交大資工蔡文能計概
... – Routers typically do not forward these datagrams – Often ignored due to security concerns ...
... – Routers typically do not forward these datagrams – Often ignored due to security concerns ...
Networking the Internet - Part 1
... • Access local file servers with software and data • Access the Internet Rick Graziani [email protected] ...
... • Access local file servers with software and data • Access the Internet Rick Graziani [email protected] ...
About the Presentations
... • Work at the Application layer • Control the way applications inside the network access external networks by setting up proxy services • Minimize the effect of viruses, worms, Trojan horses, and other malware • Run special software that enable them to act as a proxy for a specific service request ...
... • Work at the Application layer • Control the way applications inside the network access external networks by setting up proxy services • Minimize the effect of viruses, worms, Trojan horses, and other malware • Run special software that enable them to act as a proxy for a specific service request ...
Document
... named after the date when the IEEE Computer Society “Local Network Standards Committee,” Project 802, held their first meeting, which was in February (2) of 1980(80) The 802 series of specifications define the physical media for each specification (802.3, 802.4, 802.5, and so on) ...
... named after the date when the IEEE Computer Society “Local Network Standards Committee,” Project 802, held their first meeting, which was in February (2) of 1980(80) The 802 series of specifications define the physical media for each specification (802.3, 802.4, 802.5, and so on) ...
socks for proxy - Linux Magazine
... ask the Socks proxy to open a port for the incoming data connection. The proxy sends two replies in response. The first contains the port and address at which the Socks server will listen for the incoming connection. The proxy does not send the second reply until the target server opens a connection ...
... ask the Socks proxy to open a port for the incoming data connection. The proxy sends two replies in response. The first contains the port and address at which the Socks server will listen for the incoming connection. The proxy does not send the second reply until the target server opens a connection ...
Intel® Rack Scale Architecture Platform Hardware Guide
... Intel disclaims all express and implied warranties, including without limitation, the implied warranties of merchantability, fitness for a particular purpose, and noninfringement, as well as any warranty arising from course of performance, course of dealing, or usage in trade. This document contains ...
... Intel disclaims all express and implied warranties, including without limitation, the implied warranties of merchantability, fitness for a particular purpose, and noninfringement, as well as any warranty arising from course of performance, course of dealing, or usage in trade. This document contains ...
CCNA2 Module 6
... Verify that the static route has been correctly entered. If the route is not correct, it will be necessary to go back into global configuration mode to remove the incorrect static route and enter the correct one. Enter the command show ip route. Verify that the route that was configured is in the ro ...
... Verify that the static route has been correctly entered. If the route is not correct, it will be necessary to go back into global configuration mode to remove the incorrect static route and enter the correct one. Enter the command show ip route. Verify that the route that was configured is in the ro ...
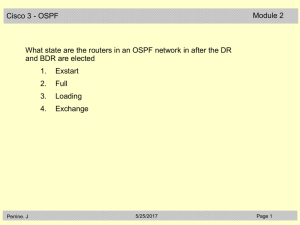
20088-2 CCNA3 3.1-02 Questions OSPF
... A network administrator has configured a default route on Router_A but it is not being shared with adjacent Router_B and the other routers in the OSPF area. Which command will save the administrator the time and trouble of configuring this default route on Router_B and all of the other routers in th ...
... A network administrator has configured a default route on Router_A but it is not being shared with adjacent Router_B and the other routers in the OSPF area. Which command will save the administrator the time and trouble of configuring this default route on Router_B and all of the other routers in th ...
IPv6
... Routing Protocols • RIPng • OSPFv3 • IS-IS Extensions for IPv6 • MP-BGP • EIGRP for IPv6 • Static Routing ...
... Routing Protocols • RIPng • OSPFv3 • IS-IS Extensions for IPv6 • MP-BGP • EIGRP for IPv6 • Static Routing ...
EE29 Shilpi Agrawal - RJIT paper
... networks. The main idea behind this method is to list out the set of malicious nodes locally at each node whenever they act as a source node. As mentioned in the Assumption our protocol uses the concept of Core Maintenance of the Allocation Table ie, whenever a new node joins the network, it sends a ...
... networks. The main idea behind this method is to list out the set of malicious nodes locally at each node whenever they act as a source node. As mentioned in the Assumption our protocol uses the concept of Core Maintenance of the Allocation Table ie, whenever a new node joins the network, it sends a ...
manet-intro
... protocol which provides one or more modes of operation, each mode specialized for efficient operation in a given mobile networking “context”, where a context is a predefined set of network characteristics. ...
... protocol which provides one or more modes of operation, each mode specialized for efficient operation in a given mobile networking “context”, where a context is a predefined set of network characteristics. ...
Note
... inet_aton() converts the Internet host address cp from the standard numbers-and-dots notation into binary data and stores it in the structure that inp points to. inet_aton() returns non-zero if the address is valid, zero if not. The inet_addr() function converts the Internet host address cp from num ...
... inet_aton() converts the Internet host address cp from the standard numbers-and-dots notation into binary data and stores it in the structure that inp points to. inet_aton() returns non-zero if the address is valid, zero if not. The inet_addr() function converts the Internet host address cp from num ...
P.DG A4001N User Manual
... Your Home Station ADSL requires the computer(s) and components in your network to be configured with at least the following: A computer with the Operating Systems that support TCP/IP networking protocols: Microsoft® Windows 2000, Windows XP 32bit, Vista 32bit, Windows 7 or Apple® MAC 10.x or Linux ...
... Your Home Station ADSL requires the computer(s) and components in your network to be configured with at least the following: A computer with the Operating Systems that support TCP/IP networking protocols: Microsoft® Windows 2000, Windows XP 32bit, Vista 32bit, Windows 7 or Apple® MAC 10.x or Linux ...
Multi-Protocol Label Switching (MPLS)
... • MPLS is currently in use in IP-only networks and is standardized by the IETF in RFC 3031. It is deployed to connect as few as two facilities to very large deployments. For example, in the retail sector, it is not uncommon to see deployments of 2000 to 5000 locations to communicate transaction data ...
... • MPLS is currently in use in IP-only networks and is standardized by the IETF in RFC 3031. It is deployed to connect as few as two facilities to very large deployments. For example, in the retail sector, it is not uncommon to see deployments of 2000 to 5000 locations to communicate transaction data ...
Why virtualize?
... virtual machines at near-native speed (requiring hardware virtualization extensions (VT-x) on x86 machines). QEMU can also be used purely for CPU emulation for userlevel processes, allowing applications compiled for one architecture to be run on another. ...
... virtual machines at near-native speed (requiring hardware virtualization extensions (VT-x) on x86 machines). QEMU can also be used purely for CPU emulation for userlevel processes, allowing applications compiled for one architecture to be run on another. ...
PPT
... – looks for errors, flow control, reliable data transmission, etc – extracts packet, passes to receiving node ...
... – looks for errors, flow control, reliable data transmission, etc – extracts packet, passes to receiving node ...
Turbo Codes and their Implementation
... Congestion Control assumes that packets are only lost due to overfull queues. ...
... Congestion Control assumes that packets are only lost due to overfull queues. ...
Notes
... compare transmitted, received signals difficult in wireless LANs: received signal strength ...
... compare transmitted, received signals difficult in wireless LANs: received signal strength ...
riku kaura-aho scalable iot traffic generation system
... was done before so a lot of time went on building, testing, and debugging the new environment. Thesis process started in the Autumn 2015 and professor Jarmo Harju from Tampere University of Technology started as the thesis supervisor. With long academic experience professor Harju has been a steady s ...
... was done before so a lot of time went on building, testing, and debugging the new environment. Thesis process started in the Autumn 2015 and professor Jarmo Harju from Tampere University of Technology started as the thesis supervisor. With long academic experience professor Harju has been a steady s ...
SLAC IPv6 deployment
... IPv6 Network configuration There is IOS code available that allows: – Cryptographic images • SSH client/server ...
... IPv6 Network configuration There is IOS code available that allows: – Cryptographic images • SSH client/server ...
Network Address Translation - Not a Security Panacea
... 1 . If a user on the inside initiates a connection to a web site that hosts a malicious application there is nothing on a NAT device that will block or filter the packets that return. 2 . There is nothing on the NAT device that will keep "friendly" or malicious applications on an internal host from ...
... 1 . If a user on the inside initiates a connection to a web site that hosts a malicious application there is nothing on a NAT device that will block or filter the packets that return. 2 . There is nothing on the NAT device that will keep "friendly" or malicious applications on an internal host from ...
Thesis for the Master of Science degree by
... data center. We evaluate the design trade offs of these WMN choices through the NS-3 simulations. The simulation results show that with this type of WMN (6 WiMAX Base Stations and 540 Wi-Fi Access Points), it is feasible to collect meter data from 150,000 smart meters within one second. The Smart Gr ...
... data center. We evaluate the design trade offs of these WMN choices through the NS-3 simulations. The simulation results show that with this type of WMN (6 WiMAX Base Stations and 540 Wi-Fi Access Points), it is feasible to collect meter data from 150,000 smart meters within one second. The Smart Gr ...
User Manual 4ipnet EAP767
... fast, secure and easy. They support business grade security, namely 802.1X, and Wi-Fi Protected Access (WPA and WPA2). By pushing a purposely built button, the 4ipWES (Press-n-Connect) feature makes it easy to bridge wireless links of multiple access points for forming a wider wireless network cover ...
... fast, secure and easy. They support business grade security, namely 802.1X, and Wi-Fi Protected Access (WPA and WPA2). By pushing a purposely built button, the 4ipWES (Press-n-Connect) feature makes it easy to bridge wireless links of multiple access points for forming a wider wireless network cover ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.