RHA030 - Workbook
... • Network server applications are generally designed to be "always running", starting automatically as a system boots, and only shutting down when the system does. Generally, only the root user may manage server processes. • Network client applications are generally running only when in use, and may ...
... • Network server applications are generally designed to be "always running", starting automatically as a system boots, and only shutting down when the system does. Generally, only the root user may manage server processes. • Network client applications are generally running only when in use, and may ...
Networks presentation - DPS Indonesia
... have a frequency range of just less than that of red light. These waves are used for short range communication (approx. 5m) in a variety of wireless communications, monitoring, and control applications. Home-entertainment remote-control devices, Cordless mouse, and Intrusion detectors are some of th ...
... have a frequency range of just less than that of red light. These waves are used for short range communication (approx. 5m) in a variety of wireless communications, monitoring, and control applications. Home-entertainment remote-control devices, Cordless mouse, and Intrusion detectors are some of th ...
e3-e4 cfa core subject
... 68. Direct Broadcast Address is used by a router to send a packet to all hosts in a network. 69. If an IP address is composed of all 0s, it means This Host on this Network. 70. A host address which does not know its IP address uses the IP address 0.0.0.0 as the source address and 255.255.255.255 as ...
... 68. Direct Broadcast Address is used by a router to send a packet to all hosts in a network. 69. If an IP address is composed of all 0s, it means This Host on this Network. 70. A host address which does not know its IP address uses the IP address 0.0.0.0 as the source address and 255.255.255.255 as ...
wireless broadband router base station-g
... 1.1 AirStation 54Mbps Wireless Broadband Router Base Station (WBR-G54) Welcome to AirStation, the easy way to fast wireless networking. This manual introduces you to the high-speed AirStation 54Mbps Wireless Broadband Router Base Station and will help you connect to your broadband internet connectio ...
... 1.1 AirStation 54Mbps Wireless Broadband Router Base Station (WBR-G54) Welcome to AirStation, the easy way to fast wireless networking. This manual introduces you to the high-speed AirStation 54Mbps Wireless Broadband Router Base Station and will help you connect to your broadband internet connectio ...
CEI 128 - Magellan Configuration.pmd
... back of your EdgeWare server. The serial number begins with CE and six digits, for instance “CE2ADB10.” Note that the serial number of your server can be found under the “Host Name” column. NOTE: For information of how to obtain access and configure the EdgeWare OS, please refer to the EdgeWare conf ...
... back of your EdgeWare server. The serial number begins with CE and six digits, for instance “CE2ADB10.” Note that the serial number of your server can be found under the “Host Name” column. NOTE: For information of how to obtain access and configure the EdgeWare OS, please refer to the EdgeWare conf ...
What is the Internet? - University of Arizona
... "I just had to take the hypertext idea and connect it to the Transmission Control Protocol and domain name system ideas and—ta-da!—the World Wide Web ... Creating the web was really an act of desperation, because the situation without it was very difficult when I was working at CERN later. Most of t ...
... "I just had to take the hypertext idea and connect it to the Transmission Control Protocol and domain name system ideas and—ta-da!—the World Wide Web ... Creating the web was really an act of desperation, because the situation without it was very difficult when I was working at CERN later. Most of t ...
Slides
... –Find and provision an available address –Record it in the management system –Update DNS and other related tasks The annual cost to manage each IP address is directly correlated with organization size: –Enterprise average: $9.19 annually –SMB average: $7.12 annually –Mean: $8.10 annually Conclusio ...
... –Find and provision an available address –Record it in the management system –Update DNS and other related tasks The annual cost to manage each IP address is directly correlated with organization size: –Enterprise average: $9.19 annually –SMB average: $7.12 annually –Mean: $8.10 annually Conclusio ...
Deployment Status in Singapore
... Testbed to study the challenges of realising an all IP network QoS issues in core network and building an IP telephony system based on SIP ...
... Testbed to study the challenges of realising an all IP network QoS issues in core network and building an IP telephony system based on SIP ...
Best Practices Integrating On-Premise Datacenters with Azure IaaS
... VMs within a site in 30-seconds. Failover 1,000 VMs across sites in 3-minutes THIS hosted datacenter efficiency (now at $.46/$1, heading to $.37/$1 within 6 months) drives down the cost of a VM, and puts pressure on internal IT departments to improve their internal IT efficiencies… ...
... VMs within a site in 30-seconds. Failover 1,000 VMs across sites in 3-minutes THIS hosted datacenter efficiency (now at $.46/$1, heading to $.37/$1 within 6 months) drives down the cost of a VM, and puts pressure on internal IT departments to improve their internal IT efficiencies… ...
C: Glossary
... compressed. It can also be transmitted over a distance with little or no loss in quality. Sound (such as speech or music), still images (such as transparencies), and motion video are commonly converted into digitized form. Distance learning Instruction delivered from a distant site, possibly includi ...
... compressed. It can also be transmitted over a distance with little or no loss in quality. Sound (such as speech or music), still images (such as transparencies), and motion video are commonly converted into digitized form. Distance learning Instruction delivered from a distant site, possibly includi ...
GTS SAN Usage A UNIX SysAdmin`s View of How A SAN Works
... Most difficult to manage due to large numbers and types of servers Storage Managers may not be Server Managers Don’t trust the consumer to manage resources Trusting the fox to guard the hen house ...
... Most difficult to manage due to large numbers and types of servers Storage Managers may not be Server Managers Don’t trust the consumer to manage resources Trusting the fox to guard the hen house ...
39 Kyung Hee University Finding the Subnet Mask Address (cont`d)
... addresses in the block (including itself). It retains the netid of the block and sets the hostid to zero. (refer table 4.2) Kyung Hee University ...
... addresses in the block (including itself). It retains the netid of the block and sets the hostid to zero. (refer table 4.2) Kyung Hee University ...
ppt - Applied Crypto Group at Stanford University
... Abadi-Burrows-Manasse-Wobber, ACM ToIT ‘05 ...
... Abadi-Burrows-Manasse-Wobber, ACM ToIT ‘05 ...
3rd Edition: Chapter 2
... A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lo ...
... A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lo ...
Network Defense
... All devices on the link capture the packet and pass it to the IP layer. 10.10.10.101 is the only one to answer: a0:a0:a0:a0:a0:a0; 00:01:02:03:04:05; arp 64; arp reply 10.10.10.101 is-at a0:a0:a0:a0:a0:a0 ...
... All devices on the link capture the packet and pass it to the IP layer. 10.10.10.101 is the only one to answer: a0:a0:a0:a0:a0:a0; 00:01:02:03:04:05; arp 64; arp reply 10.10.10.101 is-at a0:a0:a0:a0:a0:a0 ...
24-ensembles
... phone numbers with my notebook computer? • How do I shuffle photos from my camera, when its memory card fills up, to my digital ...
... phone numbers with my notebook computer? • How do I shuffle photos from my camera, when its memory card fills up, to my digital ...
OptiSwitch® MR2226N-2C L2/4 Managed Switch
... ACLs restrict access to sensitive portions of the network by denying packets based on source and destination MAC addresses, IP addresses, or TCP/UDP ports. ACL lookups are done in hardware; therefore, forwarding performance is not compromised when implementing ACL-based security in the network. The ...
... ACLs restrict access to sensitive portions of the network by denying packets based on source and destination MAC addresses, IP addresses, or TCP/UDP ports. ACL lookups are done in hardware; therefore, forwarding performance is not compromised when implementing ACL-based security in the network. The ...
Introduction to Computing
... • It probably is the most important aspect of the design of a Website ...
... • It probably is the most important aspect of the design of a Website ...
Group Comm
... groups Multicast is the easy case; can use DNS to resolve FQDN in authority to multicast or unicast address Can a group be represented by a list of addresses as well? If so, perhaps this argues for a group scheme, e.g. “coapm” to signal a proxy to do fan-out task ...
... groups Multicast is the easy case; can use DNS to resolve FQDN in authority to multicast or unicast address Can a group be represented by a list of addresses as well? If so, perhaps this argues for a group scheme, e.g. “coapm” to signal a proxy to do fan-out task ...
"The Distance learning and the networking technologies".
... An Accurate Network Performance Analysis Provides Proper Network Dimensioning Decisions that ensure Distance Learning Efficiency at a minimum technical and/or economical cost. Prediction of Network Performance is a rather complicated task but can be carried out, even for complicated networks, wi ...
... An Accurate Network Performance Analysis Provides Proper Network Dimensioning Decisions that ensure Distance Learning Efficiency at a minimum technical and/or economical cost. Prediction of Network Performance is a rather complicated task but can be carried out, even for complicated networks, wi ...
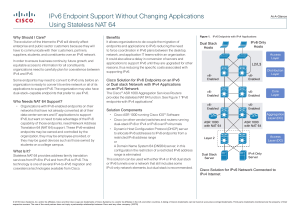
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... reasons, thus reducing the specific costs associated with supporting IPv6. ...
... reasons, thus reducing the specific costs associated with supporting IPv6. ...