Final presentation
... The cost of solving the puzzle is easy to adjust from zero to impossible (i.e. when server’s resource is getting exhausted, server should increase the difficulty level). It is not possible to precompute solutions While client is solving the puzzle, the server does not need to store the solution or o ...
... The cost of solving the puzzle is easy to adjust from zero to impossible (i.e. when server’s resource is getting exhausted, server should increase the difficulty level). It is not possible to precompute solutions While client is solving the puzzle, the server does not need to store the solution or o ...
例外(exception)とは何か
... - A network includes a set of protocols to work together, called protocol suite/family - Each protocol in a protocol suite solves part of communication problem Need for Protocols - Hardware is low level and can’t be directly interacted with computer - Need mechanisms to distinguish among * multiple ...
... - A network includes a set of protocols to work together, called protocol suite/family - Each protocol in a protocol suite solves part of communication problem Need for Protocols - Hardware is low level and can’t be directly interacted with computer - Need mechanisms to distinguish among * multiple ...
Globus Project Future Directions
... The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format message block permits building relatively simple switching mechanisms using an adaptive store-and- ...
... The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format message block permits building relatively simple switching mechanisms using an adaptive store-and- ...
Basics of Networking
... Input / Output port used for transmitting data over a network In Unix, a socket is actually a file descriptor! (called a special file) It's one of those virtualization things ...
... Input / Output port used for transmitting data over a network In Unix, a socket is actually a file descriptor! (called a special file) It's one of those virtualization things ...
Types of Computer Networks
... facilities for other computers on the network and clients are computers that receive or use the facilities provided by the server. Server in client-server type of network called a Dedicated Server as pure acts as facility provider for workstations and servers can not serve as workstation. ...
... facilities for other computers on the network and clients are computers that receive or use the facilities provided by the server. Server in client-server type of network called a Dedicated Server as pure acts as facility provider for workstations and servers can not serve as workstation. ...
[2017-04-05] Offering New 200-125 Exam PDF And 200
... What are three parts of an IPv6 global unicast address? (Choose three.) A. an interface ID that is used to identify the local host on the network B. an interface ID that is used to identify the local network for a particular host. C. a subnet ID that is used to identify networks inside of the local ...
... What are three parts of an IPv6 global unicast address? (Choose three.) A. an interface ID that is used to identify the local host on the network B. an interface ID that is used to identify the local network for a particular host. C. a subnet ID that is used to identify networks inside of the local ...
Part I: Introduction
... m change of implementation of layer’s service transparent to rest of system m e.g., change in gate procedure doesn’t affect rest of system r layering considered harmful? r ...
... m change of implementation of layer’s service transparent to rest of system m e.g., change in gate procedure doesn’t affect rest of system r layering considered harmful? r ...
Networking Terms Glossary - Beijer Electronics, Inc.
... The data link layer is concerned with physical addressing, network topology, line discipline, error notification, ordered delivery of frames, and flow control. The IEEE has divided this layer into two sublayers: the MAC sublayer and the LLC sublayer. DCE (Data Circuit-Terminating Equipment) – conver ...
... The data link layer is concerned with physical addressing, network topology, line discipline, error notification, ordered delivery of frames, and flow control. The IEEE has divided this layer into two sublayers: the MAC sublayer and the LLC sublayer. DCE (Data Circuit-Terminating Equipment) – conver ...
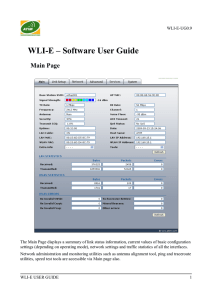
WLI-E – Software User Guide
... mode. The represented value coincides with the graphical bar. Use antenna alignment tool to adjust the device antenna to get better link with the wireless device. The antenna of the wireless client has to be adjusted to get the maximum signal strength. Signal Strength is measured in dBm (the Decibel ...
... mode. The represented value coincides with the graphical bar. Use antenna alignment tool to adjust the device antenna to get better link with the wireless device. The antenna of the wireless client has to be adjusted to get the maximum signal strength. Signal Strength is measured in dBm (the Decibel ...
3rd Edition: Chapter 4 - Communications Systems Center (CSC)
... run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
... run routing algorithms/protocol (RIP, OSPF, BGP) forwarding datagrams from incoming to outgoing link ...
$doc.title
... H1 and H2 have established a TCP connection and data packet 1, 2, 3, and 4 are flowing between the two machines as part of that connection. We have partially filled in the headers for packet ...
... H1 and H2 have established a TCP connection and data packet 1, 2, 3, and 4 are flowing between the two machines as part of that connection. We have partially filled in the headers for packet ...
Top-Down Network Design
... run on networked PCs in the security policy • Require personal firewalls and antivirus software on networked PCs – Implement written procedures that specify how the software is installed and kept current ...
... run on networked PCs in the security policy • Require personal firewalls and antivirus software on networked PCs – Implement written procedures that specify how the software is installed and kept current ...
Network Connectivity_PPT_ch09
... • Users log on to the network with a single set of credentials maintained by one or more servers running a server OS • In most cases, servers are dedicated to running network services and should not be used to run user applications ...
... • Users log on to the network with a single set of credentials maintained by one or more servers running a server OS • In most cases, servers are dedicated to running network services and should not be used to run user applications ...
H5 Appliances
... network operations engineers. It is downloaded from the H5 Appliance Web interface and run on any workstation using WebStart standard. H5-Dock loads data in real-time from the appliance network application flow database and dynamically displays the node and metrics information on pre defined and cus ...
... network operations engineers. It is downloaded from the H5 Appliance Web interface and run on any workstation using WebStart standard. H5-Dock loads data in real-time from the appliance network application flow database and dynamically displays the node and metrics information on pre defined and cus ...
Start a wireless network with up to 4X the range and 12X
... double-speed mode for Wireless-N devices, while still connecting to other wireless devices at their respective fastest speeds. In congested areas, the “good neighbor” mode ensures that the Router checks for other wireless devices in the area before gobbling up the radio band. To help protect your da ...
... double-speed mode for Wireless-N devices, while still connecting to other wireless devices at their respective fastest speeds. In congested areas, the “good neighbor” mode ensures that the Router checks for other wireless devices in the area before gobbling up the radio band. To help protect your da ...
ITNW 1358 - Network+
... 1. Turn OFF your mobile phones or, at a minimum, put them on vibrate mode! 2. Do not use the Internet during lectures or lab times unless specifically requested to locate some information. 3. Do not play games (computer or otherwise) during lecture or lab times. 4. Students may not do their class wo ...
... 1. Turn OFF your mobile phones or, at a minimum, put them on vibrate mode! 2. Do not use the Internet during lectures or lab times unless specifically requested to locate some information. 3. Do not play games (computer or otherwise) during lecture or lab times. 4. Students may not do their class wo ...
Good Network Design
... Distributed Data Interface (FDDI) One computer failing can bring down single-ring network unless it has smart hub that automatically removes failed computer from ring When one ring fails, dual ring network uses secondary ring and continues to work ...
... Distributed Data Interface (FDDI) One computer failing can bring down single-ring network unless it has smart hub that automatically removes failed computer from ring When one ring fails, dual ring network uses secondary ring and continues to work ...
ppt
... of the link and the time the packet is assigned to an outgoing link queue for transmission. 2. The queueing delay [QD] between the time the packet is assigned to a queue for transmission and the time it starts being transmitted. During this time, the packet waits while other packets in the transmiss ...
... of the link and the time the packet is assigned to an outgoing link queue for transmission. 2. The queueing delay [QD] between the time the packet is assigned to a queue for transmission and the time it starts being transmitted. During this time, the packet waits while other packets in the transmiss ...
Applying Operating System Principles to SDN Controller
... promises to ease many of the network management headaches that have been plaguing network operators for years [12, 14]. Software-defined networking uses a logically centralized control plane to manage a collection of packet processing and forwarding nodes in the data plane. It has been proposed that ...
... promises to ease many of the network management headaches that have been plaguing network operators for years [12, 14]. Software-defined networking uses a logically centralized control plane to manage a collection of packet processing and forwarding nodes in the data plane. It has been proposed that ...
arubaos 6.5 - Aruba Networks
... spend their time online. This enables IT administrators to reduce or eliminate inappropriate or malicious web traffic from enterprise networks. WebCC gives IT administrators critical insight into the risks of malware, phishing, and other security problems associated with Internet usage, and provides ...
... spend their time online. This enables IT administrators to reduce or eliminate inappropriate or malicious web traffic from enterprise networks. WebCC gives IT administrators critical insight into the risks of malware, phishing, and other security problems associated with Internet usage, and provides ...
bYTEBoss CHEBROLU_kameswari_poster
... multiple interfaces as Multi-Access Services. In this work, we develop a network layer architecture that supports multiple communication paths. We also implement most of the functional components that make up our architecture as proof of concept for the different services. We experiment with differe ...
... multiple interfaces as Multi-Access Services. In this work, we develop a network layer architecture that supports multiple communication paths. We also implement most of the functional components that make up our architecture as proof of concept for the different services. We experiment with differe ...
routing - ece.virginia.edu
... • Each switch controller then executes a shortest-path algorithm, such as Dijkstra's algorithm, to compute the shortest paths from its switch to all other switches • Each switch controller then updates a forwarding table, which shows the next-hop and/or output port for each destination address ...
... • Each switch controller then executes a shortest-path algorithm, such as Dijkstra's algorithm, to compute the shortest paths from its switch to all other switches • Each switch controller then updates a forwarding table, which shows the next-hop and/or output port for each destination address ...
IPSO-6LoWPAN - University of California, Berkeley
... Version is always 6 Traffic Class and Flow Label are zero Payload Length always derived from L2 header Next Header is UDP, TCP, or ICMPv6 Source and Destination Addrs are link-local and derived from L2 addrs ...
... Version is always 6 Traffic Class and Flow Label are zero Payload Length always derived from L2 header Next Header is UDP, TCP, or ICMPv6 Source and Destination Addrs are link-local and derived from L2 addrs ...
Things we didn`t get to talk about
... NAT: consistent mapping to internal address Load balancer: map to one of several internal addresses – May be grouped by original destination address and/or port – Connection affinity, source affinity (easier to manage sessions & stateful behavior ...
... NAT: consistent mapping to internal address Load balancer: map to one of several internal addresses – May be grouped by original destination address and/or port – Connection affinity, source affinity (easier to manage sessions & stateful behavior ...




![[2017-04-05] Offering New 200-125 Exam PDF And 200](http://s1.studyres.com/store/data/009792650_1-114d830b95438c7b9512a44704f59a08-300x300.png)