Configuring LNet Routers for File Systems based on Intel
... The hop parameter specifies the number of hops to the destination. When a node forwards traffic, the route with the least number of hops is used. If multiple routes to the same destination network have the same number of hops, the traffic is distributed between these routes in a round-robin fashion. ...
... The hop parameter specifies the number of hops to the destination. When a node forwards traffic, the route with the least number of hops is used. If multiple routes to the same destination network have the same number of hops, the traffic is distributed between these routes in a round-robin fashion. ...
Link Layer
... Random Access Protocols r When node has packet to send m transmit at full channel data rate R. m no a priori coordination among nodes r two or more transmitting nodes ➜ “collision”, r random access MAC protocol specifies: m how to detect collisions m how to recover from collisions (e.g., via delaye ...
... Random Access Protocols r When node has packet to send m transmit at full channel data rate R. m no a priori coordination among nodes r two or more transmitting nodes ➜ “collision”, r random access MAC protocol specifies: m how to detect collisions m how to recover from collisions (e.g., via delaye ...
Cloud Management Software/Platforms
... (specifically, which compute server host it should run on). The queue provides a central hub for passing messages between daemons. This is usually implemented with RabbitMQ today, but could be any AMQP message queue (such as Apache Qpid). New to the Folsom release is support for Zero MQ. The SQL dat ...
... (specifically, which compute server host it should run on). The queue provides a central hub for passing messages between daemons. This is usually implemented with RabbitMQ today, but could be any AMQP message queue (such as Apache Qpid). New to the Folsom release is support for Zero MQ. The SQL dat ...
Chapter 7
... problem can require a count to infinity. • To avoid this prolonged problem, distance vector protocols define infinity as a specific maximum number. • This number refers to a routing metric which may simply be the hop count. • When the metric value exceeds the maximum value, and as each router receiv ...
... problem can require a count to infinity. • To avoid this prolonged problem, distance vector protocols define infinity as a specific maximum number. • This number refers to a routing metric which may simply be the hop count. • When the metric value exceeds the maximum value, and as each router receiv ...
module10b
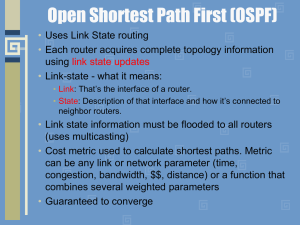
... • Loading state – one neighbor start by sending LSRs (Link State Requests) for every network it doesn't know about. The other neighbor replies with the LSUs (Link State Updates) which contain information about requested links. After all the requested information has been received, the other neighbor ...
... • Loading state – one neighbor start by sending LSRs (Link State Requests) for every network it doesn't know about. The other neighbor replies with the LSUs (Link State Updates) which contain information about requested links. After all the requested information has been received, the other neighbor ...
- Kyocera Document Solutions
... • Microsoft, Windows, Windows NT and Internet Explorer are registered trademarks of Microsoft Corporation of America and other countries. • Windows Me, Windows Server and Windows XP is a trademark of Microsoft Corporation. • Ethernet is a registered trademark of Xerox Corporation. • IBM and IBM PC/A ...
... • Microsoft, Windows, Windows NT and Internet Explorer are registered trademarks of Microsoft Corporation of America and other countries. • Windows Me, Windows Server and Windows XP is a trademark of Microsoft Corporation. • Ethernet is a registered trademark of Xerox Corporation. • IBM and IBM PC/A ...
Ch. 13 - PPP
... (MTU), compression of certain PPP fields, and the linkauthentication protocol. If a configuration option is not included in an LCP packet, the default value for that configuration option is assumed (I.e. no authentication). Before any network layer packets can be exchanged, LCP must first open the c ...
... (MTU), compression of certain PPP fields, and the linkauthentication protocol. If a configuration option is not included in an LCP packet, the default value for that configuration option is assumed (I.e. no authentication). Before any network layer packets can be exchanged, LCP must first open the c ...
Cisco ASR 5500 System Administration Guide Version 15.0
... Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner ...
... Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner ...
A Software Development Kit to exploit RINA
... Unifies networking and distributed computing: the network is a distributed application that provides IPC • 3 There is a single type of layer with programmable functions, that repeats as many times as needed by the network designers • 4 All layers provide the same service: communication (flows) bet ...
... Unifies networking and distributed computing: the network is a distributed application that provides IPC • 3 There is a single type of layer with programmable functions, that repeats as many times as needed by the network designers • 4 All layers provide the same service: communication (flows) bet ...
Chicago SCTE Event - May 2009
... Subscriber equipment which provides interface for call signaling and media transport between telephone and networks elements. E-MTA - Embedded MTA with a DOCSIS 1.1/2.0 Cable Modem MAC and PHY. Also called MTA, CM/MTA or DPT “Digital Phone Terminal” S-MTA - Standalone MTA with a LAN interface to cab ...
... Subscriber equipment which provides interface for call signaling and media transport between telephone and networks elements. E-MTA - Embedded MTA with a DOCSIS 1.1/2.0 Cable Modem MAC and PHY. Also called MTA, CM/MTA or DPT “Digital Phone Terminal” S-MTA - Standalone MTA with a LAN interface to cab ...
Chapter8 (Internet Protocol)
... list up to 9 router IP addresses since the max. size of the header is 60 bytes (Base header : 20 bytes) pointer field ...
... list up to 9 router IP addresses since the max. size of the header is 60 bytes (Base header : 20 bytes) pointer field ...
Contents - Heliodyne
... The Delta T Pro communicates with the Heliodyne Monitoring Server at 67.221.235.20, in St. Louis MO, using outgoing and incoming communication through port 9999. Some network security settings will not allow communication through port 9999 or communications to the IP address 67.221.235.20. In this c ...
... The Delta T Pro communicates with the Heliodyne Monitoring Server at 67.221.235.20, in St. Louis MO, using outgoing and incoming communication through port 9999. Some network security settings will not allow communication through port 9999 or communications to the IP address 67.221.235.20. In this c ...
Pi: A Practical Incentive Protocol for Delay Tolerant
... vehicles to communicate with each other based on the 802.11p protocol [2]. Note that the 802.11p physical layer offers different bitrates, ranging from 3 to 27 Mbps, from which OBU devices can choose [26]. Therefore, when two vehicles are within the transmission range, e.g., 300 meters, they can exc ...
... vehicles to communicate with each other based on the 802.11p protocol [2]. Note that the 802.11p physical layer offers different bitrates, ranging from 3 to 27 Mbps, from which OBU devices can choose [26]. Therefore, when two vehicles are within the transmission range, e.g., 300 meters, they can exc ...
DVTel EA-201 Encoder User Manual
... locally (not through the network and change it using the Unified Configurator. If necessary, configure the LAN/WAN to support the EA-201 IP address. Note: If you plan to use an Administrative user name and password on the unit, you can use it only for Telnet and Web server access. You do not need th ...
... locally (not through the network and change it using the Unified Configurator. If necessary, configure the LAN/WAN to support the EA-201 IP address. Note: If you plan to use an Administrative user name and password on the unit, you can use it only for Telnet and Web server access. You do not need th ...
A Dynamic Bulk Provisioning Framework for Concurrent
... the communication between ingress nodes and PCE. In this case, the ingress nodes do not need to have a working path computation client (PCC) module. A different PCE-based architecture is considered in [8] where each ingress node runs a PCC module for direct interaction with the PCE, mainly for path ...
... the communication between ingress nodes and PCE. In this case, the ingress nodes do not need to have a working path computation client (PCC) module. A different PCE-based architecture is considered in [8] where each ingress node runs a PCC module for direct interaction with the PCE, mainly for path ...
“Computers in Communication” by Gordon Brebner
... resources that are physically located in all parts of the world. From the point of view of most users, the mechanisms by which computers communicate are best kept hidden. However, without these mechanisms, no sharing of resources could happen. This book aims to reveal the basic principles of compute ...
... resources that are physically located in all parts of the world. From the point of view of most users, the mechanisms by which computers communicate are best kept hidden. However, without these mechanisms, no sharing of resources could happen. This book aims to reveal the basic principles of compute ...
multinet_admin_guide.. - PointSecure Development Web Server
... exempt from the restrictions specified in this clause. 8. If the version of a covered source file as you received it, when compiled, would normally produce executable code that would print a copyright message followed by a message referring to an ISC web page or other ISC documentation, you may not ...
... exempt from the restrictions specified in this clause. 8. If the version of a covered source file as you received it, when compiled, would normally produce executable code that would print a copyright message followed by a message referring to an ISC web page or other ISC documentation, you may not ...
MCT+Design+Options+and+Best+Practices+Guide+for+NetIron+
... of routed multicast traffic in order to prevents black-hole from uplink failure. • The IP interface can be either configured on ICL or on an extra link ...
... of routed multicast traffic in order to prevents black-hole from uplink failure. • The IP interface can be either configured on ICL or on an extra link ...
PHysical laYer protocol
... minimizing the chances of collisions. • Divides traffic into segments and filters traffic based on MAC address. • Often pass frames b/w networks operating under different Layer 2 protocols. ...
... minimizing the chances of collisions. • Divides traffic into segments and filters traffic based on MAC address. • Often pass frames b/w networks operating under different Layer 2 protocols. ...
MM2211 Wireless Broadband Gateway User`s Guide
... The device has met the FCC 15.247 requirement. In order to comply with the FCC RF exposure requirement, the user must keep 20cm away from the antenna. This device has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are ...
... The device has met the FCC 15.247 requirement. In order to comply with the FCC RF exposure requirement, the user must keep 20cm away from the antenna. This device has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are ...
An Experimenter`s Guide to OpenFlow
... Moved a VM from Stanford to Japan without changing its IP. VM hosted a video game server with active network connections. ...
... Moved a VM from Stanford to Japan without changing its IP. VM hosted a video game server with active network connections. ...
ES 203 178 - V1.1.1 - Functional architecture to support European
... Commission (EC) mandate M/493 [i.4] on emergency caller location determination and transport, in particular for the case where the VoIP service provider and one or several network operators - all serving the customer in the establishment of an emergency call - are independent enterprises needing to ...
... Commission (EC) mandate M/493 [i.4] on emergency caller location determination and transport, in particular for the case where the VoIP service provider and one or several network operators - all serving the customer in the establishment of an emergency call - are independent enterprises needing to ...
IBM BladeCenter iSCSI SAN Solution
... 1.2 Why iSCSI versus Fibre Channel The iSCSI protocol is a transport for SCSI over TCP/IP. Until recently, standard IP protocol infrastructure (for example, Ethernet) could not provide the necessary high bandwidth and low-latency needed for storage access. Special communications infrastructure, main ...
... 1.2 Why iSCSI versus Fibre Channel The iSCSI protocol is a transport for SCSI over TCP/IP. Until recently, standard IP protocol infrastructure (for example, Ethernet) could not provide the necessary high bandwidth and low-latency needed for storage access. Special communications infrastructure, main ...
CoreBuilder 3500 Implementation Guide
... adaptation) without written permission from 3Com Corporation. 3Com Corporation reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of 3Com Corporation to provide notification of such revision or change. 3Com Corporation prov ...
... adaptation) without written permission from 3Com Corporation. 3Com Corporation reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of 3Com Corporation to provide notification of such revision or change. 3Com Corporation prov ...