Chapter 11
... • Translates datagrams into format suitable for transport by physical network • IP layer can divide datagram into smaller units and transmit them individually – Attaches header information to each unit, including its sequence in the datagram ...
... • Translates datagrams into format suitable for transport by physical network • IP layer can divide datagram into smaller units and transmit them individually – Attaches header information to each unit, including its sequence in the datagram ...
Introduction - 多媒體網路實驗室The MNet Lab, NTHU-CS.
... • Building blocks of a network architecture • Each protocol object has two different interfaces – service interface: operations on this protocol – peer-to-peer interface: messages exchanged with peer ...
... • Building blocks of a network architecture • Each protocol object has two different interfaces – service interface: operations on this protocol – peer-to-peer interface: messages exchanged with peer ...
7- Link Budget Analysis and Design
... Path loss (Lpath) is the amount of signal attenuation due to the distance between the satellite and the ground station. This is the largest loss in the link. For example, the path loss for an S band signal from a geosyncronous satellite will be about 192 dB. Path loss varies with distance and freque ...
... Path loss (Lpath) is the amount of signal attenuation due to the distance between the satellite and the ground station. This is the largest loss in the link. For example, the path loss for an S band signal from a geosyncronous satellite will be about 192 dB. Path loss varies with distance and freque ...
Delay performance of CSMA in networks with bounded degree
... rates strictly less than s̃i , if the variance of the arrival process is also finite. From Theorem 2 this is an upper-bound on the mean delay for the real system. The bound on the mean delay only depends on the fugacities of link i and its neighbours and also the probabilities of choosing neighbours ...
... rates strictly less than s̃i , if the variance of the arrival process is also finite. From Theorem 2 this is an upper-bound on the mean delay for the real system. The bound on the mean delay only depends on the fugacities of link i and its neighbours and also the probabilities of choosing neighbours ...
Use of Artificial Neural Network in Data Mining For Weather
... can be used to detect attributes that do not contribute to the classification or prediction task. Including such attributes may otherwise slow down, and possibly mislead, the learning step. Data transformation and reduction: The data may be transformed by normalization, particularly when neural netw ...
... can be used to detect attributes that do not contribute to the classification or prediction task. Including such attributes may otherwise slow down, and possibly mislead, the learning step. Data transformation and reduction: The data may be transformed by normalization, particularly when neural netw ...
Long Term Evolution - Gabriele Falciasecca
... Other MIMO Techniques Transmit diversity Many different antennas transmit the same signal. At the receiver, the spatial diversity is exploited by using combining techniques. Closed Loop Rank-1 The same as the closed loop with RI=1 this assumption reduces the riTx overhead. Multi User MIMO, MU-MIM ...
... Other MIMO Techniques Transmit diversity Many different antennas transmit the same signal. At the receiver, the spatial diversity is exploited by using combining techniques. Closed Loop Rank-1 The same as the closed loop with RI=1 this assumption reduces the riTx overhead. Multi User MIMO, MU-MIM ...
address - Information Services and Technology
... • Machines are constantly moved – Keeping track of location of computers a chore – Simply give each machine a unique address – Broadcast all messages to all machines in the LAN ...
... • Machines are constantly moved – Keeping track of location of computers a chore – Simply give each machine a unique address – Broadcast all messages to all machines in the LAN ...
EC 4001 -Communication Engineering II - IESL e
... Characteristics of various forms of optical fibers(Single Mode, MultiMode, Step Index, Graded Index) Refractive index profile for each type of optical fiber ...
... Characteristics of various forms of optical fibers(Single Mode, MultiMode, Step Index, Graded Index) Refractive index profile for each type of optical fiber ...
lecture1424803314
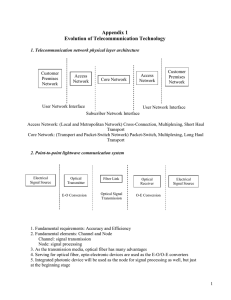
... interface). Using fiber-optics to end users is called Fiber To The Home or similar names. For customers with more demanding requirements(such as medium-to-large businesses, or other ISPs) can use higher-speed DSL (such as single-pair high-speed digital subscriber line ), Ethernet, metropolitan Ether ...
... interface). Using fiber-optics to end users is called Fiber To The Home or similar names. For customers with more demanding requirements(such as medium-to-large businesses, or other ISPs) can use higher-speed DSL (such as single-pair high-speed digital subscriber line ), Ethernet, metropolitan Ether ...
6 Lecture 6 Intro to Switching & Circuit Switching
... setting up a dedicated end to end connection. This path is maintained till the end of communication. • Link is released after communication is over • Circuit switching takes place at physical layer • Data transfer may use FDM or TDM ...
... setting up a dedicated end to end connection. This path is maintained till the end of communication. • Link is released after communication is over • Circuit switching takes place at physical layer • Data transfer may use FDM or TDM ...
Multiple Processor Systems
... – Link – physically interfacing with communication medium to move a packet over a link; Ethernet, WiFi 802.11 – Network – moving packets over multiple links, from src to destination; IP (Internet Protocol) – Transport – provides a msg service to apps; apps don’t need to care that communication is ...
... – Link – physically interfacing with communication medium to move a packet over a link; Ethernet, WiFi 802.11 – Network – moving packets over multiple links, from src to destination; IP (Internet Protocol) – Transport – provides a msg service to apps; apps don’t need to care that communication is ...
Part I: Introduction
... “SPEED aims at providing a uniform packet delivery speed across the sensor network, so that the end-to-end delay of a packet is proportional to the distance between the source and the destination. With this service, real-time applications can estimate end-to-end delay before making ...
... “SPEED aims at providing a uniform packet delivery speed across the sensor network, so that the end-to-end delay of a packet is proportional to the distance between the source and the destination. With this service, real-time applications can estimate end-to-end delay before making ...
PPT - Yuan Cheng
... Using cipher requires knowledge of environment, and threats in the environment, in which cipher will be used ...
... Using cipher requires knowledge of environment, and threats in the environment, in which cipher will be used ...
UNIT 19 (CAN)
... device, the host CPU defines which messages are to be sent and which are to be received. Only if the CAN controller receives a message whose identifier matches with one of the identifiers of the programmed (receive-) message objects the message is stored and the host CPU is informed by interrupt. An ...
... device, the host CPU defines which messages are to be sent and which are to be received. Only if the CAN controller receives a message whose identifier matches with one of the identifiers of the programmed (receive-) message objects the message is stored and the host CPU is informed by interrupt. An ...
TCP/IP Internetworking (Part 2)
... In this case network 192.168.x.x and network 60.x.x.x). An “x” indicates anything Corporate network 192.168.x.x ...
... In this case network 192.168.x.x and network 60.x.x.x). An “x” indicates anything Corporate network 192.168.x.x ...
Transport
... unused buffer space by including rwnd value in segment header sender: limits # of unACKed bytes to rwnd ...
... unused buffer space by including rwnd value in segment header sender: limits # of unACKed bytes to rwnd ...
3.01a_Network Technology - fitslm
... • A LASER transmitter encodes frequency signals into pulses of light: ones and zeros are sent through the cable. • The receiving end of the transmission translates the light signals back into data which can be read by a computer. ...
... • A LASER transmitter encodes frequency signals into pulses of light: ones and zeros are sent through the cable. • The receiving end of the transmission translates the light signals back into data which can be read by a computer. ...
Bluetooth Comparison
... SDP: Provides a means for applications to discover which services are available and to determine the characteristics of those available services Provides connection-oriented and connectionless data services to upper layer protocols with protocol multiplexing capability, segmentation, and reassembly ...
... SDP: Provides a means for applications to discover which services are available and to determine the characteristics of those available services Provides connection-oriented and connectionless data services to upper layer protocols with protocol multiplexing capability, segmentation, and reassembly ...
P7780
... It is then split into 2, 32 bit sub-blocks, Li and Ri which are then passed into what is known as a round (see figure 2.3), of which there are 16 (the subscript i in Li and Ri indicates the current round). Each of the rounds is identical and the effects of increasing their number are twofold - the a ...
... It is then split into 2, 32 bit sub-blocks, Li and Ri which are then passed into what is known as a round (see figure 2.3), of which there are 16 (the subscript i in Li and Ri indicates the current round). Each of the rounds is identical and the effects of increasing their number are twofold - the a ...
switch
... Ethernet MAC Protocol • Medium Access Control (MAC) layer protocol is identical for all Ethernets: – Ethernet Frame format – Carrier Sense Multiple Access with Collision Detection (CSMA/CD) used to determine which workstation can send at any given time. ...
... Ethernet MAC Protocol • Medium Access Control (MAC) layer protocol is identical for all Ethernets: – Ethernet Frame format – Carrier Sense Multiple Access with Collision Detection (CSMA/CD) used to determine which workstation can send at any given time. ...
ppt - Suraj @ LUMS
... IEEE sets G/L = 0 when giving out the blocks of addresses Addresses with G/L = 1 can be used without paying IEEE but the network administrator is responsible to assign addresses such that there is no collision This leaves with 222 unique OUIs ...
... IEEE sets G/L = 0 when giving out the blocks of addresses Addresses with G/L = 1 can be used without paying IEEE but the network administrator is responsible to assign addresses such that there is no collision This leaves with 222 unique OUIs ...
Document
... For current node, consider all its unvisited neighbours and calculate their distance (from the initial node). For example, if current node (A) has distance of 6, and an edge connecting it with another node (B) is 2, the distance to B through A will be 6+2=8. If this distance is less than the previou ...
... For current node, consider all its unvisited neighbours and calculate their distance (from the initial node). For example, if current node (A) has distance of 6, and an edge connecting it with another node (B) is 2, the distance to B through A will be 6+2=8. If this distance is less than the previou ...