Managed Bandwidth Vipersat Management System (VMS)
... Switching protocol enables external messaging to switch carriers to multi-point destinations Operates over multiple transponders and satellites Scalable from small to large networks Auto detection of new nodes Detailed event logs can be filtered and exported SNMP traps can be forwarded to hierarchal ...
... Switching protocol enables external messaging to switch carriers to multi-point destinations Operates over multiple transponders and satellites Scalable from small to large networks Auto detection of new nodes Detailed event logs can be filtered and exported SNMP traps can be forwarded to hierarchal ...
tetra tactical digital mobile radio system tetratac – stt115general
... needs. The SMS package, in its full extension, includes the AIE and ETE customized algorithms, the relevant downloading packages to properly set-up the switches (SCN), the base stations (RBS) and the terminals, the overall key management system (generation and distribution facilities). It must be no ...
... needs. The SMS package, in its full extension, includes the AIE and ETE customized algorithms, the relevant downloading packages to properly set-up the switches (SCN), the base stations (RBS) and the terminals, the overall key management system (generation and distribution facilities). It must be no ...
DC GW - IETF
... Interoperates with existing WAN VPN technology Deployment tested, provides a full networking toolset Scalable core routing – only one BGP-MP routing instance is required compared with one per customer/tenant in the Virtual Routing case • Service Auto-discovery - automatic discovery and route distrib ...
... Interoperates with existing WAN VPN technology Deployment tested, provides a full networking toolset Scalable core routing – only one BGP-MP routing instance is required compared with one per customer/tenant in the Virtual Routing case • Service Auto-discovery - automatic discovery and route distrib ...
Chapter 11 ATM - Darbhanga College of Engineering
... —Frame relay switches variable length frames within frame relay cloud from source to destination —ATM switches fixed-length cells (48 byte information field, 5 byte header) • Based on packet switching (connection-oriented) —Cell sequence integrity preserved via virtual channel —VCC – virtual channel ...
... —Frame relay switches variable length frames within frame relay cloud from source to destination —ATM switches fixed-length cells (48 byte information field, 5 byte header) • Based on packet switching (connection-oriented) —Cell sequence integrity preserved via virtual channel —VCC – virtual channel ...
U.S. Optical Network Status
... Standardized GMPLS protocols for dynamic provisioning intra-domain connections Develop inter-domain protocols to distribute ...
... Standardized GMPLS protocols for dynamic provisioning intra-domain connections Develop inter-domain protocols to distribute ...
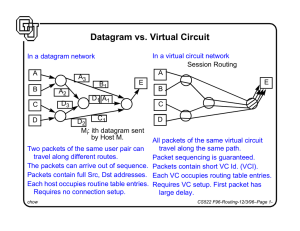
Datagram vs. Virtual Circuit
... Find the shortest paths form a given source node to all other nodes by developing paths in order of increasing path length. Let the set of nodes in a network be N. 1. start with a source node S in node set M. Let the nodes not in M be M’. 2. Let L with the set of links connecting M and M’. l Among t ...
... Find the shortest paths form a given source node to all other nodes by developing paths in order of increasing path length. Let the set of nodes in a network be N. 1. start with a source node S in node set M. Let the nodes not in M be M’. 2. Let L with the set of links connecting M and M’. l Among t ...
replex - Princeton CS - Princeton University
... 1. HyperDex recovers slowest because 2-3x more data 2. Replex-2 recovers fastest because least data, parallel recovery ...
... 1. HyperDex recovers slowest because 2-3x more data 2. Replex-2 recovers fastest because least data, parallel recovery ...
IDS - Ecs.csus.edu
... Detecting Backdoors with NIDS Look for telltale signs of sniffer and rootkit activity Entrap sniffers into revealing themselves • Use bogus IP addresses and username/password pairs; open bogus TCP connections, then measure ping times – Sniffer may try a reverse DNS query on the planted address; r ...
... Detecting Backdoors with NIDS Look for telltale signs of sniffer and rootkit activity Entrap sniffers into revealing themselves • Use bogus IP addresses and username/password pairs; open bogus TCP connections, then measure ping times – Sniffer may try a reverse DNS query on the planted address; r ...
User Datagram Protocol (UDP) Transmission Control Protocol (TCP
... ! Source port and checksum are optional " Checksum mandatory with IPv6 ! Length: header and data in bytes ! Ports provide application multiplexing within a host (single IP) ...
... ! Source port and checksum are optional " Checksum mandatory with IPv6 ! Length: header and data in bytes ! Ports provide application multiplexing within a host (single IP) ...
The fundamentals of TCP/IP networking
... The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks. TCP/IP is often referred to as a protocol stack because it consists of a series of protocols t ...
... The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks. TCP/IP is often referred to as a protocol stack because it consists of a series of protocols t ...
CCNA 1 v5.1 Practice Final Exam Answers 2016 100% PDF
... 8. Which message delivery option is used when all devices need to receive the same message simultaneously? o duplex o unicast o multicast o broadcast 9. Which two protocols function at the internet layer? (Choose two.) o POP o BOOTP o ICMP o IP o PPP 10. What PDU is associated with the transport lay ...
... 8. Which message delivery option is used when all devices need to receive the same message simultaneously? o duplex o unicast o multicast o broadcast 9. Which two protocols function at the internet layer? (Choose two.) o POP o BOOTP o ICMP o IP o PPP 10. What PDU is associated with the transport lay ...
Presentation
... Challenges for an operator Distribution of accurate time synchronization creates new challenges for an operator Operation of the network Handling of asymmetries (at set up and during operation) Planning of proper Redundancy (e.g. Time sync Holdover is only available for limited periods (minutes ins ...
... Challenges for an operator Distribution of accurate time synchronization creates new challenges for an operator Operation of the network Handling of asymmetries (at set up and during operation) Planning of proper Redundancy (e.g. Time sync Holdover is only available for limited periods (minutes ins ...
Viscoplastic Models for Polymeric Composite - MY Hussaini
... dependent on vectors of temperature, strain level and time data. A generalized neural network and one specific to this model are shown in Figure 11. A neural network consists of nodes connected by links. Each node is a processing element which takes weighted inputs from other nodes, sums them, and t ...
... dependent on vectors of temperature, strain level and time data. A generalized neural network and one specific to this model are shown in Figure 11. A neural network consists of nodes connected by links. Each node is a processing element which takes weighted inputs from other nodes, sums them, and t ...
Chapter 1 Lecture Slides - Classes
... sharing call setup required circuit-like (guaranteed) ...
... sharing call setup required circuit-like (guaranteed) ...
Experiment: Step by Step
... theanserver is stopped, it sends stop with • While LMM is hanging the port used for communication the server remains unreleased, which means that the new commands to all LMMs experiment cannot be started until LMMs are stopped and all Uponnecessary receiving the stop have signal, LMM: clean-up pro ...
... theanserver is stopped, it sends stop with • While LMM is hanging the port used for communication the server remains unreleased, which means that the new commands to all LMMs experiment cannot be started until LMMs are stopped and all Uponnecessary receiving the stop have signal, LMM: clean-up pro ...
IDS
... • At the early stage of the worm, only limited worm samples. • Host based sensors can only cover limited IP space, which has scalability issues. Thus they might not be able to detect the worm in its early stage. ...
... • At the early stage of the worm, only limited worm samples. • Host based sensors can only cover limited IP space, which has scalability issues. Thus they might not be able to detect the worm in its early stage. ...
SIS-DTN_Green Book v0.6-v0.7 changes
... continuing to extend this model so that agencies can share resources such as ground stations for crosssupport. This sharing is implemented by tunneling the space data link from the ground station across the terrestrial communications infrastructure to the control center, so that the ground station a ...
... continuing to extend this model so that agencies can share resources such as ground stations for crosssupport. This sharing is implemented by tunneling the space data link from the ground station across the terrestrial communications infrastructure to the control center, so that the ground station a ...
Chapter 1 - Introduction
... – An entire industry emerged that develops networking technologies, products, and services – The importance of computer networks has produced a demand in all industries for people with more networking expertise – Companies need workers to plan, acquire, install, operate, and manage the hardware and ...
... – An entire industry emerged that develops networking technologies, products, and services – The importance of computer networks has produced a demand in all industries for people with more networking expertise – Companies need workers to plan, acquire, install, operate, and manage the hardware and ...
Chapter 1 - Introduction
... – An entire industry emerged that develops networking technologies, products, and services – The importance of computer networks has produced a demand in all industries for people with more networking expertise – Companies need workers to plan, acquire, install, operate, and manage the hardware and ...
... – An entire industry emerged that develops networking technologies, products, and services – The importance of computer networks has produced a demand in all industries for people with more networking expertise – Companies need workers to plan, acquire, install, operate, and manage the hardware and ...
ConneXium - Schneider Electric
... Ethernet devices to a single network segment ● Unmanaged switch – Capabilities ● Plug and Play device operation, no configuration required ● Store and Forward – stores and checks all received data before forwarding ● Multi-Address Capability - learn source addresses on a per-port basis ● Tagging - d ...
... Ethernet devices to a single network segment ● Unmanaged switch – Capabilities ● Plug and Play device operation, no configuration required ● Store and Forward – stores and checks all received data before forwarding ● Multi-Address Capability - learn source addresses on a per-port basis ● Tagging - d ...
In the name of God, the most compassionate, the most merciful NFV
... and high frequencies, both at indoors and as outdoor hotspots, using mMIMO To save energy, small cells can dynamically be switched on and off, inspired by the highly variable traffic loads served by small cells Separation of coverage & capacity will enable independent mobility of C & U planes which ...
... and high frequencies, both at indoors and as outdoor hotspots, using mMIMO To save energy, small cells can dynamically be switched on and off, inspired by the highly variable traffic loads served by small cells Separation of coverage & capacity will enable independent mobility of C & U planes which ...