Evolution
... • OTNs are WDM systems providing transport services via light paths.Light paths have bandwidths up to several gigabits per second. • An OTN is made up of WXCs, plus a management system for setup and teardown of light paths. • Flexible because of most of the optical components are transparent to sign ...
... • OTNs are WDM systems providing transport services via light paths.Light paths have bandwidths up to several gigabits per second. • An OTN is made up of WXCs, plus a management system for setup and teardown of light paths. • Flexible because of most of the optical components are transparent to sign ...
IPv6 Multicasting
... while specifications of IPv6 require that all IPv6 nodes support multicasting. IPv6 explicitly limits the scope of a multicast address by using a fixed address field, whereas the scope was specified using TTL (Time to Live) of a multicast packet in IPv4. ...
... while specifications of IPv6 require that all IPv6 nodes support multicasting. IPv6 explicitly limits the scope of a multicast address by using a fixed address field, whereas the scope was specified using TTL (Time to Live) of a multicast packet in IPv4. ...
Lecture3-4-Jan13-15-04
... In-situ re-tasking gives researchers the ability to refocus their observations based on the analysis of the initial results – initially, absolute temperature readings are desired, after a while, only significant temperature changes exceeding a threshold may become more useful ...
... In-situ re-tasking gives researchers the ability to refocus their observations based on the analysis of the initial results – initially, absolute temperature readings are desired, after a while, only significant temperature changes exceeding a threshold may become more useful ...
Detecting Wireless LAN MAC Address Spoofing Joshua Wright
... Obfuscating network presence: An attacker might choose to change their MAC address in an attempt to evade network intrusion detection systems (NIDS). A common example is an attacker executing a brute- force attack script with a random MAC address for each successive connection attempt. Such an attac ...
... Obfuscating network presence: An attacker might choose to change their MAC address in an attempt to evade network intrusion detection systems (NIDS). A common example is an attacker executing a brute- force attack script with a random MAC address for each successive connection attempt. Such an attac ...
Chapter 7 - Communications Systems Center (CSC)
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking 7-10 ...
... how does callee advertise its IP address, port number, encoding algorithms? 7: Multimedia Networking 7-10 ...
ICMP and TCP - La Salle University
... Address Mask Request/Reply We discussed diskless workstation which do not know their IP address when they boot and use RARP to determine it. There is an ICMP packet used if a host does not know its subnet mask. ...
... Address Mask Request/Reply We discussed diskless workstation which do not know their IP address when they boot and use RARP to determine it. There is an ICMP packet used if a host does not know its subnet mask. ...
Net Neutrality: A must in a free society
... Mahmoud Ahmadi Nejad was re-elected in what seemed to be a rigged vote. The public of Iran rushed to the Internet posting pictures and videos from their phones from the protests. This was regarded as one of the first time a major protest was displayed in such a way. Thousands of people in Iran poste ...
... Mahmoud Ahmadi Nejad was re-elected in what seemed to be a rigged vote. The public of Iran rushed to the Internet posting pictures and videos from their phones from the protests. This was regarded as one of the first time a major protest was displayed in such a way. Thousands of people in Iran poste ...
A Predictive QoS Routing Scheme for Broadband Low Earth Orbit
... predictability of the LEO satellite topology. The LEO satellite topology at an arbitrary instant can be determined from the information on the connectivity of the constellation, and the satellite velocities. The users in the footprint of each satellite at any particular instant can also be determine ...
... predictability of the LEO satellite topology. The LEO satellite topology at an arbitrary instant can be determined from the information on the connectivity of the constellation, and the satellite velocities. The users in the footprint of each satellite at any particular instant can also be determine ...
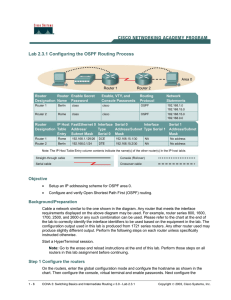
Lab 2.3.1 Configuring the OSPF Routing Process Objective
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
... In order to find out exactly how the router is configured, look at the interfaces. This will identify what type and how many interfaces the router has. There is no way to effectively list all of the combinations of configurations for each router class. What is provided are the identifiers for the po ...
On-Demand Monitoring of Protocol
... Receiving a PATH-ERROR message from the network means admission has not been granted and the sender can repeat admission requests at the rate specified by the user. In decentralized admission control the PATH message will be relayed to all the necessary parties along the route until it reaches the r ...
... Receiving a PATH-ERROR message from the network means admission has not been granted and the sender can repeat admission requests at the rate specified by the user. In decentralized admission control the PATH message will be relayed to all the necessary parties along the route until it reaches the r ...
slides
... Community's Seventh Framework programme. This paper reflects only the authors' views and the Community is not liable for any use that may be made of the information contained therein. The contributions of colleagues from E3 consortium are hereby acknowledged. ...
... Community's Seventh Framework programme. This paper reflects only the authors' views and the Community is not liable for any use that may be made of the information contained therein. The contributions of colleagues from E3 consortium are hereby acknowledged. ...
Adaptive Coding and Packet Rates for TCP-Friendly VoIP Flows
... resource distribution among multiple flows and prevent a congestion collapse of the Internet [4]. Congestion control in the Internet is based on TCP or TCP-friendly transport protocols. It is known that the throughput of a TCP-like protocol scales linearly with the packet size [5]. Thus, the optimal ...
... resource distribution among multiple flows and prevent a congestion collapse of the Internet [4]. Congestion control in the Internet is based on TCP or TCP-friendly transport protocols. It is known that the throughput of a TCP-like protocol scales linearly with the packet size [5]. Thus, the optimal ...
Metro WDM Networks: Performance Comparison of , Senior Member, IEEE
... spreading of the control signals [21], or as an out-of-band control channel, e.g., by running a PSC in parallel to the AWG [8]. In our explanation of the basic principles of the MAC protocol in the AWG star, we focus on the out-of-band control channel; we refer the interested reader to [21] for deta ...
... spreading of the control signals [21], or as an out-of-band control channel, e.g., by running a PSC in parallel to the AWG [8]. In our explanation of the basic principles of the MAC protocol in the AWG star, we focus on the out-of-band control channel; we refer the interested reader to [21] for deta ...
Demystifying Layer 2 and Layer 3 VPNs
... 4.3 Business Features of Layer 2 and Layer 3 Services ................................................................................................................................................................... 37 4.3.1 Multi-point Any-to-Any Connectivity ..................................... ...
... 4.3 Business Features of Layer 2 and Layer 3 Services ................................................................................................................................................................... 37 4.3.1 Multi-point Any-to-Any Connectivity ..................................... ...
DHCP, DNS
... Far more complex to implement than BOOTP Most DHCP servers also offer BOOTP support Duration based leases is the fundamental addition in DHCP ...
... Far more complex to implement than BOOTP Most DHCP servers also offer BOOTP support Duration based leases is the fundamental addition in DHCP ...
5_atm
... path. Cells are always received in sequence. virtual connections Statistical multiplexing of cells. An ATM connection is by definition unidirectional. ATM supports higher layer service adaptation, and may support different degrees of Quality of Service (QoS) and traffic management (IP term: traffic ...
... path. Cells are always received in sequence. virtual connections Statistical multiplexing of cells. An ATM connection is by definition unidirectional. ATM supports higher layer service adaptation, and may support different degrees of Quality of Service (QoS) and traffic management (IP term: traffic ...
IMS_new_possibilities
... IMS Momentum The OMA (Open Mobile Alliance) “IMSinOMA” Requirements Document (RD) provides a single general use case which rationalizes IMS as the only globally standardized SIP-based architecture (to date) that addresses the needs of mobile operators in terms of session management, security, mob ...
... IMS Momentum The OMA (Open Mobile Alliance) “IMSinOMA” Requirements Document (RD) provides a single general use case which rationalizes IMS as the only globally standardized SIP-based architecture (to date) that addresses the needs of mobile operators in terms of session management, security, mob ...
Securing Cognitive Wireless Sensor Networks: A Survey Linköping University Post Print
... of common characteristics. They consist of miniature devices, called motes or sensors that are severe resource constrained devices in terms of memory, processing, and energy [32, 33]. They usually do not perform any computation on the data they collect; they just forward this information to much mor ...
... of common characteristics. They consist of miniature devices, called motes or sensors that are severe resource constrained devices in terms of memory, processing, and energy [32, 33]. They usually do not perform any computation on the data they collect; they just forward this information to much mor ...
User Manual - AirStation WHR-HP-G54 High-Power
... You may also wish to contact your ISP to ask if other information, such as global IP address, subnet mask address, default gateway address, DNS server address, or PPPoE parameters, is necessary to access your internet connection. Write down any necessary information that your ISP requires for connec ...
... You may also wish to contact your ISP to ask if other information, such as global IP address, subnet mask address, default gateway address, DNS server address, or PPPoE parameters, is necessary to access your internet connection. Write down any necessary information that your ISP requires for connec ...
DHCP, DNS
... Far more complex to implement than BOOTP Most DHCP servers also offer BOOTP support Duration based leases is the fundamental addition in DHCP ...
... Far more complex to implement than BOOTP Most DHCP servers also offer BOOTP support Duration based leases is the fundamental addition in DHCP ...
About This Guide
... respective boxes. (You should have an ISP PPPoE account.) The camera will get an IP address from the ISP as starting up. DNS IP Address: DNS (Domain Name System) server is an Internet service that translates domain names into IP addresses. Enter at least one DNS IP Address in this field. Dynamic ...
... respective boxes. (You should have an ISP PPPoE account.) The camera will get an IP address from the ISP as starting up. DNS IP Address: DNS (Domain Name System) server is an Internet service that translates domain names into IP addresses. Enter at least one DNS IP Address in this field. Dynamic ...
Dynamic Node Reconfiguration in a Parallel
... and yields finer-grained control over the distribution of work. It also serves as a basis for using application knowledge to balance the load at runtime, rather than simply to effect a static decomposition into component processes. In addition, the process-level approach will tend to perform poor] y ...
... and yields finer-grained control over the distribution of work. It also serves as a basis for using application knowledge to balance the load at runtime, rather than simply to effect a static decomposition into component processes. In addition, the process-level approach will tend to perform poor] y ...
Safely Harnessing Wide Area Surrogate Computing -or-
... network driver runs in the controller virtual machine domain, clients cannot circumvent WASCo’s network access controls even if they patch or reconfigure their guest OS kernel. WASCo’s basic network security mechanisms are built using off the shelf Linux tools. Linux supports sophisticated network ...
... network driver runs in the controller virtual machine domain, clients cannot circumvent WASCo’s network access controls even if they patch or reconfigure their guest OS kernel. WASCo’s basic network security mechanisms are built using off the shelf Linux tools. Linux supports sophisticated network ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.