MIS 5211.001 Week 2 Site: 1
... Forwards packets between computer networks Works to keep localized traffic inside and only passes traffic intended for targets outside the local network Boundary between “Routable” and “NonRoutable” IP addressing ...
... Forwards packets between computer networks Works to keep localized traffic inside and only passes traffic intended for targets outside the local network Boundary between “Routable” and “NonRoutable” IP addressing ...
Network Topologies - CDNIS Community Sites
... not require that a DHCP server is running on the network. Certain types of servers must have a static IP address. These servers include DHCP servers, DNS servers, WINS servers, and any server that is providing access to users who are using the Internet. ...
... not require that a DHCP server is running on the network. Certain types of servers must have a static IP address. These servers include DHCP servers, DNS servers, WINS servers, and any server that is providing access to users who are using the Internet. ...
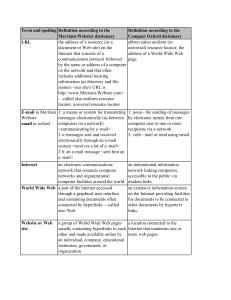
Table 9.1 Spelling and definitions.pdf
... E-mail in Merriam 1: a means or system for transmitting messages electronically (as between Webster computers on a network) email in oxford
2 a: messages sent and received
electronically through an e-mail
system
2 b: an e-mail message
... E-mail in Merriam 1: a means or system for transmitting messages electronically (as between Webster computers on a network) email in oxford
logical topology
... • A ‘driver’ for the NIC, supplied by the manufacturer. This allows the NIC hardware to be controlled by the PC an operates at the data link layer. • A ‘protocol’ such as TCP/IP, NetBeui, Ipx/Spx etc. These are components which amongst other things control how information is ‘routed’ in networks. • ...
... • A ‘driver’ for the NIC, supplied by the manufacturer. This allows the NIC hardware to be controlled by the PC an operates at the data link layer. • A ‘protocol’ such as TCP/IP, NetBeui, Ipx/Spx etc. These are components which amongst other things control how information is ‘routed’ in networks. • ...
7.6.1: Skills Integration Challenge-Data Link Layer Issues (Instructor
... You will need to configure the server, both routers, and the two PCs. You will not need to configure the switch nor do you need the IOS CLI to configure the routers. Part of the router configuration has already been done for you: all you must do is configure the static routes and the interfaces via ...
... You will need to configure the server, both routers, and the two PCs. You will not need to configure the switch nor do you need the IOS CLI to configure the routers. Part of the router configuration has already been done for you: all you must do is configure the static routes and the interfaces via ...
15-744: Computer Networking
... Why or why not keep this paper in syllabus? What issues are left open for future research? What are the important implications of the work? ...
... Why or why not keep this paper in syllabus? What issues are left open for future research? What are the important implications of the work? ...
Slide 1
... built, as well as whenever changes or additions are made to the network. • Microsoft Visio is a common tool used for network documentation, ...
... built, as well as whenever changes or additions are made to the network. • Microsoft Visio is a common tool used for network documentation, ...
2233 Booth Avenue • Marysville, CA 95901 • (530) 713
... o Support and help with any requested telecommunication needs Support the current hardware and operating system used for our Private Branch Exchange (PBX) Work with Executone on switchboard issues o Continually monitor network system for changes made (use of software such as, but not limited to, ...
... o Support and help with any requested telecommunication needs Support the current hardware and operating system used for our Private Branch Exchange (PBX) Work with Executone on switchboard issues o Continually monitor network system for changes made (use of software such as, but not limited to, ...
Project JXTA
... Sharing content cache over high speed LAN Data mirroring and striping using shared storage Deep search beyond the web Dynamic collaboration ...
... Sharing content cache over high speed LAN Data mirroring and striping using shared storage Deep search beyond the web Dynamic collaboration ...
Networks
... LANs connect computers and peripherals within a building. Users can access software, data, and peripherals. LANs require special hardware and software. ...
... LANs connect computers and peripherals within a building. Users can access software, data, and peripherals. LANs require special hardware and software. ...
IP Addressing
... the host number to indicate a subnet number. With subnetting, the network prefix and the subnet number make up an extended network prefix. The extended prefix can be expressed in terms of a subnetmask or, using CIDR notation, by adding the length of the extended subnetmask after the IP address. ...
... the host number to indicate a subnet number. With subnetting, the network prefix and the subnet number make up an extended network prefix. The extended prefix can be expressed in terms of a subnetmask or, using CIDR notation, by adding the length of the extended subnetmask after the IP address. ...
What are the collision domains?
... • The three sources of broadcasts and multicasts in IP networks are workstations, routers, and multicast applications. • Workstations broadcast an Address Resolution Protocol (ARP) request every time they need to locate a MAC address that is not in the ARP table. The ARP rate for a typical workstati ...
... • The three sources of broadcasts and multicasts in IP networks are workstations, routers, and multicast applications. • Workstations broadcast an Address Resolution Protocol (ARP) request every time they need to locate a MAC address that is not in the ARP table. The ARP rate for a typical workstati ...
Addressing - Punjab University College of Information
... G/I = 0 means unicast or individual station G/I = 1 means a (LAN) multicast address ...
... G/I = 0 means unicast or individual station G/I = 1 means a (LAN) multicast address ...
Chapter One
... receive files via TCP/IP Simple Mail Transfer Protocol (SMTP) is responsible for moving messages from one e-mail server to another, using the Internet and other TCP/IPbased networks Simple Network Management Protocol (SNMP) manages devices on a TCP/IP network ...
... receive files via TCP/IP Simple Mail Transfer Protocol (SMTP) is responsible for moving messages from one e-mail server to another, using the Internet and other TCP/IPbased networks Simple Network Management Protocol (SNMP) manages devices on a TCP/IP network ...
11/18
... send the packets one at a time to a nearby router if you are a router in the middle, when you receive a packet pass it on towards the destination as fast as you can if you are the tear off the put it in the send it back ...
... send the packets one at a time to a nearby router if you are a router in the middle, when you receive a packet pass it on towards the destination as fast as you can if you are the tear off the put it in the send it back ...
Computer Signals
... Ensuring that the systems are up and running at any given point in time, while making them easy for a user to operate. Maintaining the system’s operation with the minimum amount ...
... Ensuring that the systems are up and running at any given point in time, while making them easy for a user to operate. Maintaining the system’s operation with the minimum amount ...
Slide 1
... Presentation, and Application layers of the OSI model. Applications gain access to the network through this layer, via protocols such as the File Transfer Protocol (FTP), Trivial File Transfer Protocol (TFTP), Hypertext Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), and Dynamic Host ...
... Presentation, and Application layers of the OSI model. Applications gain access to the network through this layer, via protocols such as the File Transfer Protocol (FTP), Trivial File Transfer Protocol (TFTP), Hypertext Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), and Dynamic Host ...
Internetworking
... – Echo: ping - send ICMP ECHO_REQUEST packets to network hosts – Redirect (from router to source host) – Destination unreachable (protocol, port, or host) – TTL exceeded (so datagrams don’t cycle forever) – Checksum failed – Reassembly failed – Cannot fragment ...
... – Echo: ping - send ICMP ECHO_REQUEST packets to network hosts – Redirect (from router to source host) – Destination unreachable (protocol, port, or host) – TTL exceeded (so datagrams don’t cycle forever) – Checksum failed – Reassembly failed – Cannot fragment ...
Ağ Güvenliği - Dr. Mustafa Cem Kasapbasi
... Several opportunities to win the race If attacker loses, has to wait until TTL expires … but can try again with host2.foo.com, host3.foo.com, etc. … but what’s the point of hijacking host3.foo.com? ...
... Several opportunities to win the race If attacker loses, has to wait until TTL expires … but can try again with host2.foo.com, host3.foo.com, etc. … but what’s the point of hijacking host3.foo.com? ...
COS 420 day 18
... Replaces source address in outgoing datagram Replaces destination address in incoming datagram Also handles higher layer protocols (e.g., pseudo header For TCP or UDP) ...
... Replaces source address in outgoing datagram Replaces destination address in incoming datagram Also handles higher layer protocols (e.g., pseudo header For TCP or UDP) ...
Objectives Configure routing in Windows Server 2008 Configure
... • Can force authentication between routers when announcements are sent • Password for authentication is plain text • Can configure which incoming and outgoing routes are accepted ...
... • Can force authentication between routers when announcements are sent • Password for authentication is plain text • Can configure which incoming and outgoing routes are accepted ...
Diapositive 1
... Protocol of PPP encapsulation over IP designed by Microsoft Allow to set the virtual private networks (VPNs) over a public network. The protocol opens two channels of communication between the client and server: • a channel control for the management of the ...
... Protocol of PPP encapsulation over IP designed by Microsoft Allow to set the virtual private networks (VPNs) over a public network. The protocol opens two channels of communication between the client and server: • a channel control for the management of the ...
DeltaV Control Performance Suite
... different information. For example, through this interface you may access a network overview, the published device values, the network configuration and the parameters of a device that are configurable. ...
... different information. For example, through this interface you may access a network overview, the published device values, the network configuration and the parameters of a device that are configurable. ...
Networking
... carried between computers in the data field of Ethernet frames (MAC address) The system of high-level protocols carrying application data and the Ethernet system are independent entities that cooperate to deliver data between computers The protocol that provides that cooperation is called “ARP” ...
... carried between computers in the data field of Ethernet frames (MAC address) The system of high-level protocols carrying application data and the Ethernet system are independent entities that cooperate to deliver data between computers The protocol that provides that cooperation is called “ARP” ...
9/13/2010 Computer Network? The “nuts and bolts” view of the Internet
... ❍ “a communication medium used by millions” ...
... ❍ “a communication medium used by millions” ...