algorithm
... IRB Decision Tree Should I submit to the medical IRB (HSR) or the social and behavioral IRB (SBS)? Does this protocol involve medically invasive procedures? ...
... IRB Decision Tree Should I submit to the medical IRB (HSR) or the social and behavioral IRB (SBS)? Does this protocol involve medically invasive procedures? ...
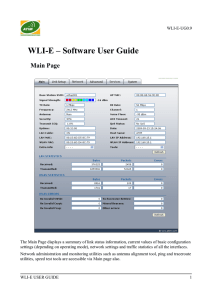
WLI-E – Software User Guide
... Transmit CCQ: This is an index of which evaluates the wireless Client Connection Quality. It takes into account transmit errors, latency, and throughput while evaluating the ratio of successfully transmitted packets against the re-transmitted ones and taking into account current rate ratio against t ...
... Transmit CCQ: This is an index of which evaluates the wireless Client Connection Quality. It takes into account transmit errors, latency, and throughput while evaluating the ratio of successfully transmitted packets against the re-transmitted ones and taking into account current rate ratio against t ...
FCTC_Zamer_iscsi
... iFCP is a gateway-to-gateway protocol for implementing a fibre channel fabric over a TCP/IP transport Traffic between fibre channel devices is routed and switched by TCP/IP network The iFCP layer maps Fibre Channel frames to a predetermined TCP connection for transport FC messaging and routing servi ...
... iFCP is a gateway-to-gateway protocol for implementing a fibre channel fabric over a TCP/IP transport Traffic between fibre channel devices is routed and switched by TCP/IP network The iFCP layer maps Fibre Channel frames to a predetermined TCP connection for transport FC messaging and routing servi ...
press release 01/2015_e - Deutschmann Automation
... The series is based on the established Protocol converter UNIGATE CL. In addition to RS232, RS485 and RS422 standard interfaces, a Fast Ethernet interface is also provided. After entering the network-specific data, such as IP address, the device is immediately ready for use for communication via TCP ...
... The series is based on the established Protocol converter UNIGATE CL. In addition to RS232, RS485 and RS422 standard interfaces, a Fast Ethernet interface is also provided. After entering the network-specific data, such as IP address, the device is immediately ready for use for communication via TCP ...
September 2012
... application might lose its relevance since there are implementations of IPv6 for sensor networks available, that allow an all-IP approach. 3.4 M2M Communication Networks (Network Domain) It covers the communications between the M2M Gateway(s) and M2M application(s), e.g. xDSL, LTE, WiMAX, and WLAN. ...
... application might lose its relevance since there are implementations of IPv6 for sensor networks available, that allow an all-IP approach. 3.4 M2M Communication Networks (Network Domain) It covers the communications between the M2M Gateway(s) and M2M application(s), e.g. xDSL, LTE, WiMAX, and WLAN. ...
Pinpointing connectivity despite hidden nodes within stimulus-driven networks Duane Q. Nykamp 兲
... we have ignored the activity of all nodes except for one 共setting Rs̃k,i = 0 for s̃ ⫽ s兲. Since, of course, the single-node model will have different parameters, we denoted the change by removing the bar over the probability distribution. We assume that the HAH model chosen for 共6兲 is an identifiabl ...
... we have ignored the activity of all nodes except for one 共setting Rs̃k,i = 0 for s̃ ⫽ s兲. Since, of course, the single-node model will have different parameters, we denoted the change by removing the bar over the probability distribution. We assume that the HAH model chosen for 共6兲 is an identifiabl ...
Taxonomy of communication networks
... - reservation/dedication (aka circuit-switching) and - no reservation (aka packet switching) ...
... - reservation/dedication (aka circuit-switching) and - no reservation (aka packet switching) ...
Socket Programming
... domain: integer, communication domain • e.g., PF_INET (IPv4 protocol) – typically used ...
... domain: integer, communication domain • e.g., PF_INET (IPv4 protocol) – typically used ...
Socket Programming
... domain: integer, communication domain • e.g., PF_INET (IPv4 protocol) – typically used ...
... domain: integer, communication domain • e.g., PF_INET (IPv4 protocol) – typically used ...
Lec08-network1
... microns) uses laser diodes, 1-5 Gbits/s for 100s kms – Less reliable and more expensive, and restrictions on bending – Cost, bandwidth, and distance of single-mode fiber affected by power of the light source, the sensitivity of the light detector, and the attenuation rate (loss of optical signal str ...
... microns) uses laser diodes, 1-5 Gbits/s for 100s kms – Less reliable and more expensive, and restrictions on bending – Cost, bandwidth, and distance of single-mode fiber affected by power of the light source, the sensitivity of the light detector, and the attenuation rate (loss of optical signal str ...
Chapter 1 - Introduction
... opposite direction of routing traffic. For example – suppose an AS owned by ISP1 contains network N • Before traffic can arrive destined for N, ISP1 must advertise a route to N • That is, when the routing advertisement flows out, data will begin to flow in ...
... opposite direction of routing traffic. For example – suppose an AS owned by ISP1 contains network N • Before traffic can arrive destined for N, ISP1 must advertise a route to N • That is, when the routing advertisement flows out, data will begin to flow in ...
Symantec Enterprise Firewalls
... – Actively blocks email messages by subject line text, file name attachment type, and message size. – If a virus is found, the file is either repaired or dropped. – All viruses are logged and a message is added to mail messages indicating that a virus was found and the attachment was deleted. ...
... – Actively blocks email messages by subject line text, file name attachment type, and message size. – If a virus is found, the file is either repaired or dropped. – All viruses are logged and a message is added to mail messages indicating that a virus was found and the attachment was deleted. ...
C07-Wireless_LANs_f
... station must additionally wait a random back-off time (collision avoidance, multiple of slot-time) if another station occupies the medium during the back-off time of the station, the back-off timer stops (fairness) ...
... station must additionally wait a random back-off time (collision avoidance, multiple of slot-time) if another station occupies the medium during the back-off time of the station, the back-off timer stops (fairness) ...
Trust management in wireless sensor networks
... The range of applications of wireless sensor networks is so wide that it tends to invade our every day life. In the future, a sensor network will survey our health, our home, the roads we follow, the office or the industry we work in or even the aircrafts we use, in an attempt to enhance our safety. ...
... The range of applications of wireless sensor networks is so wide that it tends to invade our every day life. In the future, a sensor network will survey our health, our home, the roads we follow, the office or the industry we work in or even the aircrafts we use, in an attempt to enhance our safety. ...
Chapter 7
... 86. Can a device obtain its IPv6 global unicast address dynamically and also be configured with multiple static IPv6 addresses on the same interface? ...
... 86. Can a device obtain its IPv6 global unicast address dynamically and also be configured with multiple static IPv6 addresses on the same interface? ...
6DISS: IPv6 Dissemination and Exploitation
... • Assign /56 address prefix to each school network • School prefixes are aggregated into /48 prefixes – Address allocation follows the hierarchical structure of the GSN – One /48 prefix is advertised by each of the 8 core nodes – Assign an extra /48 prefix for the backbone ...
... • Assign /56 address prefix to each school network • School prefixes are aggregated into /48 prefixes – Address allocation follows the hierarchical structure of the GSN – One /48 prefix is advertised by each of the 8 core nodes – Assign an extra /48 prefix for the backbone ...
Performance Management (Best Practices)
... • With an increasing number of network devices deployed, it is critical to be able to accurately identify the location of a network device. • This location information should provide a detailed description meaningful to those tasked with dispatching resources when a network problem occurs. • To expe ...
... • With an increasing number of network devices deployed, it is critical to be able to accurately identify the location of a network device. • This location information should provide a detailed description meaningful to those tasked with dispatching resources when a network problem occurs. • To expe ...
T R ECHNICAL ESEARCH
... This document describes the Adhoc Multicast Routing Protocol (AMRoute), which enables the use of IP Multicast in MANETs. Existing multicast protocols ([1], [2], [3]) do not work well in MANETs as the frequent tree reorganization can cause excessive signaling overhead and frequent loss of datagrams. ...
... This document describes the Adhoc Multicast Routing Protocol (AMRoute), which enables the use of IP Multicast in MANETs. Existing multicast protocols ([1], [2], [3]) do not work well in MANETs as the frequent tree reorganization can cause excessive signaling overhead and frequent loss of datagrams. ...
TCP - Andrzej Duda
... additional means are taken, it results in a large number of small packets to be sent, with no benefit to the receiver since anyhow it cannot read them fast enough. The (new) TCP specification mandates that sender and receiver should implement SWS avoidance. SWS avoidance at the receiver simply force ...
... additional means are taken, it results in a large number of small packets to be sent, with no benefit to the receiver since anyhow it cannot read them fast enough. The (new) TCP specification mandates that sender and receiver should implement SWS avoidance. SWS avoidance at the receiver simply force ...
COMP680E by M. Hamdi
... • Each PHB is represented by a 6-bit value called DSCP • All packets with the same code points are referred to as a behavior aggregate (BA) and they receive the same ...
... • Each PHB is represented by a 6-bit value called DSCP • All packets with the same code points are referred to as a behavior aggregate (BA) and they receive the same ...
Overlay networks
... Multicast packets do not impose as high a rate of bandwidth utilization as unicast packets, so there is a greater possibility that they will arrive almost simultaneously at the receivers ...
... Multicast packets do not impose as high a rate of bandwidth utilization as unicast packets, so there is a greater possibility that they will arrive almost simultaneously at the receivers ...
Document
... chatting between two users is P2P centralized service: client presence detection/location • user registers its IP address with central server when it comes online • user contacts central server to find IP addresses of buddies Network services ...
... chatting between two users is P2P centralized service: client presence detection/location • user registers its IP address with central server when it comes online • user contacts central server to find IP addresses of buddies Network services ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.