MultiNet: Connecting to Multiple IEEE 802.11 Networks Using a
... What buffering protocols should we use to ensure delivery of packets across the disjoint networks? What switching algorithms should we use to get the best performance from MultiNet? and How do we do synchronize multiple switching nodes in an ad hoc network? ...
... What buffering protocols should we use to ensure delivery of packets across the disjoint networks? What switching algorithms should we use to get the best performance from MultiNet? and How do we do synchronize multiple switching nodes in an ad hoc network? ...
CSCE 790: Computer Network Security
... inform-request allows one manager to send info to another ...
... inform-request allows one manager to send info to another ...
Dualog Connection Suite DHCP Server – User Manual
... owner, you will get an IP conflict. This is not as bad as it sounds, but the DHCP server will mark off the address as being unavailable, and not release it again until the DHCP range is filled up. Please note that if an IP conflict arises, performing the repair-operation as described in 5.1.1 will f ...
... owner, you will get an IP conflict. This is not as bad as it sounds, but the DHCP server will mark off the address as being unavailable, and not release it again until the DHCP range is filled up. Please note that if an IP conflict arises, performing the repair-operation as described in 5.1.1 will f ...
Virtualization Group
... – Need to share? Enough to hand out individually? – Hard to envision technology cost being a constraint; increasingly less important ...
... – Need to share? Enough to hand out individually? – Hard to envision technology cost being a constraint; increasingly less important ...
Systems in System Group
... without special-case checks. Relative lack of observation and control points makes it difficult to access the behavior of wide-area network. To deploy a new type of network element iBox To deploy iBox relay on A delegation and indirection mechanisms that allow both the sender and the receiver to spe ...
... without special-case checks. Relative lack of observation and control points makes it difficult to access the behavior of wide-area network. To deploy a new type of network element iBox To deploy iBox relay on A delegation and indirection mechanisms that allow both the sender and the receiver to spe ...
Data Modeling - Computer Science at Hiram College
... • Random access protocols – Always transmit at full bandwidth, if there is a conflict, retransmit the frame (after a random ...
... • Random access protocols – Always transmit at full bandwidth, if there is a conflict, retransmit the frame (after a random ...
No Slide Title
... A site switches provider without renumbering still adds one entry into global routing tables ...
... A site switches provider without renumbering still adds one entry into global routing tables ...
Chapter 19 - William Stallings, Data and Computer
... eg. avoid path to avoid transiting particular AS eg. link speed, capacity, tendency to become congested, and overall quality of operation, security eg. minimizing number of transit ASs ...
... eg. avoid path to avoid transiting particular AS eg. link speed, capacity, tendency to become congested, and overall quality of operation, security eg. minimizing number of transit ASs ...
TOPOLOGIES in COMPUTER NETWORKING
... of a cable failure. Used in WANs to ensure that all sites continue to transmit in the event of a cable failure. ...
... of a cable failure. Used in WANs to ensure that all sites continue to transmit in the event of a cable failure. ...
Good CV for a Network Engineer
... Employment History Company Role Dates Description Responsibilities ...
... Employment History Company Role Dates Description Responsibilities ...
ethics and privacy
... connected to that server and announced what files you had to share. • Every search was conducted on the dataset assembled at the central server. • Connections to download files where done between peer machines only! ...
... connected to that server and announced what files you had to share. • Every search was conducted on the dataset assembled at the central server. • Connections to download files where done between peer machines only! ...
Chapter 11 Network Fundamentals
... – Non-realtime variable bit rate (nrt-VBR) for airline reservation or financial transaction – Available bit rate (ABR) for LAN-to-LAN – Unspecified bit rate (UBR) for TCP-based traffic ...
... – Non-realtime variable bit rate (nrt-VBR) for airline reservation or financial transaction – Available bit rate (ABR) for LAN-to-LAN – Unspecified bit rate (UBR) for TCP-based traffic ...
cs516 midterm solution
... [ T ] (e) IEEE 802.2 defines the logical link control layer and provides three types of services: 1) unacknowledged connectionless service, 2) connection-mode service, and 3) acknowledged connectionless service. [ F ] (f) In CSMA/CD LANs, the amount of time that it takes to detect a collision is nev ...
... [ T ] (e) IEEE 802.2 defines the logical link control layer and provides three types of services: 1) unacknowledged connectionless service, 2) connection-mode service, and 3) acknowledged connectionless service. [ F ] (f) In CSMA/CD LANs, the amount of time that it takes to detect a collision is nev ...
home address
... IP in IP tunnels cannot traverse NAT. The Care-of address is a private address. This address is not reachable from outside the private network. Two Mobile Nodes in different private networks may happen to have the same private address as Care-of address. The solution: draft-ietf-mobileip-nat-t ...
... IP in IP tunnels cannot traverse NAT. The Care-of address is a private address. This address is not reachable from outside the private network. Two Mobile Nodes in different private networks may happen to have the same private address as Care-of address. The solution: draft-ietf-mobileip-nat-t ...
TigerStack™ II 10/100
... TigerSwitch 10/100 can be stacked up to 16 units high with the stacking kit, so that up to 386 ports can be managed under single IP address. The TigerStack II comes with features, including port or protocol based and tagged VLANs, plus support for automatic GVRP VLAN registration provides traffic se ...
... TigerSwitch 10/100 can be stacked up to 16 units high with the stacking kit, so that up to 386 ports can be managed under single IP address. The TigerStack II comes with features, including port or protocol based and tagged VLANs, plus support for automatic GVRP VLAN registration provides traffic se ...
ppt
... Using Divide and Conquer, check many in parallel. only a very small portion of addresses are monitored, so send same probe to many addresses ...
... Using Divide and Conquer, check many in parallel. only a very small portion of addresses are monitored, so send same probe to many addresses ...
TCP/IP
... timeout condition is reached or until successful delivery has been achieved. TCP can also recognize duplicate messages and will discard them appropriately. If the sending computer is transmitting too fast for the receiving computer, TCP can employ flow control mechanisms to slow data transfer. ...
... timeout condition is reached or until successful delivery has been achieved. TCP can also recognize duplicate messages and will discard them appropriately. If the sending computer is transmitting too fast for the receiving computer, TCP can employ flow control mechanisms to slow data transfer. ...
Communication Networks Overview Nodes and Links Nodes and
... company Y, you use the services of the next lower layer. Specifically, you ask your secretary to put a destination address, a return address, and a stamp onto an envelope, and to put the letter inside the envelope. The peer of the secretary in company B is the secretary in company Y. ...
... company Y, you use the services of the next lower layer. Specifically, you ask your secretary to put a destination address, a return address, and a stamp onto an envelope, and to put the letter inside the envelope. The peer of the secretary in company B is the secretary in company Y. ...
Powerpoint Slide (Office 97
... Determine goals when crafting packets Identify and use packet crafting tools ...
... Determine goals when crafting packets Identify and use packet crafting tools ...
MIS 5211.001 Week 2 Site:
... Forwards packets between computer networks Works to keep localized traffic inside and only passes traffic intended for targets outside the local network Boundary between “Routable” and “NonRoutable” IP addressing ...
... Forwards packets between computer networks Works to keep localized traffic inside and only passes traffic intended for targets outside the local network Boundary between “Routable” and “NonRoutable” IP addressing ...
Module 3 Network Packet Crafting
... Determine goals when crafting packets Identify and use packet crafting tools ...
... Determine goals when crafting packets Identify and use packet crafting tools ...
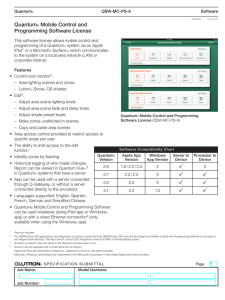
Quantum Mobile Control and Programming Software License
... Q-Admm is used to view the report in the Quantum versions prior to 3.2. Device must be equipped with a wired ethernet connection. Apple and iPad are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, and Surface are trademarks of the Microsoft Corporation in th ...
... Q-Admm is used to view the report in the Quantum versions prior to 3.2. Device must be equipped with a wired ethernet connection. Apple and iPad are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, and Surface are trademarks of the Microsoft Corporation in th ...
Intro To Networking Part B Chapter 3
... Before a network upgrade can be properly designed, an on-site technician is dispatched to: – Perform a site survey to document the existing network structure. –Document the physical layout of the premises to determine where new equipment can be installed. Review the on site survey results with t ...
... Before a network upgrade can be properly designed, an on-site technician is dispatched to: – Perform a site survey to document the existing network structure. –Document the physical layout of the premises to determine where new equipment can be installed. Review the on site survey results with t ...
Internet Protocols
... The Internet protocols are the world’s most popular open-system (nonproprietary) protocol suite because they can be used to communicate across any set of interconnected networks and are equally well suited for LAN and WAN communications. The Internet protocols consist of a suite of communication pro ...
... The Internet protocols are the world’s most popular open-system (nonproprietary) protocol suite because they can be used to communicate across any set of interconnected networks and are equally well suited for LAN and WAN communications. The Internet protocols consist of a suite of communication pro ...