Alteon Stackable Web switches 180 and ACEDirector
... and applications – assigning each session to the most available server associated with the destination VIP address specified. It monitors each session from start to finish, providing full address translation as it forwards packets between the client and server. VIP addresses can be administered in ...
... and applications – assigning each session to the most available server associated with the destination VIP address specified. It monitors each session from start to finish, providing full address translation as it forwards packets between the client and server. VIP addresses can be administered in ...
Presentation Title Here 24/28pt - Alcatel
... A new acquisition always requires very fast ROI from all departments. IT integration can be very long, but needs at least a network integration. ...
... A new acquisition always requires very fast ROI from all departments. IT integration can be very long, but needs at least a network integration. ...
Chapter 4 PowerPoint Slides
... Network of networks that use the TCP/IP protocol Contain gateways to computers that do not use TCP/IP Provides four basic functions: ...
... Network of networks that use the TCP/IP protocol Contain gateways to computers that do not use TCP/IP Provides four basic functions: ...
Group Comm
... (IETF) protocols that are suitable for Low Power Lossy Network (LLN) and standard backbone deployments, instead of defining new protocols from scratch ...
... (IETF) protocols that are suitable for Low Power Lossy Network (LLN) and standard backbone deployments, instead of defining new protocols from scratch ...
NET331_lecture10
... – is an examination of the data contained in a packet as well as the state of the connection between internal and external computers. – This information, known as the state table, is kept in a memory location called the cache. – Stateful inspection is superior to stateless inspection because it uses ...
... – is an examination of the data contained in a packet as well as the state of the connection between internal and external computers. – This information, known as the state table, is kept in a memory location called the cache. – Stateful inspection is superior to stateless inspection because it uses ...
Module 5 – Networking
... • How many bits in an IP address? • How many of these bits identify the network? • How many of these bits identify the host on a particular network? ...
... • How many bits in an IP address? • How many of these bits identify the network? • How many of these bits identify the host on a particular network? ...
Introduction
... student:x:1000:1000:Example User,,555-1212,:/home/student:/bin/bash student:$1$w/UuKtLF$otSSvXtSN/xJzUOGFElNz0:13226:0:99999:7::: CIT 470: Advanced Network and System Administration ...
... student:x:1000:1000:Example User,,555-1212,:/home/student:/bin/bash student:$1$w/UuKtLF$otSSvXtSN/xJzUOGFElNz0:13226:0:99999:7::: CIT 470: Advanced Network and System Administration ...
Routed Protocol - Faculty of Computer Science and Information
... The address is checked to see if the frame is directly addressed to the router interface, or if it is a broadcast. In either of these two cases, the frame is accepted. Otherwise, the frame is discarded The packet is then checked to see if it is actually destined for the router, or if it is to be rou ...
... The address is checked to see if the frame is directly addressed to the router interface, or if it is a broadcast. In either of these two cases, the frame is accepted. Otherwise, the frame is discarded The packet is then checked to see if it is actually destined for the router, or if it is to be rou ...
Connecting computers - Cambridge Regional College
... If no proxy server is used, what is the IP address of the default gateway? Is static IP addressing or dynamic IP addressing used? – If static IP addresses are used, what is the IP address and subnet mask? ...
... If no proxy server is used, what is the IP address of the default gateway? Is static IP addressing or dynamic IP addressing used? – If static IP addresses are used, what is the IP address and subnet mask? ...
Chapter_10_Final
... • This allows us to communicate with IPv4 and IPv6 devices at the same time. ...
... • This allows us to communicate with IPv4 and IPv6 devices at the same time. ...
Download PDF: Regione Abruzzo - ARIT
... and peaks often higher than 2,000 metres. It is a geography that shapes an area that many believe to be the heart of rustic Italy, but which today has created a digital divide. Most of the region’s 1.3 million inhabitants live in the four county capitals, along the coast or in one of only a few doze ...
... and peaks often higher than 2,000 metres. It is a geography that shapes an area that many believe to be the heart of rustic Italy, but which today has created a digital divide. Most of the region’s 1.3 million inhabitants live in the four county capitals, along the coast or in one of only a few doze ...
OSI Network Layer OSI Layer 3 Network Fundamentals – Chapter 5 ١
... Further subdividing networks into smaller networks With IPv4 hierarchical addressing, the network portion of the address for all hosts in a network is the same. To divide a network, the network portion of the address is extended to use bits from the host portion of the address. These borrowed host ...
... Further subdividing networks into smaller networks With IPv4 hierarchical addressing, the network portion of the address for all hosts in a network is the same. To divide a network, the network portion of the address is extended to use bits from the host portion of the address. These borrowed host ...
20000209-HoustonQoS-Fallis
... Conclusions • Migration to control layer • QoS is application, routing independent • Common reservation method • Common signalling method • Range of QoS supported • QoS architecture not dependant on other NW functions • Work needs to be done on how and when to use these services ...
... Conclusions • Migration to control layer • QoS is application, routing independent • Common reservation method • Common signalling method • Range of QoS supported • QoS architecture not dependant on other NW functions • Work needs to be done on how and when to use these services ...
Burst-Polling Based Dynamic Bandwidth Allocation using Adaptive
... Ethernet passive optical network (EPON), Quality of service (QoS). ...
... Ethernet passive optical network (EPON), Quality of service (QoS). ...
IP MULTICAST
... standard unicast routing table that the incoming interface is the one that is used for sending unicast packets toward S. If this is not the case, it drops the packets and sends back a “prune (S,G)” message on the incoming interface. • The router will then forward a copy of the message on all the int ...
... standard unicast routing table that the incoming interface is the one that is used for sending unicast packets toward S. If this is not the case, it drops the packets and sends back a “prune (S,G)” message on the incoming interface. • The router will then forward a copy of the message on all the int ...
Admission Control in IP Multicast over Heterogeneous Access
... – Receivers are free to join any group – Sources are free to transmit to any group Makes IP multicast-based commercial services difficult to implement ...
... – Receivers are free to join any group – Sources are free to transmit to any group Makes IP multicast-based commercial services difficult to implement ...
GARR and cultural heritage
... The performance involved three archaeological sites in Rome (Colosseum, the Baths of Diocletian, and Crypta Balbi, which were among the monuments recently interconnected) and a major research facility, the laboratories of the National Institute of Nuclear Physics (INFN) in Frascati, at about 30 km f ...
... The performance involved three archaeological sites in Rome (Colosseum, the Baths of Diocletian, and Crypta Balbi, which were among the monuments recently interconnected) and a major research facility, the laboratories of the National Institute of Nuclear Physics (INFN) in Frascati, at about 30 km f ...
Slide 1
... Yes: Apply subnet mask of the receiving interface for this network address in the routing table. No: Apply classful subnet mask for this network address in the routing table. Sending an Update: Determining whether or not to summarize route sent What is the major classful network address of t ...
... Yes: Apply subnet mask of the receiving interface for this network address in the routing table. No: Apply classful subnet mask for this network address in the routing table. Sending an Update: Determining whether or not to summarize route sent What is the major classful network address of t ...
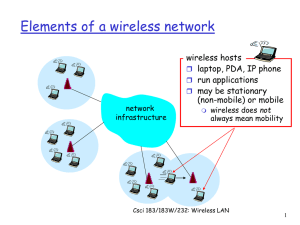
Chapter 6 slides, Computer Networking, 3rd edition
... random bits random sequence known to both sender and receiver called n-bit chipping code 802.11 defines an 11-bit chipping code ...
... random bits random sequence known to both sender and receiver called n-bit chipping code 802.11 defines an 11-bit chipping code ...
An Overview of the MEF
... frequency accuracy of ±50 ppb and ±100 ppb (pico BS) – The need for this requirement stems primarily from the need to support handover of mobiles between base stations – UMTS FDD Base Station (frequency synchronization) • The timing requirement applicable to the WCDMA FDD radio interface can be foun ...
... frequency accuracy of ±50 ppb and ±100 ppb (pico BS) – The need for this requirement stems primarily from the need to support handover of mobiles between base stations – UMTS FDD Base Station (frequency synchronization) • The timing requirement applicable to the WCDMA FDD radio interface can be foun ...
AL35218220
... minimize the overall delay in the network. The Internet today provides only a single path between any pair of hosts that fundamentally limits the throughput achievable between them. Multipath routing can be effectively used for maximum utilization of network resources. It gives the node a choice of ...
... minimize the overall delay in the network. The Internet today provides only a single path between any pair of hosts that fundamentally limits the throughput achievable between them. Multipath routing can be effectively used for maximum utilization of network resources. It gives the node a choice of ...
Routing Protocols in Mobile Ad
... an internetwork. The later concept is called as packet switching which is straight forward, and the path determination could be very complex[4]. Routing protocols use several metrics to calculate the best path for routing the packets to its destination. These metrics are a standard measurement that ...
... an internetwork. The later concept is called as packet switching which is straight forward, and the path determination could be very complex[4]. Routing protocols use several metrics to calculate the best path for routing the packets to its destination. These metrics are a standard measurement that ...
3rd Edition, Chapter 5
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...