Why the SurfBeam System Should Be Your Internet
... working to transform satellite broadband with ViaSat-1, expected to be the world’s largest capacity broadband satellite. In addition to satellites and ground system technology, our technical staff focuses on this challenge from many other angles. Data processing and acceleration techniques, more eff ...
... working to transform satellite broadband with ViaSat-1, expected to be the world’s largest capacity broadband satellite. In addition to satellites and ground system technology, our technical staff focuses on this challenge from many other angles. Data processing and acceleration techniques, more eff ...
CECS470
... – A formal description of message formats and the rules the two layers must follow to exchange those messages. – Protocol definitions range from how bits are placed on a wire to the format of an e-mail message. – Standard protocols allow different manufacturers' computers to communicate. These compu ...
... – A formal description of message formats and the rules the two layers must follow to exchange those messages. – Protocol definitions range from how bits are placed on a wire to the format of an e-mail message. – Standard protocols allow different manufacturers' computers to communicate. These compu ...
Computer Science 171L
... distributed over a large area using coaxial cable and amplifiers. The key innovations in cable TV are optical feeder links, digital compression techniques, and service integration. Today cable TV uses frequency-division multiplexing to transmit up to 69 analog TV channels, each 4.5 MHz wide. Transmi ...
... distributed over a large area using coaxial cable and amplifiers. The key innovations in cable TV are optical feeder links, digital compression techniques, and service integration. Today cable TV uses frequency-division multiplexing to transmit up to 69 analog TV channels, each 4.5 MHz wide. Transmi ...
Figure 7 Layers in the TCP/IP Protocol Suite
... • TCP/IP does not define any specific protocol for this layer either, but supports all standard and proprietary protocols. • At this level, the communication is also between two hops/nodes, either a computer or router. – The unit of communication is a packet called a frame, which encapsulates the da ...
... • TCP/IP does not define any specific protocol for this layer either, but supports all standard and proprietary protocols. • At this level, the communication is also between two hops/nodes, either a computer or router. – The unit of communication is a packet called a frame, which encapsulates the da ...
Review For Final - Eastern Illinois University
... workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
... workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
Enabling Trustworthy Service Evaluation in
... review attacks, i.e., linkability, rejection, and modification attacks, and develop sophisticated security mechanisms for the TSE to deal with these attacks. Specifically, the basic TSE (bTSE) enables users to distributedly and cooperatively submit their reviews in an integrated chain form by using ...
... review attacks, i.e., linkability, rejection, and modification attacks, and develop sophisticated security mechanisms for the TSE to deal with these attacks. Specifically, the basic TSE (bTSE) enables users to distributedly and cooperatively submit their reviews in an integrated chain form by using ...
Review For Final - Eastern Illinois University
... workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
... workstations/servers transmit a message: Workstation 1 sends a message to workstation 3: Workstation 2 sends a message to Server 1: Server 1 sends a message to workstation 3: ...
Presentation to Dr. Harvey Newman (Caltech) about NIIT SLAC
... • Next Generation Network Monitoring for Pakistan ...
... • Next Generation Network Monitoring for Pakistan ...
Looking deeper into ARQ “frames”
... – Both are frames (groups of bits); “Frame” means carrying payload data – Both ends might want to transmit data; more complicated. – May be distinguished by a type field in packet header (and/or time of transmission – e.g. WiFi acks) ...
... – Both are frames (groups of bits); “Frame” means carrying payload data – Both ends might want to transmit data; more complicated. – May be distinguished by a type field in packet header (and/or time of transmission – e.g. WiFi acks) ...
Next Generation Networks
... There are more than 200 million wireless subscribers in the world today; an additional 700 million more will be added over the next 15-20 years There are more than 200 million Cable TV subscribers in the world today; an additional 300 million more will be added over the next 15-20 years More t ...
... There are more than 200 million wireless subscribers in the world today; an additional 700 million more will be added over the next 15-20 years There are more than 200 million Cable TV subscribers in the world today; an additional 300 million more will be added over the next 15-20 years More t ...
Router Design and Optics
... Technology did not match people’s experience with IP • deploying ATM in LAN is complex (e.g. broadcast) • supporting connection-less service model on connection-based technology ...
... Technology did not match people’s experience with IP • deploying ATM in LAN is complex (e.g. broadcast) • supporting connection-less service model on connection-based technology ...
ipbasics
... Different IP addresses (from different subnets) on different interfaces Receives packets on one interface, and forwards them (usually out of another interface) to get them closer to their destination ...
... Different IP addresses (from different subnets) on different interfaces Receives packets on one interface, and forwards them (usually out of another interface) to get them closer to their destination ...
acceptable use policy
... While using Signetique’s service, Customer shall NOT (a) restrict or prevent any other user from using and having such access to the Internet (b) post or transmit any material likely to be construed as being illegal, obscene, threatening, abusive, offensive, indecent, libellous, defamatory, discrimi ...
... While using Signetique’s service, Customer shall NOT (a) restrict or prevent any other user from using and having such access to the Internet (b) post or transmit any material likely to be construed as being illegal, obscene, threatening, abusive, offensive, indecent, libellous, defamatory, discrimi ...
The UNIX operating system
... http://www.faqs.org/faqs/computer-security/most-commonqs/section-21.html http://en.wikipedia.org/wiki/Portscanning ...
... http://www.faqs.org/faqs/computer-security/most-commonqs/section-21.html http://en.wikipedia.org/wiki/Portscanning ...
Reviewing Traffic Classification - Sites personnels de TELECOM
... In the first days of the Internet, identifying the application associated with some network packets was not an issue whatsoever: protocols were assigned to well-known transportlayer ports by IANA [2]. Therefore, Port-based classification [49, 50, 53] simply extracted such value from the packet heade ...
... In the first days of the Internet, identifying the application associated with some network packets was not an issue whatsoever: protocols were assigned to well-known transportlayer ports by IANA [2]. Therefore, Port-based classification [49, 50, 53] simply extracted such value from the packet heade ...
Remote Access
... • Takes advantage of using the public Internet as if it were a private network • Allow the public Internet to be used privately • Prior to VPNs, organizations were forced to lease expensive data connections from private carriers so employees could remotely connect to the organization’s network cs490 ...
... • Takes advantage of using the public Internet as if it were a private network • Allow the public Internet to be used privately • Prior to VPNs, organizations were forced to lease expensive data connections from private carriers so employees could remotely connect to the organization’s network cs490 ...
Security & Cryptography
... exchanging encryption ciphers that will be used in a later encrypted session IPSec is an overall term used to describe encrypted data communication over IP, using the keys exchanged with IKE ...
... exchanging encryption ciphers that will be used in a later encrypted session IPSec is an overall term used to describe encrypted data communication over IP, using the keys exchanged with IKE ...
8[1]. Chapter 9 Norton
... The network allows communication and collaboration between users Networking is a group of technologies working together. These technologies include: Media is the wiring that connects the computers 2. Hardware needs to be installed to connect the media 3. Software needs to be written to handle ne ...
... The network allows communication and collaboration between users Networking is a group of technologies working together. These technologies include: Media is the wiring that connects the computers 2. Hardware needs to be installed to connect the media 3. Software needs to be written to handle ne ...
Chapter 2 Networking Standards and the OSI Model
... converting the packets/datagrams into frames, the MAC sublayer converts the frames into bits, which the Physical layer can put on the wire. These steps are known as data encapsulation. When the bits stream arrives at the destination, the process is reversed and each layer will remove their correspon ...
... converting the packets/datagrams into frames, the MAC sublayer converts the frames into bits, which the Physical layer can put on the wire. These steps are known as data encapsulation. When the bits stream arrives at the destination, the process is reversed and each layer will remove their correspon ...
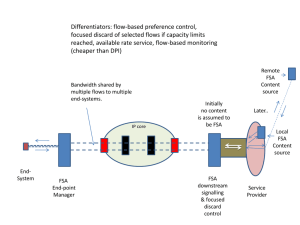
Document
... No standard approach today that addresses the unique needs of most remote monitoring and control applications • Enables the broad-based deployment of reliable wireless networks with low-complexity, low-cost solutions. • Provides the ability to run for years on inexpensive primary batteries for a typ ...
... No standard approach today that addresses the unique needs of most remote monitoring and control applications • Enables the broad-based deployment of reliable wireless networks with low-complexity, low-cost solutions. • Provides the ability to run for years on inexpensive primary batteries for a typ ...
September 2016 report
... The transport layer isolates the session and higher layers from the network itself. The transport layer is responsible for the reliable transmission of messages between two application nodes of a network and for ensuring that the messages are received in the order in which they were sent. The transp ...
... The transport layer isolates the session and higher layers from the network itself. The transport layer is responsible for the reliable transmission of messages between two application nodes of a network and for ensuring that the messages are received in the order in which they were sent. The transp ...
Firewalls
... Three subsets of packet filtering firewalls: Static filtering: requires that filtering rules governing how the firewall decides which packets are allowed and which are denied are developed and installed Dynamic filtering: allows firewall to react to emergent event and update or create rules to ...
... Three subsets of packet filtering firewalls: Static filtering: requires that filtering rules governing how the firewall decides which packets are allowed and which are denied are developed and installed Dynamic filtering: allows firewall to react to emergent event and update or create rules to ...
The Packet Filter: A Basic Network Security Tool
... operating systems can be configured for packet filtering. Packet filtering can be added to *nix operating systems. Support for packet filtering via ipchains is included by default in the Linux kernel. Windows NT and Windows 2000 support packet filtering. Virtually all commercial firewalls support pa ...
... operating systems can be configured for packet filtering. Packet filtering can be added to *nix operating systems. Support for packet filtering via ipchains is included by default in the Linux kernel. Windows NT and Windows 2000 support packet filtering. Virtually all commercial firewalls support pa ...
















![8[1]. Chapter 9 Norton](http://s1.studyres.com/store/data/008740653_1-fe1d78b3a4d5882ed6aebaaa8846aa3c-300x300.png)