Chapter 7 Lecture Presentation
... Each input port of packet switch has a forwarding table Lookup entry for VCI of incoming packet Determine output port (next hop) and insert VCI for next ...
... Each input port of packet switch has a forwarding table Lookup entry for VCI of incoming packet Determine output port (next hop) and insert VCI for next ...
Slide 1
... Choose the path that packets take around the network Packets are given a time to live (TTL) to prevent them travelling for ever ...
... Choose the path that packets take around the network Packets are given a time to live (TTL) to prevent them travelling for ever ...
Introduction to the Internet and Web
... • trailer /footer- It contains a couple of bits that tell the receiving device that it has reached the end of the packet. It may also have some type of error checking. The most common error checking used in packets is Cyclic Redundancy Check (CRC). ...
... • trailer /footer- It contains a couple of bits that tell the receiving device that it has reached the end of the packet. It may also have some type of error checking. The most common error checking used in packets is Cyclic Redundancy Check (CRC). ...
Overview
... with 35 users, probability that more than 10 users are active at same time is less than .0004. ...
... with 35 users, probability that more than 10 users are active at same time is less than .0004. ...
Wireless Communications and Networks
... Many packets over time can dynamically share the same node to node link ...
... Many packets over time can dynamically share the same node to node link ...
Congestion Control Algorithm - Computer Science and Engineering
... Goals: IPv6 1. Support billions of hosts, even with inefficient address space allocation 2. Reduce the size of the routing tables 3. Simplify the protocol, to allow routers to process packets faster 4. Provide better security (authentication and privacy) than current IP 5. Pay more attention to typ ...
... Goals: IPv6 1. Support billions of hosts, even with inefficient address space allocation 2. Reduce the size of the routing tables 3. Simplify the protocol, to allow routers to process packets faster 4. Provide better security (authentication and privacy) than current IP 5. Pay more attention to typ ...
Study Guide - Csulb.edu
... Packet switching: A technique used on computer networks for sending information that divides messages into small packets before sending. ...
... Packet switching: A technique used on computer networks for sending information that divides messages into small packets before sending. ...
Presentation - rossparker.org
... All original work used here is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. For more details please look at http://creativecommons.org/licenses/by-sa/3.0/. This license has been chosen to permit a high degree of sharing, whilst protecting the author’s control as ...
... All original work used here is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. For more details please look at http://creativecommons.org/licenses/by-sa/3.0/. This license has been chosen to permit a high degree of sharing, whilst protecting the author’s control as ...
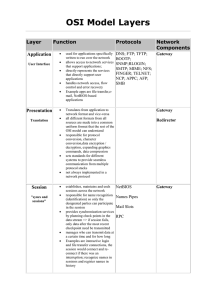
OSI Model Layers
... by planning check points in the data stream => if session fails, only data after the most recent checkpoint need be transmitted manages who can transmit data at a certain time and for how long Examples are interactive login and file transfer connections, the session would connect and reconnect if th ...
... by planning check points in the data stream => if session fails, only data after the most recent checkpoint need be transmitted manages who can transmit data at a certain time and for how long Examples are interactive login and file transfer connections, the session would connect and reconnect if th ...
ppt - Pacific University
... each time you connect to the internet) The client computers in LL21 and the dorms all ...
... each time you connect to the internet) The client computers in LL21 and the dorms all ...
chapter2ccna
... Internet Control Message Protocol (ICMP) works at the Network layer and is used by IP for many different services. •ICMP is a management protocol and messaging service provider for IP. •Its messages are carried as IP datagrams. ICMP packets have the following characteristics: • They can provide host ...
... Internet Control Message Protocol (ICMP) works at the Network layer and is used by IP for many different services. •ICMP is a management protocol and messaging service provider for IP. •Its messages are carried as IP datagrams. ICMP packets have the following characteristics: • They can provide host ...
Slide 1
... Authentication helps the network to establish the users’ identity, while wireless-hop security ensures data privacy for authenticated users and protection for the network. Repeat authentication at each hotspot location and the process might be configured differently. ...
... Authentication helps the network to establish the users’ identity, while wireless-hop security ensures data privacy for authenticated users and protection for the network. Repeat authentication at each hotspot location and the process might be configured differently. ...
one.world — System Support for Pervasive Applications
... Query all sources of packet events round-robin Integrate with interrupts Reflects duality of approaches Polling works well for predictable behavior: overload Interrupts work well for unpredictable behavior: regular load ...
... Query all sources of packet events round-robin Integrate with interrupts Reflects duality of approaches Polling works well for predictable behavior: overload Interrupts work well for unpredictable behavior: regular load ...
Chapter 4 PowerPoint
... The telephone network is a circuit-switched network – you have a dedicated path between you and the person you are talking to. The Internet is packetswitched. Everything sent over the Internet is broken up into small packets of data and sent on their way. ...
... The telephone network is a circuit-switched network – you have a dedicated path between you and the person you are talking to. The Internet is packetswitched. Everything sent over the Internet is broken up into small packets of data and sent on their way. ...
Safe internet Network Base for schools and business use: Οδηγός
... Safe Internet for Schools service filters all the traffic on a school network without the need to install any kind of software on the school’s computers or other devices. In this way, the entire school network is secure and protected even when visitors, students and/or members of personnel are conne ...
... Safe Internet for Schools service filters all the traffic on a school network without the need to install any kind of software on the school’s computers or other devices. In this way, the entire school network is secure and protected even when visitors, students and/or members of personnel are conne ...
IAP 01 – Introduction to Internet Architecture
... • A Protocol is a set of rules and regulations that governs the exchange of information between two or more entities. • It takes two (or more) communicating entities running the same protocol in order to accomplish a task. • All communication activity in Internet governed by protocols. • A protocol ...
... • A Protocol is a set of rules and regulations that governs the exchange of information between two or more entities. • It takes two (or more) communicating entities running the same protocol in order to accomplish a task. • All communication activity in Internet governed by protocols. • A protocol ...
ppt
... Distribution and the OS • There are various issues that the OS must deal with: – how to provide efficient network communication – what protocols to use – what is the application interface to remote apps (although this might be a language issue) – protection of distributed resources ...
... Distribution and the OS • There are various issues that the OS must deal with: – how to provide efficient network communication – what protocols to use – what is the application interface to remote apps (although this might be a language issue) – protection of distributed resources ...
ppt
... – Ethernet exponential back-off after a collision – TCP additive increase, multiplicative decrease ...
... – Ethernet exponential back-off after a collision – TCP additive increase, multiplicative decrease ...
Introduction
... Building Blocks Nodes: PC, special-purpose hardware… hosts Switches Routers ...
... Building Blocks Nodes: PC, special-purpose hardware… hosts Switches Routers ...
Chapter 4 : TCP/IP and OSI
... • Segregation means that no other software needs to be concerned about net specifics ...
... • Segregation means that no other software needs to be concerned about net specifics ...
No Slide Title
... Centrally managed, configured and deployed. Monitors each and every Business Transaction that you choose ...
... Centrally managed, configured and deployed. Monitors each and every Business Transaction that you choose ...
HHS - Complete Table of Contents and Glossary
... Anonymous FTP – A method by which computer files are made available for downloading by the general public awk – A programming language designed for working with strings. backdoors – An undocumented way of gaining access to a program, online service or an entire computer system. Baud – bits per secon ...
... Anonymous FTP – A method by which computer files are made available for downloading by the general public awk – A programming language designed for working with strings. backdoors – An undocumented way of gaining access to a program, online service or an entire computer system. Baud – bits per secon ...
EECC694 - Shaaban
... – Used only when other congestion control methods in place fail. – When capacity is reached, routers or switches may discard a number of incoming packets to reduce their load. EECC694 - Shaaban #4 lec #8 Spring2000 3-30-2000 ...
... – Used only when other congestion control methods in place fail. – When capacity is reached, routers or switches may discard a number of incoming packets to reduce their load. EECC694 - Shaaban #4 lec #8 Spring2000 3-30-2000 ...