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
... • Purpose is to encrypt & authenticate routing information • This is an interface specific configuration • Routers will only accept routing information from other routers that have been configured with the same password or authentication information ...
Security in Computer Networks
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
Lecture note 7
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
Chapter 7
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
... audio: < 150 msec good, < 400 msec OK • includes application-level (packetization) and network delays • higher delays noticeable, impair interactivity ...
7 10 Gigabit Ethernet Performance with Various
... With the increased availability and decrease in cost of Gigabit Ethernet using twisted pair cabling of suitable quality, system suppliers and integrators are offering Gigabit Ethernet and associated switches as the preferred interconnect between disk servers and PC compute farms as well as the most ...
... With the increased availability and decrease in cost of Gigabit Ethernet using twisted pair cabling of suitable quality, system suppliers and integrators are offering Gigabit Ethernet and associated switches as the preferred interconnect between disk servers and PC compute farms as well as the most ...
1 - IC Intracom
... The 10Base-T to 10Base-2 Media Converter was specifically designed to offer the network designer the tools for migration from UTP based Ethernet to Coaxial based Ethernet. Now migration or expansion of existing networks can be achieved with minimum cost and complexity. The converter is completely tr ...
... The 10Base-T to 10Base-2 Media Converter was specifically designed to offer the network designer the tools for migration from UTP based Ethernet to Coaxial based Ethernet. Now migration or expansion of existing networks can be achieved with minimum cost and complexity. The converter is completely tr ...
Internetworking - Northwestern University
... Conceptually, programmers can view the DNS database as a collection of millions of host entry structures: ...
... Conceptually, programmers can view the DNS database as a collection of millions of host entry structures: ...
Routing Concept
... Distance Vector Algorithm • Using hop count as a metric • Each router periodically sends a copy of its routing table to neighbors • send
...
... Distance Vector Algorithm • Using hop count as a metric • Each router periodically sends a copy of its routing table to neighbors • send
Remote Access VPN Setup (IPSec)
... not supported by the IPSec standard. Because broadcasts are not supported by the IPSec VPN standard we cannot guarantee that using hostnames instead of IP’s will work. A work around for this limitation of the IPSec standard would be to use a WINS server. ...
... not supported by the IPSec standard. Because broadcasts are not supported by the IPSec VPN standard we cannot guarantee that using hostnames instead of IP’s will work. A work around for this limitation of the IPSec standard would be to use a WINS server. ...
EVVBU Marketing Strategy Development Session
... 802.1x Open Benefits • 802.1x was designed to be inexpensive to implement on existing network hardware, utilizing existing network-access infrastructure (RADIUS, LDAP, Active Directory, etc.). • EAP-compatible RADIUS servers include, among others, Microsoft Windows 2000 Sever (IAS), Cisco ACS, Funk ...
... 802.1x Open Benefits • 802.1x was designed to be inexpensive to implement on existing network hardware, utilizing existing network-access infrastructure (RADIUS, LDAP, Active Directory, etc.). • EAP-compatible RADIUS servers include, among others, Microsoft Windows 2000 Sever (IAS), Cisco ACS, Funk ...
SG19LD ** NEW ** Network Setup Document
... Thank you for activating your free Dynamic DNS account for your Lorex DVR Combo. Once you have set up your Lorex device and configured your network, you will be able to view your video images from anywhere in the world using the URL shown at the end of this message. When you visit the Lorex web site ...
... Thank you for activating your free Dynamic DNS account for your Lorex DVR Combo. Once you have set up your Lorex device and configured your network, you will be able to view your video images from anywhere in the world using the URL shown at the end of this message. When you visit the Lorex web site ...
Development Kit For the PIC® MCU
... Open the PCW IDE. If any files are open, click File>Close All Click File>New>Source File and enter the filename EX3.C Type in the following program and Compile. ...
... Open the PCW IDE. If any files are open, click File>Close All Click File>New>Source File and enter the filename EX3.C Type in the following program and Compile. ...
Archer_C2600_UG_V1 - TP-Link
... 11. 7 Use WPS for wireless connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59 11. 7. 1. Set the router’s PIN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
... 11. 7 Use WPS for wireless connection . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 59 11. 7. 1. Set the router’s PIN . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ...
Simple Network Management Protocol (SNMP
... Network Analyst feature for managed switches SNMP Device Discovery MIB Import and Automatic Tag Generation Note: No dependency on the NetSNMP stack or on Microsoft SNMP tools for Windows. ...
... Network Analyst feature for managed switches SNMP Device Discovery MIB Import and Automatic Tag Generation Note: No dependency on the NetSNMP stack or on Microsoft SNMP tools for Windows. ...
EE579T-Class 2A
... • The physical interconnection of network elements does not necessarily reflect the logical network topology – Ethernet is logically a buss architecture – Ethernet, connected using hubs, uses a physical star interconnection – Ethernet, connected using coaxial cable, uses a physical buss interconnect ...
... • The physical interconnection of network elements does not necessarily reflect the logical network topology – Ethernet is logically a buss architecture – Ethernet, connected using hubs, uses a physical star interconnection – Ethernet, connected using coaxial cable, uses a physical buss interconnect ...
Network Management Integration Options
... can be viewed by clicking on the AP List tab. Similarly, the status of ACLs, VLANs or L3 features can be viewed by clicking on their respective tabs if there are any configured in the network. Figure 9 displays a list of connected APs from different vendors. ...
... can be viewed by clicking on the AP List tab. Similarly, the status of ACLs, VLANs or L3 features can be viewed by clicking on their respective tabs if there are any configured in the network. Figure 9 displays a list of connected APs from different vendors. ...
What`s DHCP? How DHCP works? - IT Resources
... For example, if you set a scope with a range from 10.0.0.100-10.0.0.200, you can easily provide only from this range IP addresses to your clients. You can also create more than one scope, but it's recommended to check that your scopes aren't duplicating one with each other's. At the scope creation p ...
... For example, if you set a scope with a range from 10.0.0.100-10.0.0.200, you can easily provide only from this range IP addresses to your clients. You can also create more than one scope, but it's recommended to check that your scopes aren't duplicating one with each other's. At the scope creation p ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.