5G radio network architecture
... needs technology advances, including dynamic power control that is optimally coordinated among the users and with surrounding cells so that there is proportionality between the traffic and the energy consumption [5GNOW project http://www.5gnow.eu/]. There is a need for network architecture advances ...
... needs technology advances, including dynamic power control that is optimally coordinated among the users and with surrounding cells so that there is proportionality between the traffic and the energy consumption [5GNOW project http://www.5gnow.eu/]. There is a need for network architecture advances ...
Terms of using WI-FI
... b) Unauthorised use of software or other products subject to protection of intellectual property of content available on the Internet, c) Damage done by software owned by users, or any damage caused indirectly or directly during using internet connection via WiFi Network, d) D ...
... b) Unauthorised use of software or other products subject to protection of intellectual property of content available on the Internet, c) Damage done by software owned by users, or any damage caused indirectly or directly during using internet connection via WiFi Network, d) D ...
Is an Alligator Better Than an Armadillo? Is an
... be difficult because many cost and performance metrics could be used. Suppose someone asked you to select the best animal. What features would you use to compare, say, an alligator and an armadillo? In some ways, the two are very similar: both have four legs, a rugged exterior, and sharp claws. Howe ...
... be difficult because many cost and performance metrics could be used. Suppose someone asked you to select the best animal. What features would you use to compare, say, an alligator and an armadillo? In some ways, the two are very similar: both have four legs, a rugged exterior, and sharp claws. Howe ...
22-IPv6-BF - EECS People Web Server
... • IPv6 Neighbor Discovery (ND) replaces ARP and ICMP • Hosts use ND to discover neighboring routers and to discover addresses, address prefixes, and other parameters. • Routers use ND to advertise their presence, configure host parameters, inform hosts of next-hop address and on-link ...
... • IPv6 Neighbor Discovery (ND) replaces ARP and ICMP • Hosts use ND to discover neighboring routers and to discover addresses, address prefixes, and other parameters. • Routers use ND to advertise their presence, configure host parameters, inform hosts of next-hop address and on-link ...
Chapter 2 - William Stallings, Data and Computer
... • The peer layers communicate using a set of rules or conventions known as a protocol. • Instead of implementing the complex logic for this as a single module, the task is broken up into modules. • In a protocol architecture, the modules are arranged in a vertical stack, each layer in the stack perf ...
... • The peer layers communicate using a set of rules or conventions known as a protocol. • Instead of implementing the complex logic for this as a single module, the task is broken up into modules. • In a protocol architecture, the modules are arranged in a vertical stack, each layer in the stack perf ...
Informal Quiz 7 (contd) - ECSE - Rensselaer Polytechnic Institute
... transmission at rates at or below OC-48c Shivkumar Kalyanaraman Rensselaer Polytechnic Institute EDFAs amplify in an -sensitive manner ...
... transmission at rates at or below OC-48c Shivkumar Kalyanaraman Rensselaer Polytechnic Institute EDFAs amplify in an -sensitive manner ...
CS 294-7: Cellular Digital Packet Data (CDPD)
... – CDPD network trackes location of ES’ and routes them network datagrams – ES’ address does NOT imply location; current subnetwork “point of attachment” determines this – ES’ are associated with the CDPD network’s routing domain, not the user’s corporate home network – Mobility support functions: » ...
... – CDPD network trackes location of ES’ and routes them network datagrams – ES’ address does NOT imply location; current subnetwork “point of attachment” determines this – ES’ are associated with the CDPD network’s routing domain, not the user’s corporate home network – Mobility support functions: » ...
Chapter 8 - Department of Information Technology
... three types of firewalls: stateless packet filters stateful packet filters application gateways 8: Network Security ...
... three types of firewalls: stateless packet filters stateful packet filters application gateways 8: Network Security ...
ppt - (Walid) Ben Ali
... • Sometimes called Start/Stop Transmission • Characteristics of file transfer protocols – Designed to transmit error-free data – Group data into blocks to be transmitted (rather sending character by character) ...
... • Sometimes called Start/Stop Transmission • Characteristics of file transfer protocols – Designed to transmit error-free data – Group data into blocks to be transmitted (rather sending character by character) ...
Mobile Communications - Georgetown University
... products have to follow many national restrictions if working wireless, it takes a vary long time to establish global solutions like, e.g., IMT-2000 ...
... products have to follow many national restrictions if working wireless, it takes a vary long time to establish global solutions like, e.g., IMT-2000 ...
Document
... • This shared link concept works well as a local area network – if too large a network – with many hosts – each host will get a small percentage of bandwidth M. Veeraraghavan ...
... • This shared link concept works well as a local area network – if too large a network – with many hosts – each host will get a small percentage of bandwidth M. Veeraraghavan ...
Mobile Communications
... products have to follow many national restrictions if working wireless, it takes a vary long time to establish global solutions like, e.g., IMT-2000 ...
... products have to follow many national restrictions if working wireless, it takes a vary long time to establish global solutions like, e.g., IMT-2000 ...
PPT
... • Use other means to route setup request • Each router allocates flow ID on local link • Creates mapping of inbound flow ID/port to outbound ...
... • Use other means to route setup request • Each router allocates flow ID on local link • Creates mapping of inbound flow ID/port to outbound ...
Statistical multiplexing in Cable TV networks
... Cable TV networks are running out of free frequencies due to increasing number of TV channels with higher video resolutions, ever growing need for higher broadband speeds, and new DOCSIS® standards. Statistical multiplexing enables efficient usage of bandwidth and ensures high quality viewing experi ...
... Cable TV networks are running out of free frequencies due to increasing number of TV channels with higher video resolutions, ever growing need for higher broadband speeds, and new DOCSIS® standards. Statistical multiplexing enables efficient usage of bandwidth and ensures high quality viewing experi ...
C07
... products have to follow many national restrictions if working wireless, it takes a vary long time to establish global solutions like, e.g., IMT-2000 ...
... products have to follow many national restrictions if working wireless, it takes a vary long time to establish global solutions like, e.g., IMT-2000 ...
The Transport Layer
... 2. Reduce packet count to reduce software overhead. 3. Minimize context switches. 4. Minimize copying. 5. You can buy more bandwidth but not lower delay. 6. Avoiding congestion is better than recovering from it. 7. Avoid timeouts. ...
... 2. Reduce packet count to reduce software overhead. 3. Minimize context switches. 4. Minimize copying. 5. You can buy more bandwidth but not lower delay. 6. Avoiding congestion is better than recovering from it. 7. Avoid timeouts. ...
Multimedia Traffic Security Architecture for the Internet of Things
... of content, tracing illegally distributed copies, and disabling unauthorized access to content [8]. Generally speaking, characteristics and requirements for watermarks in multimedia applications are totally different. Identification of the origin of multimedia content requires the embedding of a sin ...
... of content, tracing illegally distributed copies, and disabling unauthorized access to content [8]. Generally speaking, characteristics and requirements for watermarks in multimedia applications are totally different. Identification of the origin of multimedia content requires the embedding of a sin ...
In this project, we plan to establish a complete communications loop:
... has immediate knowledge of dropped frames and thus can respond faster than higherlevel protocols. It can take over the task of ensuring the reliable delivery of packets that are lost due to errors, effectively hiding these losses from TCP and avoiding congestion control measures [10]. Similarly, pac ...
... has immediate knowledge of dropped frames and thus can respond faster than higherlevel protocols. It can take over the task of ensuring the reliable delivery of packets that are lost due to errors, effectively hiding these losses from TCP and avoiding congestion control measures [10]. Similarly, pac ...
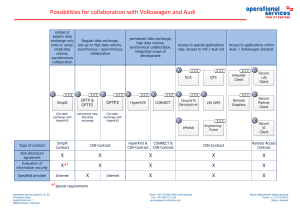
Possibilities for collaboration with Volkswagen
... HyperKVS is an application for data exchange, for audit-proof storage and for file conversion of CAx data to the format that is needed. HyperKVS is used by all parties that are involved within the process of product creation. Due to the worldwide use by more than 1.900 suppliers and partner companie ...
... HyperKVS is an application for data exchange, for audit-proof storage and for file conversion of CAx data to the format that is needed. HyperKVS is used by all parties that are involved within the process of product creation. Due to the worldwide use by more than 1.900 suppliers and partner companie ...
$doc.title
... Switch Fabric .......................................................................................................................................... 11 ...
... Switch Fabric .......................................................................................................................................... 11 ...
Constrained Application Protocol for Internet of Things
... protocols which are Alert, Handshake and application data, in some condition Change Cipher Spec protocol may replace one of them. Change Cipher Spec message is used to notify Record protocol to protect subsequent records with just-negotiate cipher suite and keys. [Raza13] Record protocol [E.Rescorla ...
... protocols which are Alert, Handshake and application data, in some condition Change Cipher Spec protocol may replace one of them. Change Cipher Spec message is used to notify Record protocol to protect subsequent records with just-negotiate cipher suite and keys. [Raza13] Record protocol [E.Rescorla ...
paper template (word format) for sample
... rating is given to a node only from the direct observation when the node does not cooperate, which results in the decreased reputation for that node. The positive rating, in contrast, is given from both direct observation and positive reports from other nodes, which results in the increased reputati ...
... rating is given to a node only from the direct observation when the node does not cooperate, which results in the decreased reputation for that node. The positive rating, in contrast, is given from both direct observation and positive reports from other nodes, which results in the increased reputati ...
Life in the fast lane
... Cablenet cable modem service in Kilkenny, Clonmel and Thurles. It gives a 512Kbps/128Kbps service for €35 including Vat over the TV charges with a €50 connection fee. These areas are accepting new subscribers, including businesses at the current €75 rate, which includes support, fixed internet proto ...
... Cablenet cable modem service in Kilkenny, Clonmel and Thurles. It gives a 512Kbps/128Kbps service for €35 including Vat over the TV charges with a €50 connection fee. These areas are accepting new subscribers, including businesses at the current €75 rate, which includes support, fixed internet proto ...