router isis as42
... Integrated IS-IS carries CLNS and IPv4 address families RFC5308 adds IPv6 address family support RFC5120 adds multi-topology support ...
... Integrated IS-IS carries CLNS and IPv4 address families RFC5308 adds IPv6 address family support RFC5120 adds multi-topology support ...
Delivering HPC Applications with Juniper Networks and Chelsio
... improve overall application performance. Called the “3-2-1” data center network architecture, the strategy asserts that today’s data center is far too complex, requiring three layers of switches to provide the required port densities. As a result of this three-tiered “tree” structure, east-west netw ...
... improve overall application performance. Called the “3-2-1” data center network architecture, the strategy asserts that today’s data center is far too complex, requiring three layers of switches to provide the required port densities. As a result of this three-tiered “tree” structure, east-west netw ...
UPS SYSTEM Communication Manual Network Interface Card
... Power and connections Before installing the NIC card, it is necessary to setup local parameters to allow communication in an ETHERNET network. Refer to Chapter 4 for details. Refer to figure 2-3 to make the power and communication connectors to the NIC card. 10. Verify that the jumpers setting are a ...
... Power and connections Before installing the NIC card, it is necessary to setup local parameters to allow communication in an ETHERNET network. Refer to Chapter 4 for details. Refer to figure 2-3 to make the power and communication connectors to the NIC card. 10. Verify that the jumpers setting are a ...
Secure Efficient Distance Vector Routing for Mobile Wireless Ad Hoc
... turn uses its own routing table to forward the packet along its next hop toward the destination. To maintain the routing tables, each node periodically transmits a routing update to to each of its neighbor routers, containing the information from its own routing table. Each node uses this informatio ...
... turn uses its own routing table to forward the packet along its next hop toward the destination. To maintain the routing tables, each node periodically transmits a routing update to to each of its neighbor routers, containing the information from its own routing table. Each node uses this informatio ...
Industrial Application of Coloured Petri Nets for Protocol Verification
... The protocol was revised such that the edge router always replies with the list of all currently assigned prefixes. State space: 34 nodes and 49 arcs. No dead markings and 11 home markings (constituting a single terminal SCC). Inspection showed that all home markings are consistently configu ...
... The protocol was revised such that the edge router always replies with the list of all currently assigned prefixes. State space: 34 nodes and 49 arcs. No dead markings and 11 home markings (constituting a single terminal SCC). Inspection showed that all home markings are consistently configu ...
Application of Mininet
... it knows that this PC is connected to this port and the traffic to this PC needs to only ben sent to that port and not to any of the others. The broadcasting happens at the beginning. Most of the traffic only goes where it needs to go rather than to every port. So a switch is faster. When there's hi ...
... it knows that this PC is connected to this port and the traffic to this PC needs to only ben sent to that port and not to any of the others. The broadcasting happens at the beginning. Most of the traffic only goes where it needs to go rather than to every port. So a switch is faster. When there's hi ...
9781305105430_PPT_ch03
... Network Technologies and Media • Unshielded Twisted pair (UTP) – Most common media type in LANs – Consists of 4 pairs of copper wires each twisted together – Comes in numbered categories ...
... Network Technologies and Media • Unshielded Twisted pair (UTP) – Most common media type in LANs – Consists of 4 pairs of copper wires each twisted together – Comes in numbered categories ...
ppt - Carnegie Mellon School of Computer Science
... and network management. » LSPs can be thought of as “programmable links” that can be set up under software control » on top of a simple, static hardware infrastructure ...
... and network management. » LSPs can be thought of as “programmable links” that can be set up under software control » on top of a simple, static hardware infrastructure ...
ATM
... and network management. » LSPs can be thought of as “programmable links” that can be set up under software control » on top of a simple, static hardware infrastructure ...
... and network management. » LSPs can be thought of as “programmable links” that can be set up under software control » on top of a simple, static hardware infrastructure ...
FIREWALL DEPLOYMENT AND CONFIGURATION
... building in order to protect the owners' lives and properties. Although firewall operation on network is not capable of protecting people's lives, it is still essential for protecting network sources from attacks. The first firewall for network security dates as early as in the late 1980s and was us ...
... building in order to protect the owners' lives and properties. Although firewall operation on network is not capable of protecting people's lives, it is still essential for protecting network sources from attacks. The first firewall for network security dates as early as in the late 1980s and was us ...
Static Routes
... Dynamic routing is when protocols are used to find networks and update routing tables on routers. Dynamic routing makes it possible to avoid the time-consuming process of configuring static routes. Dynamic routing use more CPU processing and network bandwidth than static routing ...
... Dynamic routing is when protocols are used to find networks and update routing tables on routers. Dynamic routing makes it possible to avoid the time-consuming process of configuring static routes. Dynamic routing use more CPU processing and network bandwidth than static routing ...
eMachines Wireless Supplement - Gateway Computer, Server
... wireless features on your notebook 54gTM, the most advanced wireless networking technology available, is incorporated into your notebook. Also known as 802.11g, this up-and-coming wireless networking standard is up to 5 times faster than the widely used, older standard, 802.11b. Instead of communica ...
... wireless features on your notebook 54gTM, the most advanced wireless networking technology available, is incorporated into your notebook. Also known as 802.11g, this up-and-coming wireless networking standard is up to 5 times faster than the widely used, older standard, 802.11b. Instead of communica ...
Module 7 - IT, Sligo
... •To configure an interface to send RIP V1 packets •Router(config-if)#ip rip send version 1 •To configure an interface to send RIP V2 packets •Router(config-if)#ip rip send version 2 •To configure an interface to send RIP V1 and V2 packets •Router(config-if)#ip rip send version 1 2 •To configure and ...
... •To configure an interface to send RIP V1 packets •Router(config-if)#ip rip send version 1 •To configure an interface to send RIP V2 packets •Router(config-if)#ip rip send version 2 •To configure an interface to send RIP V1 and V2 packets •Router(config-if)#ip rip send version 1 2 •To configure and ...
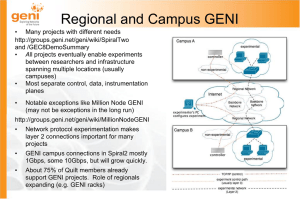
GENIConnections
... •Layer 2 Ethernet switches with dedicated 1 GbE and 10GbE connections •Layer 3 IP (management, control and general connectivity) • Programmable network hardware — NetFPGA card installed in rack mounted PC o acts as OpenFlow switch, programmable router, packet generator, etc. ...
... •Layer 2 Ethernet switches with dedicated 1 GbE and 10GbE connections •Layer 3 IP (management, control and general connectivity) • Programmable network hardware — NetFPGA card installed in rack mounted PC o acts as OpenFlow switch, programmable router, packet generator, etc. ...
What is NIDS?
... 1 hour at a busy site(100.2M data, 1.2M packets, 273K connections Second was a 2 hour HTTP traffic. (137MB, 197k packets, 6379 connections) Both tests yield same result. Execution time are same, memory usage was 200k higher with AM ...
... 1 hour at a busy site(100.2M data, 1.2M packets, 273K connections Second was a 2 hour HTTP traffic. (137MB, 197k packets, 6379 connections) Both tests yield same result. Execution time are same, memory usage was 200k higher with AM ...
What is the Access Grid?
... variety of modes. In the Access Grid environment, VNC allows a speaker to share his/her podium laptop with Access Grid display systems which can then project it at remote nodes. This is useful when a speaker wishes to give real-time demonstrations or present PowerPoint slides that include "fancy" fe ...
... variety of modes. In the Access Grid environment, VNC allows a speaker to share his/her podium laptop with Access Grid display systems which can then project it at remote nodes. This is useful when a speaker wishes to give real-time demonstrations or present PowerPoint slides that include "fancy" fe ...
20061004-IMSP2P
... • Network is unaware of the applications, this makes it scalable • Nothing should be done in the network that can be done in an end-system • Quality of Service (QoS) is a matter of bandwidth availability and not of central control ...
... • Network is unaware of the applications, this makes it scalable • Nothing should be done in the network that can be done in an end-system • Quality of Service (QoS) is a matter of bandwidth availability and not of central control ...
Wireless Local Area Networks (WLAN)
... Access points can have a varying amount of intelligence and functionality built-in. There are two main types of AP. “Thick” APs are fully functional and can handle all processes. “Thin” APs only include radios and antennas and rely on controllers (WLAN switches/appliances) for other functionality in ...
... Access points can have a varying amount of intelligence and functionality built-in. There are two main types of AP. “Thick” APs are fully functional and can handle all processes. “Thin” APs only include radios and antennas and rely on controllers (WLAN switches/appliances) for other functionality in ...
In classful addressing, the network address
... • Understand subnets and supernets TCP/IP Protocol Suite ...
... • Understand subnets and supernets TCP/IP Protocol Suite ...
Networks Oy - Roggeweck.net
... The GGSN is the gateway to external networks. Every connection to a fixed external data network has to go through a GGSN. The GGSN acts as the anchor point in a GPRS data connection even when the subscriber moves to another SGSN during roaming. The GGSN may accept connection request from SGSN that i ...
... The GGSN is the gateway to external networks. Every connection to a fixed external data network has to go through a GGSN. The GGSN acts as the anchor point in a GPRS data connection even when the subscriber moves to another SGSN during roaming. The GGSN may accept connection request from SGSN that i ...