ITE PC v4.0 Chapter 1
... The hub will flood it out all ports except for the incoming port. Hub is a layer 1 device. A hub does NOT look at layer 2 addresses, so it is fast in transmitting data. Disadvantage with hubs: A hub or series of hubs is a single collision domain. A collision will occur if any two or more devices tra ...
... The hub will flood it out all ports except for the incoming port. Hub is a layer 1 device. A hub does NOT look at layer 2 addresses, so it is fast in transmitting data. Disadvantage with hubs: A hub or series of hubs is a single collision domain. A collision will occur if any two or more devices tra ...
- Aditya College of Engineering
... Most companies have a more number of computers, and each provided for workers and use them to design products, develop products, marketing their products and to maintain database etc. Resource sharing: To make all equipment (physical resources like scanners and printers), and especially data (re ...
... Most companies have a more number of computers, and each provided for workers and use them to design products, develop products, marketing their products and to maintain database etc. Resource sharing: To make all equipment (physical resources like scanners and printers), and especially data (re ...
Routing II: Protocols - ECSE - Rensselaer Polytechnic Institute
... The pt-mpt subnet model violates the IP subnet model assumption that nodes on the same subnet should be able to directly communicate with each other A network-LSA is generated by any random router on the broadcast LAN subnet. An NBMA subnet allows cheap broadcast capability. The NBMA ...
... The pt-mpt subnet model violates the IP subnet model assumption that nodes on the same subnet should be able to directly communicate with each other A network-LSA is generated by any random router on the broadcast LAN subnet. An NBMA subnet allows cheap broadcast capability. The NBMA ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... In the past few years, fixed and mobile networks had a tremendous growth in voice and data processing in good part to the increasing popularity of the Internet. Consequently new data centric applications are emerging and are reaching the general public. At the same time the market is witnessing a re ...
... In the past few years, fixed and mobile networks had a tremendous growth in voice and data processing in good part to the increasing popularity of the Internet. Consequently new data centric applications are emerging and are reaching the general public. At the same time the market is witnessing a re ...
Network Technology and the Internet
... Most are faster downstream than upstream Computer Concepts, 6th Edition, Enhanced -- Illustrated ...
... Most are faster downstream than upstream Computer Concepts, 6th Edition, Enhanced -- Illustrated ...
DATA ALCOTT SYSTEM, www.finalsemprojects.com 09600095046
... deployment in practice. Besides the well-studied pollution attacks, there is another severe threat, that of wormhole attacks, which undermines the performance gain of network coding. Since the underlying characteristics of network coding systems are distinctly different from traditional wireless net ...
... deployment in practice. Besides the well-studied pollution attacks, there is another severe threat, that of wormhole attacks, which undermines the performance gain of network coding. Since the underlying characteristics of network coding systems are distinctly different from traditional wireless net ...
Core of Multicast VPNs
... A generic MVPN service delivered by service providers or large enterprises should be able to cater to a large number of different applications such as video distribution, resource discovery and advertisement, software and file distribution, finance, surveillance, and video conferencing, among others ...
... A generic MVPN service delivered by service providers or large enterprises should be able to cater to a large number of different applications such as video distribution, resource discovery and advertisement, software and file distribution, finance, surveillance, and video conferencing, among others ...
Download PDF
... The added mechanisms ensure business continuity for data—as well as Voice-over-IP. By maximizing uptime for all traffic types, SmartNode delivers reliable unified communications for a high-quality user experience. “We’ve wiped out the FUD* factor for Voice-over-IP,” said Ramon Felder, President of P ...
... The added mechanisms ensure business continuity for data—as well as Voice-over-IP. By maximizing uptime for all traffic types, SmartNode delivers reliable unified communications for a high-quality user experience. “We’ve wiped out the FUD* factor for Voice-over-IP,” said Ramon Felder, President of P ...
04_IPv4_routing
... Default route matches every packet, therefore its to be tested last Local delivery takes place in every case ...
... Default route matches every packet, therefore its to be tested last Local delivery takes place in every case ...
Chapter 6 PowerPoint - Lansing School District
... manufacturer or vendor and thus comprise the Organizational Unique Identifier (OUI). The last six hexadecimal digits comprise the interface serial number, or another value administered by the specific vendor: ...
... manufacturer or vendor and thus comprise the Organizational Unique Identifier (OUI). The last six hexadecimal digits comprise the interface serial number, or another value administered by the specific vendor: ...
Network Topology
... transmission. If abnormally high signal levels are heard, which is a collision detection, then the node ceases transmission. ...
... transmission. If abnormally high signal levels are heard, which is a collision detection, then the node ceases transmission. ...
Networking
... Information will only be passed to the centralized network management system if at the request by the central manager or certain predefined error conditions occur on a subnet. See Figure 15-19. SNMP2 works transparently with AppleTalk, IPX, and OSI transport protocols. SNMP2 allows not just monitori ...
... Information will only be passed to the centralized network management system if at the request by the central manager or certain predefined error conditions occur on a subnet. See Figure 15-19. SNMP2 works transparently with AppleTalk, IPX, and OSI transport protocols. SNMP2 allows not just monitori ...
Routing Biomedical Data Between Applications Through Ad Hoc
... The dynamic and self-organizing nature of ad hoc networks makes them particular useful in situations where rapid network deployments are required or it is prohibitively costly to deploy and manage network infrastructure. [6] B. Applications of ad hoc wireless networks As a first approximation, we co ...
... The dynamic and self-organizing nature of ad hoc networks makes them particular useful in situations where rapid network deployments are required or it is prohibitively costly to deploy and manage network infrastructure. [6] B. Applications of ad hoc wireless networks As a first approximation, we co ...
RSUS - Unit 4
... Distance Vector routing algorithm). AODV is an “on-demand” (or reactive) routing protocol because it creates (discovers) routes only when required by the source node. For discovering routes to destinations it uses route requests (RREQ) and replies (RREP) messages that gather the accumulated cost ...
... Distance Vector routing algorithm). AODV is an “on-demand” (or reactive) routing protocol because it creates (discovers) routes only when required by the source node. For discovering routes to destinations it uses route requests (RREQ) and replies (RREP) messages that gather the accumulated cost ...
lesson1 - USF Computer Science Department
... Switch (selectively connects nearby NICs) Bridge (connects multiple network segments) Router (intelligently forwards network packets) ...
... Switch (selectively connects nearby NICs) Bridge (connects multiple network segments) Router (intelligently forwards network packets) ...
Networking-101026
... 6. A wireless network will never be connected such as to allow connection to the Internet while using wireless networking for printer sharing. 7. High power antennae and/or other signal boosters will not be used. 8. File sharing will be turned off. ...
... 6. A wireless network will never be connected such as to allow connection to the Internet while using wireless networking for printer sharing. 7. High power antennae and/or other signal boosters will not be used. 8. File sharing will be turned off. ...
slides - network systems lab @ sfu
... Principles of network applications and protocols; Sample applications: HTTP, DNS; Socket ...
... Principles of network applications and protocols; Sample applications: HTTP, DNS; Socket ...
Differentiated Services
... – Windows 2000 has support for Integrated Services QoS – Router vendors now support Integrated Services for enterprise networks (RSVP signalling and local queue management) – Router vendors developing Differentiated Services support for service provider networks – MPLS-based QoS characteristics are ...
... – Windows 2000 has support for Integrated Services QoS – Router vendors now support Integrated Services for enterprise networks (RSVP signalling and local queue management) – Router vendors developing Differentiated Services support for service provider networks – MPLS-based QoS characteristics are ...
Compliance Rules for WMDRM10 for Network Devices Receiver
... “Cryptographically Random” means unpredictable, in that no polynomialtime algorithm, given any sequence of bits, can guess the succeeding K bits with probability greater than ½^K + 1/P(K) for any (positive) polynomial P and sufficiently large K. ...
... “Cryptographically Random” means unpredictable, in that no polynomialtime algorithm, given any sequence of bits, can guess the succeeding K bits with probability greater than ½^K + 1/P(K) for any (positive) polynomial P and sufficiently large K. ...
coverage
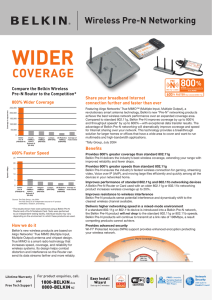
... Featuring Airgo Networks’ True MIMO™ (Multiple Input, Multiple Output), a revolutionary smart antenna technology, Belkin’s new “Pre-N” networking products achieve the best wireless network performance over an expanded coverage area. Compared to standard 802.11g, Belkin Pre-N improves coverage by up ...
... Featuring Airgo Networks’ True MIMO™ (Multiple Input, Multiple Output), a revolutionary smart antenna technology, Belkin’s new “Pre-N” networking products achieve the best wireless network performance over an expanded coverage area. Compared to standard 802.11g, Belkin Pre-N improves coverage by up ...
Slide 1
... About the Project • WIBRO stands for Wireless Broadband; it is a Korean Mobile WiMax Technology which provide superior broadband services for data, voice , video • The network consists of a core fibre-optic transmission network , wibro radio equipments, antennas and masts installed at various locati ...
... About the Project • WIBRO stands for Wireless Broadband; it is a Korean Mobile WiMax Technology which provide superior broadband services for data, voice , video • The network consists of a core fibre-optic transmission network , wibro radio equipments, antennas and masts installed at various locati ...