MESH NETWORK SIMULAION Pei Ping Belarusian National
... support a lot of school activities. An open area in class room provides a good environmental condition for mesh network. There are two AP – 4900M devices in classroom offering the wireless coverage indoor. The AP – 4000M devices are installed in front of the building A as well as the parking place. ...
... support a lot of school activities. An open area in class room provides a good environmental condition for mesh network. There are two AP – 4900M devices in classroom offering the wireless coverage indoor. The AP – 4000M devices are installed in front of the building A as well as the parking place. ...
Topologies for Power Efficient Wireless Sensor Networks
... consider the maximum available power at each node which falls in the direction the message should be routed and minimal directional value when picking which node route to take Instead of simply picking the node with the lowest directional value, the directional value is divided by the power avai ...
... consider the maximum available power at each node which falls in the direction the message should be routed and minimal directional value when picking which node route to take Instead of simply picking the node with the lowest directional value, the directional value is divided by the power avai ...
Voice Over IP (VoIP): Internet Telephony
... • Because the computer network is used, the reliability of the network will have an impact on the telephony service – In the analog telephone industry, reliability of 99.999 percent uptime is required – The above is known as five nines ...
... • Because the computer network is used, the reliability of the network will have an impact on the telephony service – In the analog telephone industry, reliability of 99.999 percent uptime is required – The above is known as five nines ...
Local Area Networks: Internetworking
... List the advantages of using frame relay for transmitting data. Describe a frame relay permanent virtual circuit and how it is created. Outline the basic features of frame relay’s committed information rate and how it is used to establish a level of service. List the differences between data over fr ...
... List the advantages of using frame relay for transmitting data. Describe a frame relay permanent virtual circuit and how it is created. Outline the basic features of frame relay’s committed information rate and how it is used to establish a level of service. List the differences between data over fr ...
IP / MPLS - IDG Communications
... • Network has full QoS feature support with Service Level Guarantees to support lower latency, packet loss and jitter • 100% Powered by Cisco Systems – Single vendor platform • Infrastructure is SOUL owned and operated, and independent of Telstra • In excess of 900 employees in offices throughout Au ...
... • Network has full QoS feature support with Service Level Guarantees to support lower latency, packet loss and jitter • 100% Powered by Cisco Systems – Single vendor platform • Infrastructure is SOUL owned and operated, and independent of Telstra • In excess of 900 employees in offices throughout Au ...
Cisco Discovery 1 Module 05 Quiz Picture Descriptions
... a PDA attached to a networked workstation 2. Which three statements are true about binary octets? (Choose three) if a bit is a zero (0), its column value is not counted. The value of each bit in an octet is twice that of the bit to its right. The rightmost bit in an octet has a value of 0 when it is ...
... a PDA attached to a networked workstation 2. Which three statements are true about binary octets? (Choose three) if a bit is a zero (0), its column value is not counted. The value of each bit in an octet is twice that of the bit to its right. The rightmost bit in an octet has a value of 0 when it is ...
Document
... Basic network topologies used to achieve connectivity within an Intranet Functions of network software, including managing communications sessions and avoiding data collision Characteristics of EDI technology and its application in a trading partner ...
... Basic network topologies used to achieve connectivity within an Intranet Functions of network software, including managing communications sessions and avoiding data collision Characteristics of EDI technology and its application in a trading partner ...
Firewall
... FORWARD chain. If accepted by FORWARD chain, packet is sent to the other interface If program running on computer wants to send packet out of the machine, packet must traverse through OUTPUT chain. If it is accepted by any of the rules, it is sent to whatever interface packet is intended for Each ru ...
... FORWARD chain. If accepted by FORWARD chain, packet is sent to the other interface If program running on computer wants to send packet out of the machine, packet must traverse through OUTPUT chain. If it is accepted by any of the rules, it is sent to whatever interface packet is intended for Each ru ...
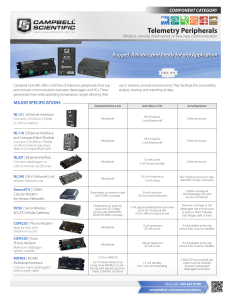
Telemetry Peripherals
... Campbell Scientific offers a full line of telemetry peripherals that support remote communications between dataloggers and PCs. These peripherals have wide operating temperature ranges allowing their ...
... Campbell Scientific offers a full line of telemetry peripherals that support remote communications between dataloggers and PCs. These peripherals have wide operating temperature ranges allowing their ...
Voice over IP
... provides a simple, but unreliable message service for transaction-oriented services. Each UDP header carries both a source port identifier and destination port identifier, allowing high-level protocols to target specific applications and services among hosts. ...
... provides a simple, but unreliable message service for transaction-oriented services. Each UDP header carries both a source port identifier and destination port identifier, allowing high-level protocols to target specific applications and services among hosts. ...
CCNA2 - MTEE Server
... ICMP messages are encapsulated into datagrams in the same way any other data is delivered using IP Since ICMP messages are transmitted in the same way as any other data, they are subject to the same delivery failures This creates a scenario where error reports could generate more error reports, caus ...
... ICMP messages are encapsulated into datagrams in the same way any other data is delivered using IP Since ICMP messages are transmitted in the same way as any other data, they are subject to the same delivery failures This creates a scenario where error reports could generate more error reports, caus ...
Network Control and Management in the 100x100 Architecture
... Individual networks can upgrade their control planes and gain benefits ...
... Individual networks can upgrade their control planes and gain benefits ...
Introducing a New Product
... Other tests demonstrated flawless call quality between two pairs separated by 2.1km and extending into Gulf St. Vincent in Adelaide, South Australia. Similar robust performance was experienced by the Serval Project's field testing of MPs and compatible equipment in the Australian Outback. Several ca ...
... Other tests demonstrated flawless call quality between two pairs separated by 2.1km and extending into Gulf St. Vincent in Adelaide, South Australia. Similar robust performance was experienced by the Serval Project's field testing of MPs and compatible equipment in the Australian Outback. Several ca ...
summary notes basic 6 (term 2)
... school network is the fact that all of the software can be loaded on one computer (the server). This saves time and energy when installing updates and tracking files. 8. Electronic Mail. A network that provides the hardware necessary to install an e mail system. E-mail’s help in personal and profess ...
... school network is the fact that all of the software can be loaded on one computer (the server). This saves time and energy when installing updates and tracking files. 8. Electronic Mail. A network that provides the hardware necessary to install an e mail system. E-mail’s help in personal and profess ...
our slides - Project Byzantium
... • A small group of minimally skilled individuals should be required to deploy the solution • Needs to support a larger community of users • Sufficient tools available to accomplish arbitrary tasks • Minimal collusion required • Not all devices on a network are running mesh routing software ...
... • A small group of minimally skilled individuals should be required to deploy the solution • Needs to support a larger community of users • Sufficient tools available to accomplish arbitrary tasks • Minimal collusion required • Not all devices on a network are running mesh routing software ...
PowerPoint Presentation - Securing a Wireless 802.11b Network
... access points, adapters, etc.) through a wired link – If you change a device setting through a wireless link, you could lose the connection when you apply the changes – Set up devices in this order: • Base station (Cable/DSL modem) • Access points ...
... access points, adapters, etc.) through a wired link – If you change a device setting through a wireless link, you could lose the connection when you apply the changes – Set up devices in this order: • Base station (Cable/DSL modem) • Access points ...
MSc – CD4040 – Internet and Web Research Topics
... TCP adds support to detect errors or lost data to trigger retransmission until the data is correctly and completely received. • Sockets is a name given to the package of subroutines that provide access to TCP/IP on most systems ...
... TCP adds support to detect errors or lost data to trigger retransmission until the data is correctly and completely received. • Sockets is a name given to the package of subroutines that provide access to TCP/IP on most systems ...
Student Workbook
... 12. Describe the components of a typical high-speed data access system for a service offering by a cable telecommunications company, and explain how a subscriber is part of a LAN. In your descriptions, be sure to include the physical form of the digital signal at the interfaces to each component. ...
... 12. Describe the components of a typical high-speed data access system for a service offering by a cable telecommunications company, and explain how a subscriber is part of a LAN. In your descriptions, be sure to include the physical form of the digital signal at the interfaces to each component. ...
HGiga PowerStation Product Presentation
... Provide secure remote access for mobile users. Windows has built-in support for PPTP/L2TP, no license and client software is required. ...
... Provide secure remote access for mobile users. Windows has built-in support for PPTP/L2TP, no license and client software is required. ...
Sisteme cu microprocesoare
... Other Application layer protocols DNS (Domain Name System) - is a service that allows addressing messages based on symbolic names, the protocol allows transformation of symbolic names for network addresses (IP addresses) - NFS (Network File System) - is a mapping service that allows remote file fol ...
... Other Application layer protocols DNS (Domain Name System) - is a service that allows addressing messages based on symbolic names, the protocol allows transformation of symbolic names for network addresses (IP addresses) - NFS (Network File System) - is a mapping service that allows remote file fol ...
VANET Simulation in Diffrent Indian City Scenario
... One emerging, new type of ad-hoc network is the Vehicular Ad-Hoc Network (VANET), in which vehicles constitute the mobile nodes in the network. Due to the prohibitive cost of deploying and implementing such a system in real world, most research in VANET relies on simulations for evaluation. This pap ...
... One emerging, new type of ad-hoc network is the Vehicular Ad-Hoc Network (VANET), in which vehicles constitute the mobile nodes in the network. Due to the prohibitive cost of deploying and implementing such a system in real world, most research in VANET relies on simulations for evaluation. This pap ...
Wake-on-LAN
Wake-on-LAN (WoL) is an Ethernet or Token ring computer networking standard that allows a computer to be turned on or awakened by a network message.The message is usually sent by a program executed on another computer on the same local area network. It is also possible to initiate the message from another network by using subnet directed broadcasts or a WOL gateway service. Equivalent terms include wake on WAN, remote wake-up, power on by LAN, power up by LAN, resume by LAN, resume on LAN and wake up on LAN. In case the computer being awakened is communicating via Wi-Fi, a supplementary standard called Wake on Wireless LAN (WoWLAN) must be employed.The WOL and WoWLAN standards are often supplemented by vendors to provide protocol-transparent on-demand services, for example in the Apple Bonjour wake-on-demand (Sleep Proxy) feature.