Experimental Evaluation of LANMAR, a Scalable
... except in scenario 3. This is because the two selected nodes in scenario 1 or 2 are along the path from the source to the destination. In scenario 3, the two selected nodes are not on the path to the destination. Also once the landmark of the destinations group is down, the source and forwarding nod ...
... except in scenario 3. This is because the two selected nodes in scenario 1 or 2 are along the path from the source to the destination. In scenario 3, the two selected nodes are not on the path to the destination. Also once the landmark of the destinations group is down, the source and forwarding nod ...
FlexPort 80 ® 80 GHz High-Capacity Wireless Carrier Backhaul Links
... capacity while migrating technologies from circuit-based SDH/ SONET networks to packet-based IP networks. BridgeWave’s FlexPort80 provides simultaneous native SDH/SONET and native Ethernet connectivity in a single, all-outdoor solution with user transmission rates up to 1200 Mbps. With FlexPort80, n ...
... capacity while migrating technologies from circuit-based SDH/ SONET networks to packet-based IP networks. BridgeWave’s FlexPort80 provides simultaneous native SDH/SONET and native Ethernet connectivity in a single, all-outdoor solution with user transmission rates up to 1200 Mbps. With FlexPort80, n ...
Introduction
... 55.91.56.21) into 48-bit local MAC addresses (e.g., 01-1C-23-0E-1D-41). Hosts on the same network must know each other’s MAC addresses before they can send and receive packets using IP addresses. Hosts build ARP tables by sending ARP requests and replies to each other. b) Can ARP poisoning be used o ...
... 55.91.56.21) into 48-bit local MAC addresses (e.g., 01-1C-23-0E-1D-41). Hosts on the same network must know each other’s MAC addresses before they can send and receive packets using IP addresses. Hosts build ARP tables by sending ARP requests and replies to each other. b) Can ARP poisoning be used o ...
Guide to Network Defense and - e
... – TCP headers are processed at the Transport layer of OSI model – TCP portion of a packet is called TCP segment – Flags section of a TCP header are important: • You can specify them when you create packet-filtering ...
... – TCP headers are processed at the Transport layer of OSI model – TCP portion of a packet is called TCP segment – Flags section of a TCP header are important: • You can specify them when you create packet-filtering ...
The University of Queensland
... In traditional IP routing, all packets between a source and destination follow the same path through the network. This is due to the fact that forwarding decisions at each hop are based on the destination IP address in the packet. In contrast, the matching rules in flow tables of SDN switches are mu ...
... In traditional IP routing, all packets between a source and destination follow the same path through the network. This is due to the fact that forwarding decisions at each hop are based on the destination IP address in the packet. In contrast, the matching rules in flow tables of SDN switches are mu ...
Characteristics of Communication Systems
... A protocol is a set of rules which governs the transfer of data between computers. Protocols allow communication between computers and networks. Handshaking is used to establish which protocols to use. Handshaking controls the flow of data between computers protocols will determine the speed of tran ...
... A protocol is a set of rules which governs the transfer of data between computers. Protocols allow communication between computers and networks. Handshaking is used to establish which protocols to use. Handshaking controls the flow of data between computers protocols will determine the speed of tran ...
Document
... Framing: there is also framing in IP and TCP; link access; reliable delivery: there is also reliable delivery in TCP; flow control: there is also flow control in TCP; error detection: there is also error detection in IP and TCP; ...
... Framing: there is also framing in IP and TCP; link access; reliable delivery: there is also reliable delivery in TCP; flow control: there is also flow control in TCP; error detection: there is also error detection in IP and TCP; ...
KM3218251830
... antennas.[ipmc].Mobile nodes may be cellular or satellite transmission or group of laptops. Mobile nodes can move independently in any direction. Each node in manet behave like host as well as router. Each nodes forward packet to other nodes. Research in this area is mostly simulation based Random w ...
... antennas.[ipmc].Mobile nodes may be cellular or satellite transmission or group of laptops. Mobile nodes can move independently in any direction. Each node in manet behave like host as well as router. Each nodes forward packet to other nodes. Research in this area is mostly simulation based Random w ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... presents a neighbour discovery algorithm that achieves this goal. Node hears its ID during a round; it “drops out” of neighbour discovery at the end of the round. The neighbour discovery is done even when the nodes cannot detect collisions. Instead of providing a single bit of feedback, each node no ...
... presents a neighbour discovery algorithm that achieves this goal. Node hears its ID during a round; it “drops out” of neighbour discovery at the end of the round. The neighbour discovery is done even when the nodes cannot detect collisions. Instead of providing a single bit of feedback, each node no ...
ppt - Course Website Directory
... Interface cards/devices. Each interface has a different MAC/IP address. ...
... Interface cards/devices. Each interface has a different MAC/IP address. ...
Networking
... Given a packet, where do we send it? To its final destination? Somewhere else? On which interface? ...
... Given a packet, where do we send it? To its final destination? Somewhere else? On which interface? ...
Internetworking
... • if router is connected to destination network, then forward to host • if not directly connected, then forward to some router • forwarding table maps network number into next hop (router) • each host has a default router • each router maintains a forwarding table ...
... • if router is connected to destination network, then forward to host • if not directly connected, then forward to some router • forwarding table maps network number into next hop (router) • each host has a default router • each router maintains a forwarding table ...
A Security Pattern for a Virtual Private Network
... attacker could get full access to the internal network. • Because of encryption, VPN traffic is invisible to IDS monitoring. If the IDS probe is outside the VPN server, as is often the case, then the IDS cannot see the traffic within the VPN tunnel. Therefore if a hacker gains access to the VPN, he ...
... attacker could get full access to the internal network. • Because of encryption, VPN traffic is invisible to IDS monitoring. If the IDS probe is outside the VPN server, as is often the case, then the IDS cannot see the traffic within the VPN tunnel. Therefore if a hacker gains access to the VPN, he ...
Cloud-Managed and Unified Wired and Wireless Networking Launch
... HP is announcing new solutions that enhance the existing HP Unified Wired and Wireless (UWW) portfolio with a new Cloud-Managed Networking solution, next-generation wireless access points (APs), and new scalable unified wired and wireless appliances. HP is also extending its SDN leadership with futu ...
... HP is announcing new solutions that enhance the existing HP Unified Wired and Wireless (UWW) portfolio with a new Cloud-Managed Networking solution, next-generation wireless access points (APs), and new scalable unified wired and wireless appliances. HP is also extending its SDN leadership with futu ...
O A
... solution to this problem and their use revolutionized the speed of telecommunication. Optical fibers have become an unavoidable part of any high speed communication system due to its high information carrying capacity, high bandwidth and extremely low loss. The transmission performance of the optica ...
... solution to this problem and their use revolutionized the speed of telecommunication. Optical fibers have become an unavoidable part of any high speed communication system due to its high information carrying capacity, high bandwidth and extremely low loss. The transmission performance of the optica ...
INPUT DOCUMENT: Response to Report of the 6th FGNGN meeting
... allows the aggregation of multiple resources and makes the aggregated resources appear as a single resource. The virtual networks are completed isolated each other, so different virtual networks may use different protocols and packet formats. When combined with programmability in network elements, u ...
... allows the aggregation of multiple resources and makes the aggregated resources appear as a single resource. The virtual networks are completed isolated each other, so different virtual networks may use different protocols and packet formats. When combined with programmability in network elements, u ...
Lektion 1-Introduktion
... Local Area Networks (LANs) • A computer network in a limited geographical area, a single building or several close to each other buildings • LANs are privately owned and built by the companies • Generally less expensive than WAN for comparable speed • LAN technologies use multiple access channels • ...
... Local Area Networks (LANs) • A computer network in a limited geographical area, a single building or several close to each other buildings • LANs are privately owned and built by the companies • Generally less expensive than WAN for comparable speed • LAN technologies use multiple access channels • ...
Network Management
... download, statistics collection for ATM/TDM networks, automatic TFTPbased device configuration download and storage, as well as network level date/time synchronization. Network Management Layer RADview-SC/Vmux is a powerful management tool for provisioning and monitoring compressed voice services, p ...
... download, statistics collection for ATM/TDM networks, automatic TFTPbased device configuration download and storage, as well as network level date/time synchronization. Network Management Layer RADview-SC/Vmux is a powerful management tool for provisioning and monitoring compressed voice services, p ...
TAC Slides (May) - Travel Modelling Group
... objective function • Cannot reasonably assume that zone internal roads are not present (especially when applying an older zone system to a newer network) • Not much experience to draw upon in the literature ...
... objective function • Cannot reasonably assume that zone internal roads are not present (especially when applying an older zone system to a newer network) • Not much experience to draw upon in the literature ...
CH 2 Packet Filtering
... - Only way that a packet filter can determine the service that it is filtering EX might want to filter out all Telnet traffic – do so by blocking all traffic that is directed at TCP port 23 o TCP’s Three-Way Handshake Host A wants to connect to Host B 1. Host A sends a packet to Host B with the SYN ...
... - Only way that a packet filter can determine the service that it is filtering EX might want to filter out all Telnet traffic – do so by blocking all traffic that is directed at TCP port 23 o TCP’s Three-Way Handshake Host A wants to connect to Host B 1. Host A sends a packet to Host B with the SYN ...
PSAX family brochure.qxd - Convergent Communications (India)
... scheme assigns internal traffic priorities even more specialized than the ATM Forum, to differentiate voice, video, and data requirements, and deliver quality of service for each. Using the latest voice-compression technology, the voice server modules used with the PSAX 4500 deliver service provider ...
... scheme assigns internal traffic priorities even more specialized than the ATM Forum, to differentiate voice, video, and data requirements, and deliver quality of service for each. Using the latest voice-compression technology, the voice server modules used with the PSAX 4500 deliver service provider ...
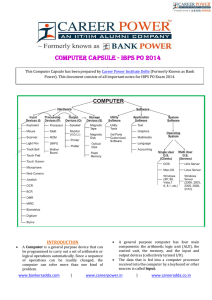
COMPUTER CAPSULE - IBPS PO 2014 . INTRODUCTION
... The set of instructions, which control the sequence of operations, are known as Program. It is a sequence of instructions, written to perform a specified task with a computer. A Software instructs the computer what to do and how to do it. It is a set of instructions that tells the computer about the ...
... The set of instructions, which control the sequence of operations, are known as Program. It is a sequence of instructions, written to perform a specified task with a computer. A Software instructs the computer what to do and how to do it. It is a set of instructions that tells the computer about the ...
Internet2 Presentation Template
... packet infrastructure. By 2006 when the current UCAID Qwest contract expires will the available technology drive us toward another architecture? Some discipline specific networks have enormous bandwidth requirements • High Energy Physics Community • Square Kilometre Array Community ...
... packet infrastructure. By 2006 when the current UCAID Qwest contract expires will the available technology drive us toward another architecture? Some discipline specific networks have enormous bandwidth requirements • High Energy Physics Community • Square Kilometre Array Community ...