CISSP Guide to Security Essentials, Ch4
... Technologies (cont.) • Bluetooth (cont.) – Devices can authenticate through a process called “pairing”, during which two devices can exchange a cryptographic secret key that the two devices can later use ...
... Technologies (cont.) • Bluetooth (cont.) – Devices can authenticate through a process called “pairing”, during which two devices can exchange a cryptographic secret key that the two devices can later use ...
Cisco IP SLA`s
... • Optimize IP business applications and services Voice over IP, Video, and VPN ...
... • Optimize IP business applications and services Voice over IP, Video, and VPN ...
Business Data Communications and Networking
... the Web was quite unknown until late 1992 -then a “stunning pattern of growth set in”: “a research site’s Web traffic began to double every 6 weeks, and continued to do so for 2 full years!!!” by 1994, Web traffic wholly dominated the site’s activities [Paxson,1996]. ...
... the Web was quite unknown until late 1992 -then a “stunning pattern of growth set in”: “a research site’s Web traffic began to double every 6 weeks, and continued to do so for 2 full years!!!” by 1994, Web traffic wholly dominated the site’s activities [Paxson,1996]. ...
D_UCY_WP4_41_c2, Specification on E2E UMTS simulator
... be based on fast and accurate simulation methods for multi-user and multi-rate traffic. To achieve reliable and significant results, WP4 needs to develop a powerful, parallel simulation environment that enables Enhanced UMTS network performance evaluation with the necessary level of system detail. T ...
... be based on fast and accurate simulation methods for multi-user and multi-rate traffic. To achieve reliable and significant results, WP4 needs to develop a powerful, parallel simulation environment that enables Enhanced UMTS network performance evaluation with the necessary level of system detail. T ...
Overview Discovery & Exploration
... Working at a Small-toor Small Businesses Medium Business or ISP ...
... Working at a Small-toor Small Businesses Medium Business or ISP ...
- IEEE Mentor
... Root mesh points are either portals or shared edge nodes that source or sink data flows such as servers. Other nodes in the mesh are Mesh Access Points or edge nodes with user interfaces or they are transit nodes – mesh points without local interfaces that source or sink data. A deployed network may ...
... Root mesh points are either portals or shared edge nodes that source or sink data flows such as servers. Other nodes in the mesh are Mesh Access Points or edge nodes with user interfaces or they are transit nodes – mesh points without local interfaces that source or sink data. A deployed network may ...
IP Routing - courses.psu.edu
... • has maximum allowable hop count of 15 • is inefficient on large networks • uses three different timers – route update timer – route invalid timer – flush timer ...
... • has maximum allowable hop count of 15 • is inefficient on large networks • uses three different timers – route update timer – route invalid timer – flush timer ...
PDF document
... matter. A continual analysis of termination, collocation, leased lines and broadband access prices, and the update of prices for cable distribution services of all operators, as well as the overview of roaming charges of the national mobile operators for 50 selected countries continued. Since the La ...
... matter. A continual analysis of termination, collocation, leased lines and broadband access prices, and the update of prices for cable distribution services of all operators, as well as the overview of roaming charges of the national mobile operators for 50 selected countries continued. Since the La ...
Comparison of LTE and WiMAX
... This article provides a high-level comparison between LTE and WiMAX. The focus of paper is on two primary areas: System Architecture and Physical Layer. The System Architecture describes the different functional elements in LTE and WiMAX and attempts to map similar functionality (such ...
... This article provides a high-level comparison between LTE and WiMAX. The focus of paper is on two primary areas: System Architecture and Physical Layer. The System Architecture describes the different functional elements in LTE and WiMAX and attempts to map similar functionality (such ...
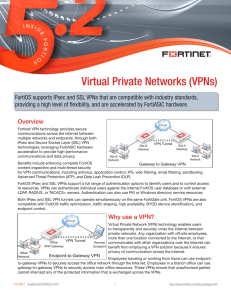
Virtual Private Networks (VPNs)
... security profiles. Their login credentials also determine the options and bookmarks that the web portal displays. IPsec VPN can also be used for endpoint-to-gateway communication by installing IPsec VPN clients on the endpoints. This is a popular option used by many organizations, but SSL VPN is typ ...
... security profiles. Their login credentials also determine the options and bookmarks that the web portal displays. IPsec VPN can also be used for endpoint-to-gateway communication by installing IPsec VPN clients on the endpoints. This is a popular option used by many organizations, but SSL VPN is typ ...
Towards Efficient and Robust Multihop Wireless Networks
... Multihop wireless networks provide ubiquitous Internet connectivity and support diverse applications, including real-time media-rich applications, in an efficient and robust manner Our focus is on 802.11 and IP-based networks Kimaya Mittal, Ph.D. Dissertation Proposal ...
... Multihop wireless networks provide ubiquitous Internet connectivity and support diverse applications, including real-time media-rich applications, in an efficient and robust manner Our focus is on 802.11 and IP-based networks Kimaya Mittal, Ph.D. Dissertation Proposal ...
ccna3 3.0-04 Introduction to LAN Switching
... Bridges “learn” network segments by building an address table, a CAM (Content Address Memory), containing the (MAC) address of each network device that accesses the bridge and pairs it with its network segment. Collision domains are created, not broadcast domains. ...
... Bridges “learn” network segments by building an address table, a CAM (Content Address Memory), containing the (MAC) address of each network device that accesses the bridge and pairs it with its network segment. Collision domains are created, not broadcast domains. ...
NetScreen-Hardware Security Client
... Juniper Networks NetScreen-Hardware Security Client The Juniper Networks NetScreen-Hardware Security Client, combined with NetScreen-Security Manager, is Juniper’s most cost effective security solution for the fixed telecommuter and small remote office. It can easily be deployed and managed in large ...
... Juniper Networks NetScreen-Hardware Security Client The Juniper Networks NetScreen-Hardware Security Client, combined with NetScreen-Security Manager, is Juniper’s most cost effective security solution for the fixed telecommuter and small remote office. It can easily be deployed and managed in large ...
3rd Edition, Chapter 5
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
OS6850 AOS 6.4.3 R01 Release Notes
... - Flexible Inner DSCP/ToS Mapping to Outer 802.1p - QOS Statistics ...
... - Flexible Inner DSCP/ToS Mapping to Outer 802.1p - QOS Statistics ...
Slides
... • BGP processing – create POP to POP (or even prefix to prefix) matrixes – correlate big volume shifts to routing changes • Internal routing (e.g. IS/IS) processing – traffic split of peers on internal (backbone) links • NetFlow collection on multiple points (routing tracing) – But this is not reall ...
... • BGP processing – create POP to POP (or even prefix to prefix) matrixes – correlate big volume shifts to routing changes • Internal routing (e.g. IS/IS) processing – traffic split of peers on internal (backbone) links • NetFlow collection on multiple points (routing tracing) – But this is not reall ...
Configuring VoIP for SonicOS Enhanced
... The Session Initiation Protocol (SIP) standard was developed by the Internet Engineering Task Force (IETF). RFC 2543 was released in March 1999. RFC 3261 was released in June 2002. SIP is a signaling protocol for initiating, managing and terminating sessions. SIP supports ‘presence’ and mobility and ...
... The Session Initiation Protocol (SIP) standard was developed by the Internet Engineering Task Force (IETF). RFC 2543 was released in March 1999. RFC 3261 was released in June 2002. SIP is a signaling protocol for initiating, managing and terminating sessions. SIP supports ‘presence’ and mobility and ...
Cisco Live 2014
... • Works with existing PE equipment – Multivendor PE support – No upgrade requirements for PE or any MPLS VPN backbone router ...
... • Works with existing PE equipment – Multivendor PE support – No upgrade requirements for PE or any MPLS VPN backbone router ...
Application of Mininet
... it knows that this PC is connected to this port and the traffic to this PC needs to only ben sent to that port and not to any of the others. The broadcasting happens at the beginning. Most of the traffic only goes where it needs to go rather than to every port. So a switch is faster. When there's hi ...
... it knows that this PC is connected to this port and the traffic to this PC needs to only ben sent to that port and not to any of the others. The broadcasting happens at the beginning. Most of the traffic only goes where it needs to go rather than to every port. So a switch is faster. When there's hi ...
G.8032 Ethernet Ring Protection
... A set of carrier-grade fault management and performance monitoring capabilities (operating in the data plane) which are appropriate for packet networks and support the network and services at different nested levels • Mechanisms for monitoring the network infrastructure which enhance the general beh ...
... A set of carrier-grade fault management and performance monitoring capabilities (operating in the data plane) which are appropriate for packet networks and support the network and services at different nested levels • Mechanisms for monitoring the network infrastructure which enhance the general beh ...
3rd Edition, Chapter 5
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
No Slide Title
... Regular routing updates: Every 30 seconds, send all or part of the routing tables to every neighbor. Triggered Updates: Whenever the metric for a route changes, send data that has changed. ...
... Regular routing updates: Every 30 seconds, send all or part of the routing tables to every neighbor. Triggered Updates: Whenever the metric for a route changes, send data that has changed. ...
SNMP - University of Greenwich
... next object on which a GetNext is executed. The walk ends when an object is returned that is beyond the scope of the request. ...
... next object on which a GetNext is executed. The walk ends when an object is returned that is beyond the scope of the request. ...