IP: Addresses and Forwarding - RPI ECSE
... End System (ES) - Network Host or workstation Network Service Access Point (NSAP) - Network Layer Address Subnetwork Point of attachment (SNPA) - Datalink interface Packet data Unit (PDU) - Analogous to IP Packet Link State PDU (LSP) - Routing information packet Level 1 and Level 2 – Area 0 and lowe ...
... End System (ES) - Network Host or workstation Network Service Access Point (NSAP) - Network Layer Address Subnetwork Point of attachment (SNPA) - Datalink interface Packet data Unit (PDU) - Analogous to IP Packet Link State PDU (LSP) - Routing information packet Level 1 and Level 2 – Area 0 and lowe ...
Chapter 8: Advanced Routing Protocols
... – Allow EIGRP to discover neighbors and keep track of their status – EIGRP must be able to keep updates bounded, sent only to those peers that need the information – EIGRP must build a neighbor table of directly connected peers CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
... – Allow EIGRP to discover neighbors and keep track of their status – EIGRP must be able to keep updates bounded, sent only to those peers that need the information – EIGRP must build a neighbor table of directly connected peers CCNA Guide to Cisco Networking Fundamentals, Fourth Edition ...
An Analysis of Fault Isolation in Multi
... 1. It is important to locate the fault in a network. 2. Little work has been done for fault isolation even in detection in multi-source multicast. 3. In multi-source multicast fault isolation, message complexity is main concern. 4. One candidate approach is a group-based architecture to locate the f ...
... 1. It is important to locate the fault in a network. 2. Little work has been done for fault isolation even in detection in multi-source multicast. 3. In multi-source multicast fault isolation, message complexity is main concern. 4. One candidate approach is a group-based architecture to locate the f ...
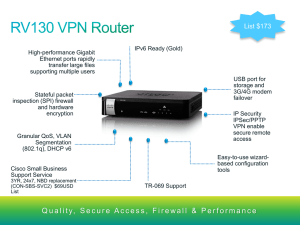
Cisco RV130/RV130W Product Overview
... Allows the business to control access to files and applications, as well as enabling secure guest access Intuitive, browser-based device manager with support for the Cisco FindIT Network Discovery Tool ...
... Allows the business to control access to files and applications, as well as enabling secure guest access Intuitive, browser-based device manager with support for the Cisco FindIT Network Discovery Tool ...
Cisco Nexus 3048 Switch Product Overview
... The Cisco Nexus® 3048 Switch (Figure 1) is a line-rate Gigabit Ethernet top-of-rack (ToR) switch and is part of the Cisco Nexus 3000 Series Switches portfolio. The Cisco Nexus 3048, with its compact one-rack-unit (1RU) form factor and integrated Layer 2 and 3 switching, complements the existing Cisc ...
... The Cisco Nexus® 3048 Switch (Figure 1) is a line-rate Gigabit Ethernet top-of-rack (ToR) switch and is part of the Cisco Nexus 3000 Series Switches portfolio. The Cisco Nexus 3048, with its compact one-rack-unit (1RU) form factor and integrated Layer 2 and 3 switching, complements the existing Cisc ...
ARCAT spec 262600 2009-9-15
... this information, are responsible for ensuring the acceptability of each application and appropriate use of the guidelines. In no event will Rockwell Automation be liable for misuse, misapplication or reliance on these guidelines in connection with any specific application. Rockwell Automation also ...
... this information, are responsible for ensuring the acceptability of each application and appropriate use of the guidelines. In no event will Rockwell Automation be liable for misuse, misapplication or reliance on these guidelines in connection with any specific application. Rockwell Automation also ...
Peer
... •The rendezvous protocol defines how a peer can subscribe or be a subscriber to a propagation service allowing larger communities to form • A rendezvous nodes’ scope is a peer group • e.g. the rendezvous protocol is used by the peer resolver protocol and by the pipe binding protocol in order to prop ...
... •The rendezvous protocol defines how a peer can subscribe or be a subscriber to a propagation service allowing larger communities to form • A rendezvous nodes’ scope is a peer group • e.g. the rendezvous protocol is used by the peer resolver protocol and by the pipe binding protocol in order to prop ...
PoolStatus_MZ - Indico
... • New layout of ETICS Web Application featuring the IPv6 check-box is being developed and will be deployed as part of Release v1.2 (to be confirmed) • Etics client with the -ipv6 switch is already available and will be deployed as part of Release v1.2 • IPv6 plug-in results will be presented by Albe ...
... • New layout of ETICS Web Application featuring the IPv6 check-box is being developed and will be deployed as part of Release v1.2 (to be confirmed) • Etics client with the -ipv6 switch is already available and will be deployed as part of Release v1.2 • IPv6 plug-in results will be presented by Albe ...
Alberto Santoro: Digital Divide Executive Report Outline to the ICFA
... c. Universities around the world have been engaged in the use of the Internet (including advanced Internet private networks) for some time now. Students around the world are engaged in attending courses across many scientific domains. Many of these courses are now being developed as interactive expe ...
... c. Universities around the world have been engaged in the use of the Internet (including advanced Internet private networks) for some time now. Students around the world are engaged in attending courses across many scientific domains. Many of these courses are now being developed as interactive expe ...
Primitives for Active Internet Topology Mapping
... probe. (It is not a problem if an edge is bi-directional, which for the interface-level graph should occur only as outliers.) The ISC scheme iteratively selects paths, and sub-paths, from the directed interface-level topology of the previous round, such that packets would probe interfaces that are n ...
... probe. (It is not a problem if an edge is bi-directional, which for the interface-level graph should occur only as outliers.) The ISC scheme iteratively selects paths, and sub-paths, from the directed interface-level topology of the previous round, such that packets would probe interfaces that are n ...
CS-TR-05-02 - Michigan Technological University
... characteristics such as administrative ease, ease of deployment and self-organization. Unstructured P2P networks however, pose significant challenges for anonymous communication protocols. An example of this kind of network is the Gnutella file sharing system, which is known to consume high bandwidt ...
... characteristics such as administrative ease, ease of deployment and self-organization. Unstructured P2P networks however, pose significant challenges for anonymous communication protocols. An example of this kind of network is the Gnutella file sharing system, which is known to consume high bandwidt ...
Auditing a Windows 2000 Advanced Server
... Incorrect configuration of network interfaces could increase internet and system ...
... Incorrect configuration of network interfaces could increase internet and system ...
pptx
... Some cloud companies are focused on Internet of Things scenarios that need DHTs in a WAN. Content hosting companies like Akamai often have a decentralized pull infrastructure and use a WAN overlay to find content (to avoid asking for the same thing again and again from the origin servers) Puzzle: No ...
... Some cloud companies are focused on Internet of Things scenarios that need DHTs in a WAN. Content hosting companies like Akamai often have a decentralized pull infrastructure and use a WAN overlay to find content (to avoid asking for the same thing again and again from the origin servers) Puzzle: No ...
Slide 1
... roam from mobile to fixed networks = “FMC” Messaging services for 2.0/2.5/3G networks • Capacity relief for core SS7 network • network optimization by utilizing broadband data ...
... roam from mobile to fixed networks = “FMC” Messaging services for 2.0/2.5/3G networks • Capacity relief for core SS7 network • network optimization by utilizing broadband data ...
IP Multicast
... •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. •Redundant reception by many hosts. 2. Link-layer (Ethernet) multicast •Requires ...
... •IP multicast packet is encapsulated in an Ethernet broadcast frame and transmitted on the bus. •Every host picks up the Ethernet frame and does filtering at the IP layer to decide whether to keep or discard the frame. •Redundant reception by many hosts. 2. Link-layer (Ethernet) multicast •Requires ...
Chapter 1 - Introduction
... Anycast addressing was originally known as cluster addressing – The motivation for such addressing arises from a desire to allow replication of services • For example, a corporation that offers a service over the network assigns an anycast address to several computers that provide the service • When ...
... Anycast addressing was originally known as cluster addressing – The motivation for such addressing arises from a desire to allow replication of services • For example, a corporation that offers a service over the network assigns an anycast address to several computers that provide the service • When ...
pdf
... Some cloud companies are focused on Internet of Things scenarios that need DHTs in a WAN. Content hosting companies like Akamai often have a decentralized pull infrastructure and use a WAN overlay to find content (to avoid asking for the same thing again and again from the origin servers) Puzzle: No ...
... Some cloud companies are focused on Internet of Things scenarios that need DHTs in a WAN. Content hosting companies like Akamai often have a decentralized pull infrastructure and use a WAN overlay to find content (to avoid asking for the same thing again and again from the origin servers) Puzzle: No ...
23.22
... 3 or greater indicates TSG approved document under change control. y the second digit is incremented for all changes of substance, i.e. technical enhancements, corrections, updates, etc. z the third digit is incremented when editorial only changes have been incorporated in the document. ...
... 3 or greater indicates TSG approved document under change control. y the second digit is incremented for all changes of substance, i.e. technical enhancements, corrections, updates, etc. z the third digit is incremented when editorial only changes have been incorporated in the document. ...
Border Gateway Protocol (BGP4)
... • Uses the routing table built by routing protocols • Performs the lookup to find next-hop and outgoing interface • Switches the packet with new encapsulation as per the outgoing interface ...
... • Uses the routing table built by routing protocols • Performs the lookup to find next-hop and outgoing interface • Switches the packet with new encapsulation as per the outgoing interface ...
Alcatel-Lucent OmniAccess 5510
... Half-rack width or desktop deployment options with fan-less design. ...
... Half-rack width or desktop deployment options with fan-less design. ...
RIP version 1
... Default Route and RIPv1 Propagating the Default Route in RIPv1 Default-information originate command – This command is used to specify that the router is to originate default information, by propagating the static default route in RIP update ...
... Default Route and RIPv1 Propagating the Default Route in RIPv1 Default-information originate command – This command is used to specify that the router is to originate default information, by propagating the static default route in RIP update ...
RIP version 1
... Default Route and RIPv1 Propagating the Default Route in RIPv1 Default-information originate command – This command is used to specify that the router is to originate default information, by propagating the static default route in RIP update ...
... Default Route and RIPv1 Propagating the Default Route in RIPv1 Default-information originate command – This command is used to specify that the router is to originate default information, by propagating the static default route in RIP update ...
Inferring Subnets in Router-level Topology Collection Studies
... though a given set of IP addresses can map to a, say, candidate /29 subnet, there may not be a corresponding real /29 subnet in the underlying network among these IP addresses. Instead, the addresses may belong to two separate /30 subnets in the Internet. Similarly, the candidate /29 subnet may be p ...
... though a given set of IP addresses can map to a, say, candidate /29 subnet, there may not be a corresponding real /29 subnet in the underlying network among these IP addresses. Instead, the addresses may belong to two separate /30 subnets in the Internet. Similarly, the candidate /29 subnet may be p ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.