The Network Layer
... Fragmentation when the elementary data size is 1 byte. (a) Original packet, containing 10 data bytes. (b) Fragments after passing through a network with maximum packet size of 8 payload bytes plus header. (c) Fragments after passing through a size 5 gateway. ...
... Fragmentation when the elementary data size is 1 byte. (a) Original packet, containing 10 data bytes. (b) Fragments after passing through a network with maximum packet size of 8 payload bytes plus header. (c) Fragments after passing through a size 5 gateway. ...
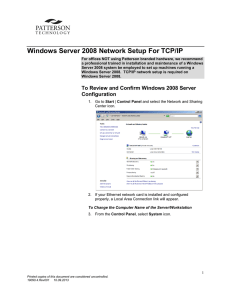
Windows Server 2008 Network Setup For TCP/IP
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
sheriff_1
... funded the Computer Science Network (CSNET). In 1982, the Internet protocol suite (TCP/IP) was introduced as the standard networking protocol on the ARPANET. In the early 1980s the NSF funded the establishment for national supercomputing centers at several universities, and provided interconnectivit ...
... funded the Computer Science Network (CSNET). In 1982, the Internet protocol suite (TCP/IP) was introduced as the standard networking protocol on the ARPANET. In the early 1980s the NSF funded the establishment for national supercomputing centers at several universities, and provided interconnectivit ...
Mention typical hardware components in a computer system (at least
... Why are three different addresses (“MAC address”, “IP address”, and “host name”) assigned to a host computer (to be exact, “to each NIC”) in the Internet? ...
... Why are three different addresses (“MAC address”, “IP address”, and “host name”) assigned to a host computer (to be exact, “to each NIC”) in the Internet? ...
1. The Central Processing Unit (CPU)
... 2. Optical media: these are storage media that hold content in digital form and that are written and read by a laser. These storage media group include all the various CD and DVD variations. 3. Semi-conducting media: These are often called flash memories. They use semiconductor clips to store data. ...
... 2. Optical media: these are storage media that hold content in digital form and that are written and read by a laser. These storage media group include all the various CD and DVD variations. 3. Semi-conducting media: These are often called flash memories. They use semiconductor clips to store data. ...
How the Internet works
... protocol stacks • layered architecture each layer is an abstraction that assumes the functionality of the layer underneath files unencrypted streams buffers packets frames bytes bits drivers, network card ...
... protocol stacks • layered architecture each layer is an abstraction that assumes the functionality of the layer underneath files unencrypted streams buffers packets frames bytes bits drivers, network card ...
Chapter 1/Tutorial
... infected hosts, such as stealing hard disk space or CPU time, accessing private information, corrupting data, displaying political or humorous messages on the user's screen ...
... infected hosts, such as stealing hard disk space or CPU time, accessing private information, corrupting data, displaying political or humorous messages on the user's screen ...
Assignment Group A1
... going on inside a network cable, just like a voltmeter is used by an electrician to examine what’s going on inside an electric cable (but at a higher level, of course).In the past, such tools were either very expensive, proprietary, or both. However, with the advent of Wireshark, all that has change ...
... going on inside a network cable, just like a voltmeter is used by an electrician to examine what’s going on inside an electric cable (but at a higher level, of course).In the past, such tools were either very expensive, proprietary, or both. However, with the advent of Wireshark, all that has change ...
Basic Networking
... Well, most devices that handle traffic don't need to know about the data within a packet to deliver to the next step in the chain. Only the device configured to receive that data will deencapsulate it (unwrap it) fully. ...
... Well, most devices that handle traffic don't need to know about the data within a packet to deliver to the next step in the chain. Only the device configured to receive that data will deencapsulate it (unwrap it) fully. ...
Document
... Middleware Resides between the client and server Gives the single system image Typically a major component in a NOS Provides: directory services, network security etc Contains proprietary elements where required ...
... Middleware Resides between the client and server Gives the single system image Typically a major component in a NOS Provides: directory services, network security etc Contains proprietary elements where required ...
Introduction to Computer Networking
... • Definition of: Ethernet The standard local area network (LAN) access method. A reference to "LAN," "LAN connection" or "network card" automatically implies Ethernet. • Most new computers come network ready with Ethernet built in. For machines without a network connection, Ethernet adapters can be ...
... • Definition of: Ethernet The standard local area network (LAN) access method. A reference to "LAN," "LAN connection" or "network card" automatically implies Ethernet. • Most new computers come network ready with Ethernet built in. For machines without a network connection, Ethernet adapters can be ...
PPT - University of Pittsburgh
... • Basic task of IP – moving packets as quickly as possible from one router to another • Yet, it doesn’t check whether packets are delivered successfully, thus need TCP • TCP (Transmission Control Protocol) – disassemble/reassemble packets, error checking, ACK packets ...
... • Basic task of IP – moving packets as quickly as possible from one router to another • Yet, it doesn’t check whether packets are delivered successfully, thus need TCP • TCP (Transmission Control Protocol) – disassemble/reassemble packets, error checking, ACK packets ...
$doc.title
... • MAC address (e.g., 00-‐15-‐C5-‐49-‐04-‐A9) – Numerical address used within a link – Unique, hard-‐coded in the adapter when it is built – Flat name space of 48 bits ...
... • MAC address (e.g., 00-‐15-‐C5-‐49-‐04-‐A9) – Numerical address used within a link – Unique, hard-‐coded in the adapter when it is built – Flat name space of 48 bits ...
PPT - UMD Department of Computer Science
... Packets can arrive late or out of order Intermediate routers will drop packets if the network is congested. ...
... Packets can arrive late or out of order Intermediate routers will drop packets if the network is congested. ...
2/6 Matt - Dr. John Durrett
... If a specific route to B exists, use this route (i.e., send the packet using the interface specified in the table) If a specific route to B’s network exists, use this route In the special case where A and B are in the same subnet (if the first a bits of A and B match), send the packet directly to B ...
... If a specific route to B exists, use this route (i.e., send the packet using the interface specified in the table) If a specific route to B’s network exists, use this route In the special case where A and B are in the same subnet (if the first a bits of A and B match), send the packet directly to B ...
IP packet filtering Packet filtering
... Stateful packet filtering • Allows for more complex policies based on current state of connections between two machines. – Let incoming UDP packets through only if they are responses to outgoing UDP packets you have seen. – Accept TCP packets with SYN set only as part of TCP connection initiation. ...
... Stateful packet filtering • Allows for more complex policies based on current state of connections between two machines. – Let incoming UDP packets through only if they are responses to outgoing UDP packets you have seen. – Accept TCP packets with SYN set only as part of TCP connection initiation. ...
1 It is desired to send a sequence of computer screen images over
... 10. Give two example computer applications for which connection-oriented service is appropriate. Now give two examples for which connectionless service is best. 11. Datagram subnets route each packet as a separate unit, independent of all others. Virtual-circuit subnets do not have to do this, since ...
... 10. Give two example computer applications for which connection-oriented service is appropriate. Now give two examples for which connectionless service is best. 11. Datagram subnets route each packet as a separate unit, independent of all others. Virtual-circuit subnets do not have to do this, since ...
Document
... Intelligent device to forward frame according to destination Media Access Control (MAC) address Forwarding: If the destination MAC address has a port different to the originate port, the frame will be sent. Filtering: If the destination MAC address is reachable with the same interface when it ...
... Intelligent device to forward frame according to destination Media Access Control (MAC) address Forwarding: If the destination MAC address has a port different to the originate port, the frame will be sent. Filtering: If the destination MAC address is reachable with the same interface when it ...
ITGS
... disk, and other machines are able to access them • With more than a few users, the lack of a server to aid in security and storage becomes a problem ...
... disk, and other machines are able to access them • With more than a few users, the lack of a server to aid in security and storage becomes a problem ...
The Infrastructure Technologies
... Breaks the message into packets. Ensures error free, end-toend delivery of the complete message. ...
... Breaks the message into packets. Ensures error free, end-toend delivery of the complete message. ...
Student Dormitory Network Usage Regulations
... The purpose to establish these regulations is to efficiently manage the dormitory network resources, which provides boarding students with TANet resources. The Student Dormitory Network offers switch ports and wireless connections for students to connect to the campus network. Students have to prepa ...
... The purpose to establish these regulations is to efficiently manage the dormitory network resources, which provides boarding students with TANet resources. The Student Dormitory Network offers switch ports and wireless connections for students to connect to the campus network. Students have to prepa ...
Chapter 15 Local Area Network Overview
... — Corporate internet operating within the organization — Uses Internet (TCP/IP and http)technology to deliver documents and resources ...
... — Corporate internet operating within the organization — Uses Internet (TCP/IP and http)technology to deliver documents and resources ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.