Document
... Packet Loss • Packet loss is determined as the probability of a packet being lost in transit from a source A to a destination B. • Applications requiring reliable transmission e.g. Bulk data transfers, use retransmission, which reduces performance. • In addition, congestion-sensitive protocols such ...
... Packet Loss • Packet loss is determined as the probability of a packet being lost in transit from a source A to a destination B. • Applications requiring reliable transmission e.g. Bulk data transfers, use retransmission, which reduces performance. • In addition, congestion-sensitive protocols such ...
ch13
... Under light load, the 5token bus introduces unnecessary delays because of the overhead. To access the bus, an NIU has to wait for the token to be passed around, even if no other NIU is attempting to access the bus. Thus, CSMA/CD is preferable under light loads. 13.17 (BL3) This is a research exerci ...
... Under light load, the 5token bus introduces unnecessary delays because of the overhead. To access the bus, an NIU has to wait for the token to be passed around, even if no other NIU is attempting to access the bus. Thus, CSMA/CD is preferable under light loads. 13.17 (BL3) This is a research exerci ...
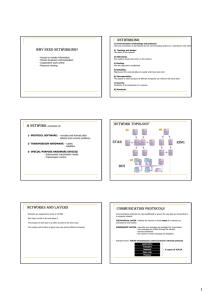
WHY NEED NETWORKING? NETWORKING NETWORK
... For example, all marketing personnel may be spread throughout a building. Yet if they are all assigned to a single VLAN, they can share resources and bandwidth as if they were connected to the same segment. ...
... For example, all marketing personnel may be spread throughout a building. Yet if they are all assigned to a single VLAN, they can share resources and bandwidth as if they were connected to the same segment. ...
ppt - Iowa State University
... allowed to send one packet 4. After transmission, DCij will be decreased by packet length each time a packet is transmitted DCij is used to calculate IFSij (time before transmit or back-off): larger DCij, smaller IFSij ...
... allowed to send one packet 4. After transmission, DCij will be decreased by packet length each time a packet is transmitted DCij is used to calculate IFSij (time before transmit or back-off): larger DCij, smaller IFSij ...
Lecture 1 - cda college
... A protocol, in contrast, is a set of rules governing the format and meaning of the packets, or messages that are exchanged by the peer entities within a layer. Entities use protocols to implement their service definitions. They are free to change their protocols at will, provided they do not change ...
... A protocol, in contrast, is a set of rules governing the format and meaning of the packets, or messages that are exchanged by the peer entities within a layer. Entities use protocols to implement their service definitions. They are free to change their protocols at will, provided they do not change ...
IP-Forwarding
... Forwarding decisions based only on data link layer header, that is the MAC DA. Use a table made from observing which addresses are seen on each port. No more than 7 bridges in diameter. Today’s ethernet environments use lots of ethernet switches, reducing the collision domain. Collision domain is th ...
... Forwarding decisions based only on data link layer header, that is the MAC DA. Use a table made from observing which addresses are seen on each port. No more than 7 bridges in diameter. Today’s ethernet environments use lots of ethernet switches, reducing the collision domain. Collision domain is th ...
IP spoofing - University Of Worcester
... A DDOS attack has occurred when attacker: » gains access to a wide number of computers/devices » uses them to launch a coordinated attack against the IP address of a “victim” computer ...
... A DDOS attack has occurred when attacker: » gains access to a wide number of computers/devices » uses them to launch a coordinated attack against the IP address of a “victim” computer ...
Routing
... It is a collection of set of ASS. internet consist of connection of multiple backbone networks called service providers. service provider may be private or government . backbone providers large companies ...
... It is a collection of set of ASS. internet consist of connection of multiple backbone networks called service providers. service provider may be private or government . backbone providers large companies ...
A Semantic-based Middleware for Multimedia Collaborative
... Efficient buffer management for Application Data Unit * Goal: to prevent payload movements in memory * Sender modules create an output buffer that can hold following “headers” and “tails” . * Receiver module needs to allocate worst case buffer size. A ...
... Efficient buffer management for Application Data Unit * Goal: to prevent payload movements in memory * Sender modules create an output buffer that can hold following “headers” and “tails” . * Receiver module needs to allocate worst case buffer size. A ...
DOS Defenses - Dr. Stephen C. Hayne
... connections while target machine waits for third part of handshake Send more SYN packets Target machine will allocate a small amount of resources to remember each SYN packet as it is transmitted ...
... connections while target machine waits for third part of handshake Send more SYN packets Target machine will allocate a small amount of resources to remember each SYN packet as it is transmitted ...
ECE537-Class 9_2009 - Electrical & Computer Engineering
... • Need to incorporate bursty and stream traffic in TCP/IP architecture • Increase capacity – Faster links, switches, routers – Intelligent routing policies – End-to-end flow control ...
... • Need to incorporate bursty and stream traffic in TCP/IP architecture • Increase capacity – Faster links, switches, routers – Intelligent routing policies – End-to-end flow control ...
Performance analysis of an IP based protocol stack for WSNs
... Hossain, "Performance analysis of an IP based protocol stack for WSNs," 2016 IEEE Conference on Computer Communications Workshops ...
... Hossain, "Performance analysis of an IP based protocol stack for WSNs," 2016 IEEE Conference on Computer Communications Workshops ...
ActionRuler_TP_front_08Mar11 copy
... INTRACOM TELECOM is an international telecommunication systems vendor operating in Eastern Europe, the Middle East & Africa, Russia, the CIS and Asia-Pacific. Over 100 customers in more than 50 countries choose INTRACOM TELECOM for its state-of-the-art products and solutions. INTRACOM TELECOM has 2, ...
... INTRACOM TELECOM is an international telecommunication systems vendor operating in Eastern Europe, the Middle East & Africa, Russia, the CIS and Asia-Pacific. Over 100 customers in more than 50 countries choose INTRACOM TELECOM for its state-of-the-art products and solutions. INTRACOM TELECOM has 2, ...
Digital IDs
... • When you send an e-mail message, Outlook informs you that the message is being signed. • When you receive a signed message, you will see a header named Signed and a Digital Signature button. • You can also encrypt messages by checking the option under the Security tab. ...
... • When you send an e-mail message, Outlook informs you that the message is being signed. • When you receive a signed message, you will see a header named Signed and a Digital Signature button. • You can also encrypt messages by checking the option under the Security tab. ...
Chapter 4 : TCP/IP and OSI
... Logic needed to support various applications Each type of application (file transfer, remote access) requires different software on this layer ...
... Logic needed to support various applications Each type of application (file transfer, remote access) requires different software on this layer ...
The Internet as a Universal Communication Network
... • Duration: 10s of seconds - 2 minutes • Usually preceeding changes in the fixed part of the delay • Often happen simultaneously on more than one path of a provider ...
... • Duration: 10s of seconds - 2 minutes • Usually preceeding changes in the fixed part of the delay • Often happen simultaneously on more than one path of a provider ...
Hermes: An Integrated CPU/GPU Microarchitecture for IP Routing
... Source Mac :new Dest Mac :new ---------------------------IP Header: Source IP :x Dest IP :y ---------------------------Data ...
... Source Mac :new Dest Mac :new ---------------------------IP Header: Source IP :x Dest IP :y ---------------------------Data ...
Gelman, Alex - Panasonic - IEEE-SA
... Wireless: UWB, Bluetooth, IEEE 802.11 Wireline: HPNA, HomePlug ...
... Wireless: UWB, Bluetooth, IEEE 802.11 Wireline: HPNA, HomePlug ...
IEEE 802.11 Wireless LAN Draft Standard
... between a subscriber site and a core network such as the public telephone network and the Internet. This wireless broadband access standard provides the missing link for the "last mile" connection in metropolitan area networks where DSL, Cable and other broadband access methods are not available or ...
... between a subscriber site and a core network such as the public telephone network and the Internet. This wireless broadband access standard provides the missing link for the "last mile" connection in metropolitan area networks where DSL, Cable and other broadband access methods are not available or ...
End to End and Innovation - Labs
... • We’ve taken this model of abstraction of functionality well beyond the traditional two-party virtual circuit model – Its still an overlay across a basic network – Its still defined and supported at the “ends” – Its no longer a two party model - its multi-party peering – Its no longer a single beha ...
... • We’ve taken this model of abstraction of functionality well beyond the traditional two-party virtual circuit model – Its still an overlay across a basic network – Its still defined and supported at the “ends” – Its no longer a two party model - its multi-party peering – Its no longer a single beha ...
Document
... • TCP/IP protocols matured quicker than similar OSI protocols – When the need for interoperability across networks was recognized, only TCP/IP was available and ready to go ...
... • TCP/IP protocols matured quicker than similar OSI protocols – When the need for interoperability across networks was recognized, only TCP/IP was available and ready to go ...
Network - Missouri State University
... • Virtual private network (VPN) - a way to use the public telecommunication infrastructure (e.g., Internet) to provide secure access to an organization’s network • Valued-added network (VAN) - a private network, provided by a ______ party, for exchanging information through a high capacity connectio ...
... • Virtual private network (VPN) - a way to use the public telecommunication infrastructure (e.g., Internet) to provide secure access to an organization’s network • Valued-added network (VAN) - a private network, provided by a ______ party, for exchanging information through a high capacity connectio ...
ppt - Courses
... 2008 ISP Infrastructure Security Report (Arbor, 2008) - Largest DDoS attack peak traffic volume of 40Gbps ...
... 2008 ISP Infrastructure Security Report (Arbor, 2008) - Largest DDoS attack peak traffic volume of 40Gbps ...
Internetworking of connectionless and connection
... either the CL network or CO network, internetworking should allow for the exchange of routing information (peer model) • Requiring all CO nodes to have CL capability seems too constraining (an MPLS requirement) • Hence, our proposed solution: – Share routing data – “Halt” or “turn back traffic” whil ...
... either the CL network or CO network, internetworking should allow for the exchange of routing information (peer model) • Requiring all CO nodes to have CL capability seems too constraining (an MPLS requirement) • Hence, our proposed solution: – Share routing data – “Halt” or “turn back traffic” whil ...