PPT_ch10
... Earlier and less sophisticated than PPP Can only carry IP packets Requires significant amount of setup Does not support data encryption Asynchronous transmission ...
... Earlier and less sophisticated than PPP Can only carry IP packets Requires significant amount of setup Does not support data encryption Asynchronous transmission ...
Net Mgmt ch7.1
... •Out-of-band management occurs when different paths are provided for network management data flows and user traffic flows. •allowing the management system to continue to monitor the network during most network events, even when such events disable the network. •Can allow monitoring portions of the n ...
... •Out-of-band management occurs when different paths are provided for network management data flows and user traffic flows. •allowing the management system to continue to monitor the network during most network events, even when such events disable the network. •Can allow monitoring portions of the n ...
Introduction of IMS for 3G Voice Services and Migration
... DOCOMO’s SEN (Service Enabler Network) Concept Provide a variety of services to satisfy various user needs with timely manner. • SEN (Service Enabler Network) is service provision platform on top of IMS Core. • Enabler is the piece of service function that can be commonly used by multiple services. ...
... DOCOMO’s SEN (Service Enabler Network) Concept Provide a variety of services to satisfy various user needs with timely manner. • SEN (Service Enabler Network) is service provision platform on top of IMS Core. • Enabler is the piece of service function that can be commonly used by multiple services. ...
last draft
... switching decisions can be based on many factors including the matching of packet headers, ingress interface that a packet arrives on, or even deep packet inspection for handling higher-level protocols. The switching silicon commonly used in COTS Ethernet switches uses different types of forwarding ...
... switching decisions can be based on many factors including the matching of packet headers, ingress interface that a packet arrives on, or even deep packet inspection for handling higher-level protocols. The switching silicon commonly used in COTS Ethernet switches uses different types of forwarding ...
Computer Networks - IESL e
... 3.5 In Idle ARQ method, if any of the ACK frames (acknowledgements) or NAK frames (negative acknowledgements) is lost in the media due to noise or any other reason, transmission comes to a hold where transmitter and receiver both are waiting for each others’ transmissions. What are the methods used ...
... 3.5 In Idle ARQ method, if any of the ACK frames (acknowledgements) or NAK frames (negative acknowledgements) is lost in the media due to noise or any other reason, transmission comes to a hold where transmitter and receiver both are waiting for each others’ transmissions. What are the methods used ...
QoS in Converged Networks
... groom, inspect, or route traffic. • Layer 3 switching accomplishes some router-like activities: queuing, routing, and packetinspection. • It can be used to shape the traffic on the data link based on each packet’s • characteristics. • For example, it’s possible to drop all non-voice traffic by filte ...
... groom, inspect, or route traffic. • Layer 3 switching accomplishes some router-like activities: queuing, routing, and packetinspection. • It can be used to shape the traffic on the data link based on each packet’s • characteristics. • For example, it’s possible to drop all non-voice traffic by filte ...
Policy based Management of Content Distribution
... Our assumption is that the CDSP proxies may be located throughout the world, and some of them may be subject to regulations that prevent them from caching specific types of content. Therefore, a policy action must be able to restrict the caching function to be performed only at specific sites. As an ...
... Our assumption is that the CDSP proxies may be located throughout the world, and some of them may be subject to regulations that prevent them from caching specific types of content. Therefore, a policy action must be able to restrict the caching function to be performed only at specific sites. As an ...
ppt - NOISE
... • Query is sent to LAN’s broadcast MAC address • Each host or router has an ARP table – Checks IP address of query against its IP address – Replies with ARP address if there is a match Potential problems with this approach? ...
... • Query is sent to LAN’s broadcast MAC address • Each host or router has an ARP table – Checks IP address of query against its IP address – Replies with ARP address if there is a match Potential problems with this approach? ...
Lecture Note 4
... Internet transport protocol “best effort” service, UDP segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
... Internet transport protocol “best effort” service, UDP segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
Active Networking
... • An EE is installed in a node by/under management control. • AAs are dynamically deployed and may be transient or persistant. • Expect: 1 nodeOS, a few EEs, many AAs in each active node. ...
... • An EE is installed in a node by/under management control. • AAs are dynamically deployed and may be transient or persistant. • Expect: 1 nodeOS, a few EEs, many AAs in each active node. ...
How LAN Switches Work
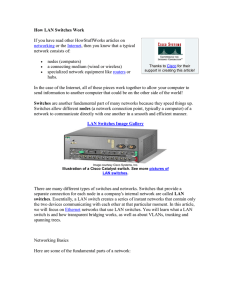
... You can see that a switch has the potential to radically change the way nodes communicate with each other. But you may be wondering what makes it different from a router. Switches usually work at Layer 2 (Data or Datalink) of the OSI Reference Model, using MAC addresses, while routers work at Layer ...
... You can see that a switch has the potential to radically change the way nodes communicate with each other. But you may be wondering what makes it different from a router. Switches usually work at Layer 2 (Data or Datalink) of the OSI Reference Model, using MAC addresses, while routers work at Layer ...
The Campus as key to Internet2 Engineering
... Internet2 networking ® 80 Mb/s But user expectations and experiences vary widely ...
... Internet2 networking ® 80 Mb/s But user expectations and experiences vary widely ...
Performance Evaluation ofIEEE802.11g WLANsUsing OPNET
... moving nodes or stations that can communicate with each other over the air in a geographically limited area [6]. Two configurations are specified in the standard: ad-hoc and infrastructure. The ad-hoc mode is also referred to as the peer-to-peer mode or an Independent Basic Service Set (IBSS) as ill ...
... moving nodes or stations that can communicate with each other over the air in a geographically limited area [6]. Two configurations are specified in the standard: ad-hoc and infrastructure. The ad-hoc mode is also referred to as the peer-to-peer mode or an Independent Basic Service Set (IBSS) as ill ...
PPT - Protocol Engineering and Technology Unit
... systems. To understand the basics of a multimedia communication system. To illustrate multimedia networks. ...
... systems. To understand the basics of a multimedia communication system. To illustrate multimedia networks. ...
H3C SR8800 10G Core Routers
... When building a MAN or campus network, the full-mesh topology on the backbone requires a large volume of link resources and a high cost for operation and maintenance. In this regard, networking using RPR is a better solution. RPR not only provides the rapid self-healing resilient protection mechanis ...
... When building a MAN or campus network, the full-mesh topology on the backbone requires a large volume of link resources and a high cost for operation and maintenance. In this regard, networking using RPR is a better solution. RPR not only provides the rapid self-healing resilient protection mechanis ...
O A RIGINAL RTICLE
... network similar to OADMs and OXCs (Tzanakaki et al., 2003). OXADMs consists of three main subsystems; a wavelength selective demultiplexer, a switching subsystem and a wavelength multiplexer. There are eight ports for add and drop functions which are controlled by four lines of thermal-optical switc ...
... network similar to OADMs and OXCs (Tzanakaki et al., 2003). OXADMs consists of three main subsystems; a wavelength selective demultiplexer, a switching subsystem and a wavelength multiplexer. There are eight ports for add and drop functions which are controlled by four lines of thermal-optical switc ...
The Design and Implementation of an intentional naming system
... INRs self-configure to form a spanning tree overlaynetwork over UDP tunnels INR-pings send a small name between INRs and measure the time it takes to process this message and get a response Domain Space Resolver (DSR) keeps track of all INRs in the system INS- February 2002 ...
... INRs self-configure to form a spanning tree overlaynetwork over UDP tunnels INR-pings send a small name between INRs and measure the time it takes to process this message and get a response Domain Space Resolver (DSR) keeps track of all INRs in the system INS- February 2002 ...
Chapter 5 outline
... A’s data link layer sends frame R’s data link layer receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s physical layer address R creates frame containing A-to-B IP datagram sends to B ...
... A’s data link layer sends frame R’s data link layer receives frame R removes IP datagram from Ethernet frame, sees its destined to B R uses ARP to get B’s physical layer address R creates frame containing A-to-B IP datagram sends to B ...
What is the Grid?
... • Technical inability to provision individual (per-flow) QoS – “normal“ Internet users • unlimited number of flows come and go at any time • heterogeneous traffic mix – Grid users • number of members in a “virtual team“ may be limited • clear distinction between bulk data transfer and SOAP messages ...
... • Technical inability to provision individual (per-flow) QoS – “normal“ Internet users • unlimited number of flows come and go at any time • heterogeneous traffic mix – Grid users • number of members in a “virtual team“ may be limited • clear distinction between bulk data transfer and SOAP messages ...
ppt
... unusually active, the activity required at the end-point to deal with the broadcasts could diminish performance. ...
... unusually active, the activity required at the end-point to deal with the broadcasts could diminish performance. ...
acba0bdb38899c8
... max. hop count value to avoid counting to infinity) and send its routing table to B after the periodic interval. - Before B sends its periodic update to C , router C sent its routing table to B containing a path to 10.0.0.0 with a better metric so B think that 10.0.0.0 can be reached by C while C de ...
... max. hop count value to avoid counting to infinity) and send its routing table to B after the periodic interval. - Before B sends its periodic update to C , router C sent its routing table to B containing a path to 10.0.0.0 with a better metric so B think that 10.0.0.0 can be reached by C while C de ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.