1 Which of the following devices can we use to segment our lan
... (C) Routers have direct knowledge of all links in the network and how they are connected. (D) After the initial LSA flooding, they generally require less bandwidth to communicate changes in a topology. (E) Link-state protocols require less router processor power than distance vector protocols. 9 Whe ...
... (C) Routers have direct knowledge of all links in the network and how they are connected. (D) After the initial LSA flooding, they generally require less bandwidth to communicate changes in a topology. (E) Link-state protocols require less router processor power than distance vector protocols. 9 Whe ...
2006 CeBIT Catalogue
... üProvides 3 Parallel ports to connect to the printers üShare your Parallel printer with all PCs through network üSupports TCP/IP, IPX/SPX and AppleTalk network protocols üSupports LPR, IPP, SMB/TCP, Raw protocols üSupportsD HCP Sever and Client Raw protocols üWeb-Based management, Windows configurat ...
... üProvides 3 Parallel ports to connect to the printers üShare your Parallel printer with all PCs through network üSupports TCP/IP, IPX/SPX and AppleTalk network protocols üSupports LPR, IPP, SMB/TCP, Raw protocols üSupportsD HCP Sever and Client Raw protocols üWeb-Based management, Windows configurat ...
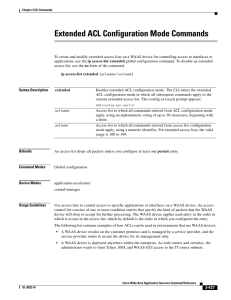
Extended ACL Configuration Mode Commands
... To add a line to an extended access-list that specifies the type of packets that you want the WAAS device to drop, use the deny command. To add a condition to the extended ACL, note that the options depend on the chosen protocol. For IP, use the following syntax to add a condition: [insert line-num] ...
... To add a line to an extended access-list that specifies the type of packets that you want the WAAS device to drop, use the deny command. To add a condition to the extended ACL, note that the options depend on the chosen protocol. For IP, use the following syntax to add a condition: [insert line-num] ...
Overview of Switches
... Switches are widely being used today by most of the business networks to connect multiple devices such as computers, printers and servers that are present within a particular boundary like a campus or building. The switch is responsible for enabling communication between the networking devices on a ...
... Switches are widely being used today by most of the business networks to connect multiple devices such as computers, printers and servers that are present within a particular boundary like a campus or building. The switch is responsible for enabling communication between the networking devices on a ...
3rd Edition: Chapter 4
... CIDR is also known as “supernetting” because subnetting and CIDR are basically the same idea. ...
... CIDR is also known as “supernetting” because subnetting and CIDR are basically the same idea. ...
RapidIO-based Space System Architectures for
... recognition [2]. SAR contains some high-level similarities to GMTI, such as the ability to break processing into stages and the repartitioning of data between different stages [3-4]. However, there are also distinct and important differences, which provide an interesting comparison of system perform ...
... recognition [2]. SAR contains some high-level similarities to GMTI, such as the ability to break processing into stages and the repartitioning of data between different stages [3-4]. However, there are also distinct and important differences, which provide an interesting comparison of system perform ...
CA Spool - Arcserve
... printer queues and documents. An SAF compliant security interface provides the ability to control which documents are printed where, and which users have the ability to view and print specific reports. An additional feature allows printers to be grouped so that if one printer is in use or unavailabl ...
... printer queues and documents. An SAF compliant security interface provides the ability to control which documents are printed where, and which users have the ability to view and print specific reports. An additional feature allows printers to be grouped so that if one printer is in use or unavailabl ...
Internet Secure Protocols
... almost (but not quite) as safe as a node disconnected from the net. Internal routers should not advertise paths to such nodes to the outside. Filter routes learned from the outside: ...
... almost (but not quite) as safe as a node disconnected from the net. Internal routers should not advertise paths to such nodes to the outside. Filter routes learned from the outside: ...
COEN 351
... almost (but not quite) as safe as a node disconnected from the net. Internal routers should not advertise paths to such nodes to the outside. Filter routes learned from the outside: ...
... almost (but not quite) as safe as a node disconnected from the net. Internal routers should not advertise paths to such nodes to the outside. Filter routes learned from the outside: ...
S5720-SI Switch Data Sheet
... tunnels (including manual tunnels, 6to4 tunnels, and ISATAP tunnels), and Layer 3 line-speed forwarding. The S5700 can be deployed on IPv4 networks, IPv6 networks, or networks that run both IPv4 and IPv6. This makes networking flexible and enables easy migration from IPv4 to IPv6. ...
... tunnels (including manual tunnels, 6to4 tunnels, and ISATAP tunnels), and Layer 3 line-speed forwarding. The S5700 can be deployed on IPv4 networks, IPv6 networks, or networks that run both IPv4 and IPv6. This makes networking flexible and enables easy migration from IPv4 to IPv6. ...
N51 , N52 EFM SHDSL.bis Modem User`s Manual V1.2
... should be performed in advance. ☞ Check the user's computer hardware. √Make sure that the Ethernet card (Network Adapter) is installed. √Make sure that the Ethernet card supports the TCP/IP protocol. ☞ Confirm if TCP/IP has already been installed in the computer running on Windows. The confirmation ...
... should be performed in advance. ☞ Check the user's computer hardware. √Make sure that the Ethernet card (Network Adapter) is installed. √Make sure that the Ethernet card supports the TCP/IP protocol. ☞ Confirm if TCP/IP has already been installed in the computer running on Windows. The confirmation ...
3rd Edition: Chapter 4 - University of Delaware
... size) - largest possible link-level frame. different link types, different ...
... size) - largest possible link-level frame. different link types, different ...
N5 NETWORKING BEST PRACTICES
... Management and Data ports should be configured on separate networks. Data Ports should use static IP addresses on a dedicated IP SAN network, ideally isolated from all other traffic. Network ports which are not being used should be set to Disabled. Flow Control should be enabled on all switc ...
... Management and Data ports should be configured on separate networks. Data Ports should use static IP addresses on a dedicated IP SAN network, ideally isolated from all other traffic. Network ports which are not being used should be set to Disabled. Flow Control should be enabled on all switc ...
Document
... Can use UTP or STP cables. 10GBASE-T (IEEE802.3an) will use Cat6 /w RJ45 connector for 55m connection. It can reach 100m with Cat6a cable. Consume more power and has higher latency than other 10GBASE Ethernet physical layers. ...
... Can use UTP or STP cables. 10GBASE-T (IEEE802.3an) will use Cat6 /w RJ45 connector for 55m connection. It can reach 100m with Cat6a cable. Consume more power and has higher latency than other 10GBASE Ethernet physical layers. ...
ppt
... – An external host can send a packet, with source IP address X and source port P, to the internal host only if the internal host had previously sent a packet to IP address X and port P. • Symmetric NAT – A symmetric NAT is a NAT where all requests from the same internal IP address and port to a spec ...
... – An external host can send a packet, with source IP address X and source port P, to the internal host only if the internal host had previously sent a packet to IP address X and port P. • Symmetric NAT – A symmetric NAT is a NAT where all requests from the same internal IP address and port to a spec ...
CompactLogix™ 5370 L2 Programmable Automation
... • Allows user to connect the Ethernet network in a ring topology • Resiliency from loss of one network connection allows to replace devices/drives one at a time without stopping production – similar to star topology • Ring supervisor capability (same as ETAP or 1756EN2TR) • Reduces the number of Eth ...
... • Allows user to connect the Ethernet network in a ring topology • Resiliency from loss of one network connection allows to replace devices/drives one at a time without stopping production – similar to star topology • Ring supervisor capability (same as ETAP or 1756EN2TR) • Reduces the number of Eth ...
Thailand
... Private AS number assigned by WMO secretariat. The AS numbers for neighbour centres are: Bangkok RTH : AS 64769 Tokyo RTH : AS 64520 Kuala Lumpur NMC : AS 65154 Vientiane NMC : AS 64771 ...
... Private AS number assigned by WMO secretariat. The AS numbers for neighbour centres are: Bangkok RTH : AS 64769 Tokyo RTH : AS 64520 Kuala Lumpur NMC : AS 65154 Vientiane NMC : AS 64771 ...
Storage for a Smarter Infrastructure Tom Roder – Top Gun Class
... Devices have network interfaces – port or nic (network interface card) Ethernet is the standard Speeds at which computers and servers can access data over the network is determined by the speed of the ‘wire’ they connect to These ‘wire’ or ‘media’ speeds are rapidly increasing to mind boggli ...
... Devices have network interfaces – port or nic (network interface card) Ethernet is the standard Speeds at which computers and servers can access data over the network is determined by the speed of the ‘wire’ they connect to These ‘wire’ or ‘media’ speeds are rapidly increasing to mind boggli ...
Switched LAN Architecture
... Static addresses are not aged out, and the switch always knows which port to send out traffic destined for that specific MAC address. As a result, there is no need to relearn or refresh which port the MAC address is connected to. One reason to implement static MAC addresses is to provide the network ...
... Static addresses are not aged out, and the switch always knows which port to send out traffic destined for that specific MAC address. As a result, there is no need to relearn or refresh which port the MAC address is connected to. One reason to implement static MAC addresses is to provide the network ...
IP Relay HWg-ER02b Manual
... HW VSP – Virtual Serial Port Virtual Serial Port driver is a software tool that adds a virtual serial port (e.g. COM5) to the operating system and redirects data from this port via the Ethernet network to another hardware interface. HW VSP Singleport – Virtual Serial Port (Windows) for one device ...
... HW VSP – Virtual Serial Port Virtual Serial Port driver is a software tool that adds a virtual serial port (e.g. COM5) to the operating system and redirects data from this port via the Ethernet network to another hardware interface. HW VSP Singleport – Virtual Serial Port (Windows) for one device ...
WGI WP307 GuidanceMaterial_DLR
... Ports are classified in three categories with associated range of values: ...
... Ports are classified in three categories with associated range of values: ...
Transport Layer
... delivered out of order to app connectionless: no handshaking between UDP sender & receiver each UDP segment handled independently of others ...
... delivered out of order to app connectionless: no handshaking between UDP sender & receiver each UDP segment handled independently of others ...
ch02
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
Parallel port

A parallel port is a type of interface found on computers (personal and otherwise) for connecting peripherals. In computing, a parallel port is a parallel communication physical interface. It is also known as a printer port or Centronics port. It was an industry de facto standard for many years, and was finally standardized as IEEE 1284 in the late 1990s, which defined the Enhanced Parallel Port (EPP) and Extended Capability Port (ECP) bi-directional versions. Today, the parallel port interface is seeing decreasing use because of the rise of Universal Serial Bus (USB) devices, along with network printing using Ethernet.The parallel port interface was originally known as the Parallel Printer Adapter on IBM PC-compatible computers. It was primarily designed to operate a line printer that used IBM's 8-bit extended ASCII character set to print text, but could also be used to adapt other peripherals. Graphical printers, along with a host of other devices, have been designed to communicate with the system.