IMC conference
... Select a basis set of k paths that fully describe O(n2) paths (k «O(n2)) • Monitor the loss rates of k paths, and infer the loss rates of all other paths • Applicable for any additive metrics, like latency ...
... Select a basis set of k paths that fully describe O(n2) paths (k «O(n2)) • Monitor the loss rates of k paths, and infer the loss rates of all other paths • Applicable for any additive metrics, like latency ...
PPT
... Multiple same-cost paths allowed (only one path in RIP) For each link, multiple cost metrics for different TOS (e.g., satellite link cost set “low” for best effort; high for real time) Integrated uni- and multicast support: Multicast OSPF (MOSPF) uses same topology data base as OSPF Hierarchical O ...
... Multiple same-cost paths allowed (only one path in RIP) For each link, multiple cost metrics for different TOS (e.g., satellite link cost set “low” for best effort; high for real time) Integrated uni- and multicast support: Multicast OSPF (MOSPF) uses same topology data base as OSPF Hierarchical O ...
userguide_plugin_v5
... 2. However, in order to support the Infiniband auto-detection, the default bootstrap should be upgraded. The Mellanox plugin installation will automatically replace and upgrade the bootstrap as part of its installation. Please note – if any server was online before installing the plugin, please rebo ...
... 2. However, in order to support the Infiniband auto-detection, the default bootstrap should be upgraded. The Mellanox plugin installation will automatically replace and upgrade the bootstrap as part of its installation. Please note – if any server was online before installing the plugin, please rebo ...
Chapter 2 Lecture Presentation
... The overall communications process between two or more machines connected across one or more networks is very complex Layering partitions related communications functions into groups that are manageable Each layer provides a service to the layer above Each layer operates according to a protocol Let’ ...
... The overall communications process between two or more machines connected across one or more networks is very complex Layering partitions related communications functions into groups that are manageable Each layer provides a service to the layer above Each layer operates according to a protocol Let’ ...
Routing protocol Chapter 4 4.1 Introduction
... available, in which case crankbacks are needed. Crankbacks require the management of more state information, which leads to increased hardware complexity. The routing protocol should be executed in parallel by all the SONET switches, without segmenting the network. This allows all the nodes to have ...
... available, in which case crankbacks are needed. Crankbacks require the management of more state information, which leads to increased hardware complexity. The routing protocol should be executed in parallel by all the SONET switches, without segmenting the network. This allows all the nodes to have ...
3rd Edition: Chapter 4
... Multiple same-cost paths allowed (only one path in RIP) For each link, multiple cost metrics for different TOS (e.g., satellite link cost set “low” for best effort; high for real time) Integrated uni- and multicast support: Multicast OSPF (MOSPF) uses same topology data base as OSPF Hierarchical O ...
... Multiple same-cost paths allowed (only one path in RIP) For each link, multiple cost metrics for different TOS (e.g., satellite link cost set “low” for best effort; high for real time) Integrated uni- and multicast support: Multicast OSPF (MOSPF) uses same topology data base as OSPF Hierarchical O ...
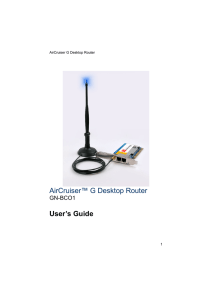
AirCruiser™ G Desktop Router User`s Guide
... fast flashing indicates faster transmissions. It has a beefed up 3dBi gain compared with the 2dBi antennas that are bundled with most standard routers on the market and that translates into better wireless performance! The AirCruiser G Desktop Router’s PCI form factor is a breakthrough in wireless n ...
... fast flashing indicates faster transmissions. It has a beefed up 3dBi gain compared with the 2dBi antennas that are bundled with most standard routers on the market and that translates into better wireless performance! The AirCruiser G Desktop Router’s PCI form factor is a breakthrough in wireless n ...
Virtual Slice Management and Resource
... In all previous papers before 2013, there is a common assumption that the SN network is fault-free, i.e., the underlying InP network remains operational at all times. The fault-free assumption is removed in the following paper, which considers a variant of VNE in the scenario where the SN network i ...
... In all previous papers before 2013, there is a common assumption that the SN network is fault-free, i.e., the underlying InP network remains operational at all times. The fault-free assumption is removed in the following paper, which considers a variant of VNE in the scenario where the SN network i ...
CCL Advanced Applications (Cont`d)
... • between Lawrence Berkeley & Argonne Nat’l lab • sending two video streams over the Internet – the priority marked stream : 8frames / sec – the standard stream : 1 frame /sec ...
... • between Lawrence Berkeley & Argonne Nat’l lab • sending two video streams over the Internet – the priority marked stream : 8frames / sec – the standard stream : 1 frame /sec ...
module10-rip
... address on the same subnet than the advertising router, if one exists (otherwise 0….0) ...
... address on the same subnet than the advertising router, if one exists (otherwise 0….0) ...
Deployment Status in Singapore
... Testbed to study the challenges of realising an all IP network QoS issues in core network and building an IP telephony system based on SIP ...
... Testbed to study the challenges of realising an all IP network QoS issues in core network and building an IP telephony system based on SIP ...
PowerPoint - DePaul University
... Advertise infinity for route and wait a period of time before switching routes. Hope that news of ...
... Advertise infinity for route and wait a period of time before switching routes. Hope that news of ...
Letter Logo
... 2.4.1.1 NOTE 1 – The cable routing is important if leaving the system block. Consult Recommendation K.27 for guidance. 2.4.1.2 NOTE 2 – The direct connection of the outer conductors of co-axial cables to the bonding network at the transmit and receive interfaces may, because of differences in earth ...
... 2.4.1.1 NOTE 1 – The cable routing is important if leaving the system block. Consult Recommendation K.27 for guidance. 2.4.1.2 NOTE 2 – The direct connection of the outer conductors of co-axial cables to the bonding network at the transmit and receive interfaces may, because of differences in earth ...
Routing in IPv6 over Low-Power Wireless Personal Area Networks
... 6LoWPANs (IPv6-based Low-Power Personal Area Networks) are formulated by devices that are compatible with the IEEE 802.15.4 standard. To moderate the effects of network mobility, the Internet Protocol (IP) does not calculate routes; it is left to a routing protocol, which maintains routing tables in ...
... 6LoWPANs (IPv6-based Low-Power Personal Area Networks) are formulated by devices that are compatible with the IEEE 802.15.4 standard. To moderate the effects of network mobility, the Internet Protocol (IP) does not calculate routes; it is left to a routing protocol, which maintains routing tables in ...
PYLON: An Architectural Framework for Ad-Hoc QoS
... While SWAN provides a model that deals with traffic on a per-class basis, it uses merely two levels of service, best effort and real-time traffic. Both levels can be simply mapped to certain DSCPs with known PHB (based on bandwidth requirement) in order to facilitate extranet QoS. Using this concept ...
... While SWAN provides a model that deals with traffic on a per-class basis, it uses merely two levels of service, best effort and real-time traffic. Both levels can be simply mapped to certain DSCPs with known PHB (based on bandwidth requirement) in order to facilitate extranet QoS. Using this concept ...
Advanced Networking Concepts & Troubleshooting
... Successor routes • Successor route is used by EIGRP to forward traffic to a destination • A successor routes may be backed up by a feasible successor route • Successor routes are stored in both the topology table and the routing table Topology Table—IP Destination 1 Successor Destination 1 Feasible ...
... Successor routes • Successor route is used by EIGRP to forward traffic to a destination • A successor routes may be backed up by a feasible successor route • Successor routes are stored in both the topology table and the routing table Topology Table—IP Destination 1 Successor Destination 1 Feasible ...
Brief History of the Internet(1)
... • Optimizations can be harmful if they reduce future adaptability. • In an exponential world, optimization is often an exercise in futility. • Note: “minimum” assumption does not mean “no assumption.” • TCP performance requires packet loss under a few percent. • QoS often needs support in subnets. ...
... • Optimizations can be harmful if they reduce future adaptability. • In an exponential world, optimization is often an exercise in futility. • Note: “minimum” assumption does not mean “no assumption.” • TCP performance requires packet loss under a few percent. • QoS often needs support in subnets. ...
Tuesday, March 20, 2007 (Circuits, Virtual
... Flexible bandwidth management Can use ATM QoS support for individual connections (with appropriate signaling support) ...
... Flexible bandwidth management Can use ATM QoS support for individual connections (with appropriate signaling support) ...
Case Studies - Huawei Enterprise
... S9700 switches also support In-Service Software Upgrade (ISSU) upgrades, further reducing service interruption. Additionally, the S9700 switches innovatively implement the Cluster Switch System (CSS) function through switching fabrics, AN innovation that efficiently addresses the problem of low swit ...
... S9700 switches also support In-Service Software Upgrade (ISSU) upgrades, further reducing service interruption. Additionally, the S9700 switches innovatively implement the Cluster Switch System (CSS) function through switching fabrics, AN innovation that efficiently addresses the problem of low swit ...
User Manual PowerLine AV500 Wireless N Mini Extender Starter Kit
... The Wireless N technology incorporated into the DHP-W310AV offers increased speed and range beyond standard 802.11g technology. Initial wireless setup can be accomplished quickly, thanks to a convenient setup wizard. WPA and WPA2 encryption keep your network traffic safe and secure. Ideal For Bandwi ...
... The Wireless N technology incorporated into the DHP-W310AV offers increased speed and range beyond standard 802.11g technology. Initial wireless setup can be accomplished quickly, thanks to a convenient setup wizard. WPA and WPA2 encryption keep your network traffic safe and secure. Ideal For Bandwi ...
Document
... The Internet has run out of addresses. The alternative is expensive, complex and unreliable Enabler for new services and existing services in a cheaper, simpler and more scalable manner Equal distribution of IP addresses around the world (unlike IPv4), which is especially important for large p ...
... The Internet has run out of addresses. The alternative is expensive, complex and unreliable Enabler for new services and existing services in a cheaper, simpler and more scalable manner Equal distribution of IP addresses around the world (unlike IPv4), which is especially important for large p ...
Chapter 9 - Subnetting IP Networks
... Subnetting Using the Subnet ID An IPv6 Network Space is subnetted to support hierarchical, logical design of the network ...
... Subnetting Using the Subnet ID An IPv6 Network Space is subnetted to support hierarchical, logical design of the network ...
Magnum Network Software – DX
... DX IPsec uses the Internet Key Exchange (IKE) protocol to set up security associations. This protocol runs over UDP on port 500. If IKE is to run over a firewalled interface, a specific permit rule must be defined for it in the firewall’s Inbound Connection table. This rule can be as general or spec ...
... DX IPsec uses the Internet Key Exchange (IKE) protocol to set up security associations. This protocol runs over UDP on port 500. If IKE is to run over a firewalled interface, a specific permit rule must be defined for it in the firewall’s Inbound Connection table. This rule can be as general or spec ...