Virtual Services Platform 4000
... Offering full multiservice capabilities without deployment of multiple protocols, the VSP 4000 offers a simplified, streamlined way to build and manage networks. For deployments in small offices where it is desirable to extend fabric technology across the wide area, the metro, or the campus edge or ...
... Offering full multiservice capabilities without deployment of multiple protocols, the VSP 4000 offers a simplified, streamlined way to build and manage networks. For deployments in small offices where it is desirable to extend fabric technology across the wide area, the metro, or the campus edge or ...
3rd Edition, Chapter 5 - Ursinus College Student, Faculty and Staff
... errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
... errors caused by signal attenuation, noise. receiver detects presence of errors: • signals sender for retransmission or drops frame ...
Admission Control in IP Multicast over Heterogeneous Access
... • ASN-GW Multicast router • SS ASN-GW connection – Identified by a 16bit number (CID) – Upstream unicast connections (exclusively) – Downstream multicast connections possible (mCID) but... • mCID are unidirectional in nature • not fitted for power-conservative systems • only efficient for large ...
... • ASN-GW Multicast router • SS ASN-GW connection – Identified by a 16bit number (CID) – Upstream unicast connections (exclusively) – Downstream multicast connections possible (mCID) but... • mCID are unidirectional in nature • not fitted for power-conservative systems • only efficient for large ...
GlobeSurfer® II 1.8 - 7.2 - 7.2 S
... GlobeSurfer ® II provides you with a quick installation and set-up that gets you easily and quickly connected to the Internet. You can use an Internet browser (e.g. Microsoft ® Internet Explorer 6.0 or Firefox ® 1.5) and most personal computers, including Windows ®, Macintosh ® and Linux. The ‘Quick ...
... GlobeSurfer ® II provides you with a quick installation and set-up that gets you easily and quickly connected to the Internet. You can use an Internet browser (e.g. Microsoft ® Internet Explorer 6.0 or Firefox ® 1.5) and most personal computers, including Windows ®, Macintosh ® and Linux. The ‘Quick ...
Lab – Configuring Dynamic and Static NAT (Instructor Version)
... Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many interfaces the router has. There is no way to effectively list all the combinations of configurations for each router class. This table includes identifiers for the possible combination ...
... Note: To find out how the router is configured, look at the interfaces to identify the type of router and how many interfaces the router has. There is no way to effectively list all the combinations of configurations for each router class. This table includes identifiers for the possible combination ...
GF2310821087
... media such as those utilized by infrared or radio frequency wireless communications adapters. Using such media, a mobile node can have neighbors which hear its broadcasts and yet do not detect each other (the hidden terminal problem). They [2] do not make any attempt to use specific characteristics ...
... media such as those utilized by infrared or radio frequency wireless communications adapters. Using such media, a mobile node can have neighbors which hear its broadcasts and yet do not detect each other (the hidden terminal problem). They [2] do not make any attempt to use specific characteristics ...
Deploying IPv6, now
... addresses Applications do not “reconnect” when a new IP address appears • TCP drops session when IP address changes • IPSEC hashes across IP addresses, changing address breaks the Security Association ...
... addresses Applications do not “reconnect” when a new IP address appears • TCP drops session when IP address changes • IPSEC hashes across IP addresses, changing address breaks the Security Association ...
Transmission-Control
... • If RTT of connections vary, connections with small RTT are able to higher proportion of bandwidth than connections with large RTT • If other non-TCP data is also present (such as multimedia using UDP), then TCP connections receive unfair treatment • Applications can use multiple TCP connections: e ...
... • If RTT of connections vary, connections with small RTT are able to higher proportion of bandwidth than connections with large RTT • If other non-TCP data is also present (such as multimedia using UDP), then TCP connections receive unfair treatment • Applications can use multiple TCP connections: e ...
paper - IJANA International Journal of Advanced Networking And
... another person’s data. 2.2 Active attack An active attack attempts to alter or destroy the data being exchanged in the network [1], [8]. 2.3 Layer based attack Network Layer Attack: The list of different types of attacks on network layer is discussed hereby: • Wormhole Attack: In wormhole attack, a ...
... another person’s data. 2.2 Active attack An active attack attempts to alter or destroy the data being exchanged in the network [1], [8]. 2.3 Layer based attack Network Layer Attack: The list of different types of attacks on network layer is discussed hereby: • Wormhole Attack: In wormhole attack, a ...
IPSO-6LoWPAN - University of California, Berkeley
... • Lack of broadcast capability impedes or, in some cases, renders some protocols inoperable (e.g. DHCP). Broadcast media can also allow efficient operation of multicast, a core mechanism of IPv6 • Link-layer error recovery often increases end-to-end performance. However, it should be lightweight and ...
... • Lack of broadcast capability impedes or, in some cases, renders some protocols inoperable (e.g. DHCP). Broadcast media can also allow efficient operation of multicast, a core mechanism of IPv6 • Link-layer error recovery often increases end-to-end performance. However, it should be lightweight and ...
Flowpoint and SmartSwitch Router DSL Devices
... prior notice. The reader should in all cases consult Aprisma to determine whether any such changes have been made. ...
... prior notice. The reader should in all cases consult Aprisma to determine whether any such changes have been made. ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... interoperability for microwave access) is based on IEEE 802.16 standards that provide wireless access to metropolitan area networks and there are several security problems The Wimax technology has great impact in wireless communication and has notched the top position in the wireless technology. But ...
... interoperability for microwave access) is based on IEEE 802.16 standards that provide wireless access to metropolitan area networks and there are several security problems The Wimax technology has great impact in wireless communication and has notched the top position in the wireless technology. But ...
static routing
... • Convergence is when all routers' routing tables are at a state of consistency. • The network has converged when all routers have complete and accurate information about the network. • Convergence time is the time it takes routers to share information, calculate best paths, and update their routing ...
... • Convergence is when all routers' routing tables are at a state of consistency. • The network has converged when all routers have complete and accurate information about the network. • Convergence time is the time it takes routers to share information, calculate best paths, and update their routing ...
Document
... • By using summarization, you reduce the routing tables on each router • To accomplish the summarization, you need to determine how many bits to unmask or unsubnet in order to make the networks appear as one big address block • The routing protocol must transmit the network prefix along with the net ...
... • By using summarization, you reduce the routing tables on each router • To accomplish the summarization, you need to determine how many bits to unmask or unsubnet in order to make the networks appear as one big address block • The routing protocol must transmit the network prefix along with the net ...
Tackling the Mobile Addressing Problem By: Kim Fullbrook
... Use existing RIR guidelines, request policies and procedures, with GSMA extras Only use Public addresses where mandatory for service or can demonstrate Private addressing is not feasible / practical Demonstrate conservative and efficient usage of requested address space, e.g. • Comparison of Public ...
... Use existing RIR guidelines, request policies and procedures, with GSMA extras Only use Public addresses where mandatory for service or can demonstrate Private addressing is not feasible / practical Demonstrate conservative and efficient usage of requested address space, e.g. • Comparison of Public ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... The information sensed by sensor devices are sent in form of data packets and for the reliable communication the transport layer protocol is embedded between application layer and network layer. The topology of WSNs can vary from a simple star network to an advanced multi-hop wireless mesh network. ...
... The information sensed by sensor devices are sent in form of data packets and for the reliable communication the transport layer protocol is embedded between application layer and network layer. The topology of WSNs can vary from a simple star network to an advanced multi-hop wireless mesh network. ...
User`s Manual
... When the power supply switches on, the power indicator light is on. If the power supply switches on but the power indicator light is off, then please check: 1, The power cable, the plug and power supply is normal or not. 2, If there’re no errors found through checking the above items and the breakdo ...
... When the power supply switches on, the power indicator light is on. If the power supply switches on but the power indicator light is off, then please check: 1, The power cable, the plug and power supply is normal or not. 2, If there’re no errors found through checking the above items and the breakdo ...
PDF
... upper-layer protocols of 802.11 link have unique signatures in their headers, which have distinct bit bias patterns. The bit bias refers to the fact that a bit takes the value of 1 or 0 with high frequency, such that it can be predicted by the receiver with high accuracy. There are numerous examples ...
... upper-layer protocols of 802.11 link have unique signatures in their headers, which have distinct bit bias patterns. The bit bias refers to the fact that a bit takes the value of 1 or 0 with high frequency, such that it can be predicted by the receiver with high accuracy. There are numerous examples ...
router rip
... 2. A Response message is sent back by RIP-enabled neighbors. If new route: Installs in routing table. If existing route: Replace if better hop count. Startup router then sends a triggered update out all RIP-enabled interfaces containing its own routing table so that RIP neighbors can be inform ...
... 2. A Response message is sent back by RIP-enabled neighbors. If new route: Installs in routing table. If existing route: Replace if better hop count. Startup router then sends a triggered update out all RIP-enabled interfaces containing its own routing table so that RIP neighbors can be inform ...
Cray XC Series Network
... Consider a fat tree network constructed from the 36-way routers typically used in InfiniBand networks. With 18 blades and a router per chassis there are 18 links up from each chassis. The chassis can be connected with 18 × 108-port switches to construct systems with up to 1,944 nodes. However, if th ...
... Consider a fat tree network constructed from the 36-way routers typically used in InfiniBand networks. With 18 blades and a router per chassis there are 18 links up from each chassis. The chassis can be connected with 18 × 108-port switches to construct systems with up to 1,944 nodes. However, if th ...
NETGEAR Wireless Router Setup Manual
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiat ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiat ...
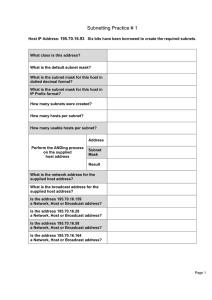
Subnetting Practice # 1
... You are the network administrator for Mangiare Food Supplies in Rome and are required to subnet the network according to the diagram. You have decided to use the network 172.31.0.0. It is the corporate policy that the IP address assigned to a default gateway is always the last host address in the su ...
... You are the network administrator for Mangiare Food Supplies in Rome and are required to subnet the network according to the diagram. You have decided to use the network 172.31.0.0. It is the corporate policy that the IP address assigned to a default gateway is always the last host address in the su ...
3rd Edition, Chapter 5
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
Cisco ME 6500 Series Ethernet Switch
... in identifying user’s MAC and IP address and port number, hence preventing attacks from malicious users. Malicious attacks can jeopardize the functionality of the network by compromising the switch CPU, MAC table, etc. Features such as Port Security and Per-VLAN MAC Limiting restrict the number of M ...
... in identifying user’s MAC and IP address and port number, hence preventing attacks from malicious users. Malicious attacks can jeopardize the functionality of the network by compromising the switch CPU, MAC table, etc. Features such as Port Security and Per-VLAN MAC Limiting restrict the number of M ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.